жңҖеҫҢжӣҙж–°: 2020-07-20
зӣ®йҢ„
- L2TP
- Auto connect VPN Setting
- Service
- NAT-T
- Debug
L2TP д»Ӣзҙ№
The entire L2TP packet, including payload and L2TP header,
is sent within a User Datagram Protocol (1701/UDP) datagram.
It does not provide any encryption or confidentiality by itself. (жүҖд»Ҙжңү PPP/L2TP)
Rather, it relies on an encryption protocol that it passes within the tunnel to provide privacy.(L2TP/IPsec)
LAC (L2TP Access Concentrator)
||
\/
LNS (L2TP Network Server)To be useful for networking, higher-level protocols are then run through the L2TP tunnel.
It is common to carry PPP sessions within an L2TP tunnel.
The traffic for each session is isolated by L2TP, so it is possible to set up multiple virtual networks across a single tunnel.
* control packets or data packets
L2TP/IPsec Startup Step
1. SA-IKE(500/UDP)
2. ESP in transport mode (50/IP)
3. Negotiation and establishment of L2TP
Windows Auto connect VPN Setting
Win7:
Setup Step
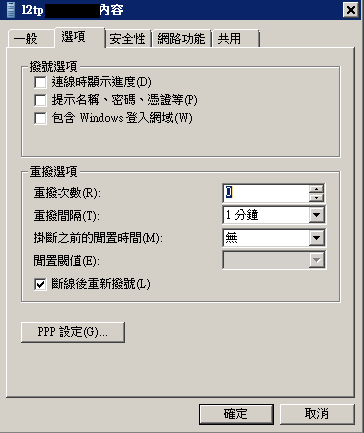
[1] Options tab -> uncheck the
- Display progress while connecting
- Prompt for username
- retry: 0
[2] taskschd.msc -> Create task
Give the task a name .e.g "Auto-start VPN"
Select "Run whether user is logged in or not"
Select "Run with the highest privileges"
"triggers tab" -> click "New" -> Select "At Startup"
Click on the "Actions tab" -> click New
program script box: "C:\Windows\System32\rasphone.exe"
optional arguments: "-d connectionname" (without the quotes !!)
Click on the Conditions tab and clear any boxes which are checked.
Click OK. ALL DONE
Service
Win7:
Service: PolicyAgent
Manages IP security policy and starts the ISAKMP/Oakley (IKE) and the IP security driver.
еҰӮжһңжӯӨ Service Stop дәҶ, йӮЈжңғ connect е””еҲ° VPN
Start
net start PolicyAgent
NAT-T
Win7
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\PolicyAgent
AssumeUDPEncapsulationContextOnSendRule [DWORD (32-bit)]
- 0 cannot establish security associations with servers that are located behind NAT devices. (Default)
- 1 establish security associations with servers that are located behind NAT devices
- 2 establish security associations when both the server and the client are behind NAT devices
Debug
Client -> Server
# Debug: On Server
# x.x.x.x = Client IP
tcpdump -i wan esp # жІ’жңү traffic зҡ„
tcpdump -i wan udp port 500 and src x.x.x.x # connection startup жҷӮжңү package (isakmp)
tcpdump -i wan udp port 4500 and src x.x.x.x # жүҖжңү traffic йғҪдҝӮиЎҢжӯӨ port (ipsec-nat-t)
![йҰ–й Ғ Logo ¶гБВ Keith і]ӯp !!](/themes/mytheme/logo.png)