жңҖеҫҢжӣҙж–°: 2018-08-31
д»Ӣзҙ№
Hareware
- Port: 8 GbE
- Power Supply: 12V, 5A
- Ram: 4 GB
- CPU: Atom C2000 series 1250 MHz, 1 CPU (4 cores)
- SSD: 8000MB
Speed
- иіҮе®үйҳІиӯ·еҗһеҗҗйҮҸ: 125 MbpsпјҲжҮүз”ЁзЁӢејҸжҺ§з®ЎиҲҮIPSпјү
- йҳІзҒ«зүҶеҗһеҗҗйҮҸ: 750 Mbps
- VPNеҗһеҗҗйҮҸ: 100 Mbps
OS
ASA 5506-X ships with either ASA or Firepower Threat Defense software preinstalled.
Firepower жҺҲж¬Ҡ=е№ҙиІ» (йҒёиіј)
* еҝ…й ҲйҖҸйҒҺйЎҚеӨ–е»әзҪ®зҡ„Firepower Management CenterпјҲFMCпјүдјәжңҚеҷЁжүҚиғҪжҺ§з®Ў
Software License
Base or Security Plus license, depending on the version you ordered.
The Security Plus license provides more firewall connections, VPN connections, failover capability, and VLANs.
It also comes pre-installed with the Strong Encryption (3DES/AES) license if you qualify for its use;
(this license is not available for some countries depending on United States export control policy)
AnyConnect Plus or Apex license, which allows AnyConnect VPN client connections.
ASA FirePOWER Licenses
Check Serial Number
Cisco IOS License
- Preinstalled License (Base License)
- Permanent License (Security Plus License)
- Time-Based Licenses
* The ASA 5506-X and ASA 5506W-X do not support time-based licenses
show version | grep Serial
Serial Number: ??????????
show version | grep Activation
Running Permanent Activation Key: 0x? 0x? 0x? 0x? 0x?
дёҚеҗҢ license зҡ„еҲҶеҲҘ
# е®ғеҖ‘жңғжңүдёҚеҗҢзҡ„еҠҹиғҪ, и·ҹж©ҹдҫҶжҳҜ "Base license"
show activation-key
Serial Number: ? Running Permanent Activation Key: ? ? ? ? ? Licensed features for this platform: Maximum Physical Interfaces : Unlimited perpetual Maximum VLANs : 5 perpetual Inside Hosts : Unlimited perpetual Failover : Disabled perpetual Encryption-DES : Enabled perpetual Encryption-3DES-AES : Enabled perpetual Carrier : Disabled perpetual AnyConnect Premium Peers : 2 perpetual AnyConnect Essentials : Disabled perpetual Other VPN Peers : 10 perpetual Total VPN Peers : 12 perpetual AnyConnect for Mobile : Disabled perpetual AnyConnect for Cisco VPN Phone : Disabled perpetual Advanced Endpoint Assessment : Disabled perpetual Shared License : Disabled perpetual Total TLS Proxy Sessions : 2 perpetual Botnet Traffic Filter : Disabled perpetual Cluster : Disabled perpetual This platform has a Base license. The flash permanent activation key is the SAME as the running permanent key.
Base License
- Firewall Conns (Concurrent): 20,000
- VPN Licenses: 10
- Failover: No support
- VLANs, Maximum: 5
Security Plus License (д»Јиҷҹ: ASA5506-SEC-PL) // иҰҒиІ·зҡ„, HK$3000@20180917
- ...
Input ASA 5506-X Sec. Plus Lic.
* The activation key is not stored in your configuration file
* The key is tied to the serial number of the device.
# Enter four-or-five-tuple activation-key
activation-key X X X X
# You must reboot it for the change to take effect in the running image.
reload
# Checking
show activation-key
... This platform has an ASA 5506 Security Plus license. The flash permanent activation key is the SAME as the running permanent key.
LED
Status - System operating status:
Green – Normal system function.
Amber – Critical alarm indicating one or more of the following:
Major failure of a hardware or software component.
Over-temperature condition.
Power voltage outside the tolerance range.
Active - Status of the failover pair:
Solid green – Failover pair operating normally. The LED is green always unless the ASA in an HA pair.
Amber – When the ASA is in an HA pair, the LED is amber for the Standby unit.
Unlit – Failover is not operational.
Link status (L):
Unlit – No link, or port is not in use.
Solid green – Link established.
Flashing green – Link activity.
Connection-speed status (S):
One blink every three seconds – 10 Mbps.
Two rapid blinks – 100 Mbps.
Three rapid blinks – 1000 Mbps.
USB Console Port
Two serial ports, a mini USB Type B, and a standard RJ-45 (8P8C),
are provided for management access via an external system.
Only one console port can be active at a time.
For Linux and Macintosh systems, no special driver is required.
For Windows systems, you must download and install a USB driver
(Cisco_usbconsole_driver_X_X_zip)
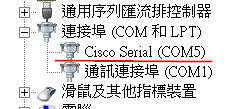
Windows
е®үиЈқ driver еҫҢ, жҸ’ USB Cable еҫҢеҮәзҸҫ Cisco Serial (COM5)
9600 baud 8 data bits no parity 1 stop bit no flow control
Linux
screen /dev/ttyACM0 9600
Reset button
A small recessed button that if pressed for longer than "three" seconds resets the ASA to its default “as-shipped” state following the next reboot.
However, the flash is not erased and no files are removed.
You can use the service sw-reset-button to disable the reset button. The default is enabled.
console output
Cryptochecksum: ? ? ? ? 4754 bytes copied in 0.260 secs *** *** --- START GRACEFUL SHUTDOWN --- *** *** Message to all terminals: *** *** SW Reset Button Pressed Shutting down isakmp Shutting down webvpn Shutting down sw-module Shutting down License Controller Shutting down File system *** *** --- SHUTDOWN NOW --- *** *** Message to all terminals: *** *** SW Reset Button Pressed Process shutdown finished Rebooting... (status 0x9)
First Time Deploy
outside GigabitEthernet 1/1 interface, IP address from DHCP
inside bridge group with GigabitEthernet 1/2 through 1/8 member interfaces
Management 1/1 interface
No ASA IP
FirePOWER IP: 192.168.1.2 (must set in FirePOWER)
Belongs to the ASA FirePOWER module;
The interface is Up, but otherwise unconfigured on the ASA.
Do not configure an IP address for this interface in the ASA configuration.
Only configure an IP address in the FirePOWER configuration.
You should consider this interface as completely separate from the ASA in terms of routing.
* assumes you want to use ASDM to manage the ASA FirePOWER Module. I
Default Login Info.
IP: IP: 192.168.1.1
Panel: https://192.168.1.1/admin
Default Login: NULL / NULL
Enable pass: NULL
Upgrade a Standalone Unit Using the CLI
# жҜҸеҖӢ Version зҡ„ ASA йғҪжңүе°ҚжҮү version зҡ„ ASDM (Compatibility)
ASA 9.9 -> ASDM 7.9 ASA 9.8 -> ASDM 7.8 ....
Download
Interim releases
They contain bug fixes which address specific issues found since the last Feature or Maintenance release.
# FileName # size 103.62 MB asa982-38-lfbff-k8.SPA # 14-JUN-2018 asa982-35-lfbff-k8.SPA # 23-MAY-2018 # asdm asdm-782-151.bin # 12-OCT-2017
Step
1. Upgrade the ASA Appliance
In privileged EXEC mode, copy the ASA software to flash memory.
i.e.
ciscoasa# copy http://192.168.1.177/asa982-38-lfbff-k8.SPA disk0:/
ciscoasa# copy ftp://cisco:[email protected]/asa991-smp-k8.bin disk0:/
2. Copy the ASDM image to flash memory.
i.e.
ciscoasa# copy http://192.168.1.177/asdm-782-151.bin disk0:/
ciscoasa# copy ftp://cisco:[email protected]/asdm-771791.bin disk0:/
3. Show current image
# IOS
show version | grep image
System image file is "disk0:/asa982-lfbff-k8.SPA"
# asdm image
show asdm image
Device Manager image file, disk0:/asdm-782.bin
4. Remove any existing boot image configurations
The ASA uses the images in the order listed;
if the first image is unavailable, the next image is used, and so on.
You cannot insert a new image URL at the top of the list; to specify the new image to be first,
you must remove any existing entries, and enter the image URLs in the order desired, according to the next steps.
ciscoasa# show running-config boot system
# жІ’жңү output
ciscoasa# configure terminal
ciscoasa(config)# no boot system disk0:/asa982-OLD-lfbff-k8.SPA
ciscoasa(config)# boot system disk0:/asa982-38-lfbff-k8.SPA
ciscoasa(config)# asdm image disk0:/asdm-782-151.bin
ciscoasa(config)# show bootvar
BOOT variable = disk0:/asa982-38-lfbff-k8.SPA Current BOOT variable = disk0:/asa982-38-lfbff-k8.SPA CONFIG_FILE variable = Current CONFIG_FILE variable =
ciscoasa# write memory
ciscoasa# reload
ASDM
Cisco ASDM can run as
- a local application (Java)
- a Java Web Start application (IE)
- start ASDM from command-line
* Default Lan IP: 192.168.1.1
start ASDM from command-line
1. fw allow jp2launcher.exe outgoing
2. C:\Program Files\Java\jre1.8.0_181\bin # asdm-782 need Java8
3. javaws.exe https://(ip or hostname to ASA)/admin/public/asdm.jnlp
Enable asdm on management interface
http server enable
http 192.168.8.0 255.255.255.0 management
Disable A ACL
To make an ACE inactive, use the inactive keyword.
To reenable it, enter the entire ACE without the inactive keyword.
This feature enables you to keep a record of an inactive ACE in your configuration to make reenabling easier.
i.e.
access-list outside_acl extended permit icmp any any time-exceeded inactive
Enable SSH By Console
ciscoasa(config)# crypto key generate rsa general-keys modulus 2048
ciscoasa(config)# username testuser password testpass
ciscoasa(config)# aaa authentication ssh console LOCAL
ciscoasa(config)# ssh timeout 30
ciscoasa(config)# ssh version 2
ciscoasa(config)# ssh key-exchange group dh-group14-sha1
ciscoasa(config)# ssh cipher integrity high
ciscoasa(config)# ssh cipher encryption high
ciscoasa(config)# ssh 192.168.1.177 255.255.255.255 inside_1
...
ciscoasa(config)# ssh 192.168.1.177 255.255.255.255 inside_7
ciscoasa(config)# write memory
timeout unit => minutes
Set "enable" Password
Get into the command line.
Type 'enable' to enter enable mode.
Type 'config t' .
Type 'enable password PaSsWoRd
ASA 5505 иіӘ 5506-X еҲҶеҲҘ
[1] еңЁ 5506-X дёҠ vlan иў« bridge-group еҸ–д»ЈдәҶ
bridge-group vs vlan
A bridge group is used on routers to join two (or more) router interfaces to a single broadcast domain.
A VLAN is used on switches to group switch ports into a single broadcast domain.
VNI Interface
Virtual Extensible LAN (VXLAN)
- VXLAN is a technology which allows overlaying a Layer 2 (L2) network over a Layer 3 (L3) underlay with use of any IP routing protocol.
- It uses MAC-in-UDP Encapsulation.
Virtual Tunnel Interface (VTI)
IP security (IPsec) virtual tunnel interfaces (VTIs) provide a routable interface type for terminating IPsec tunnels and an easy way to define protection between sites to form an overlay network.
IPsec VTIs simplify configuration of IPsec for protection of remote links, support multicast, and simplify network management and load balancing.
Object
show run object
object network apps1_lan_ip host 192.168.3.151 object network apps_network subnet 192.168.3.0 255.255.255.0
show run object in-line
object network apps1_lan_ip host 192.168.3.151 object network apps_network subnet 192.168.3.0 255.255.255.0
NAT
Version 9.8 дёҖе…ұжңүе…©зЁ® Nat жЁЎејҸ, еҲҶеҲҘжҳҜ
- network object NAT
All NAT rules that are configured as a parameter of a network object are considered to be network object NAT rules.
(You cannot create these rules for a group object)
- twice NAT.
Twice NAT lets you identify both the source and destination address in a single rule.
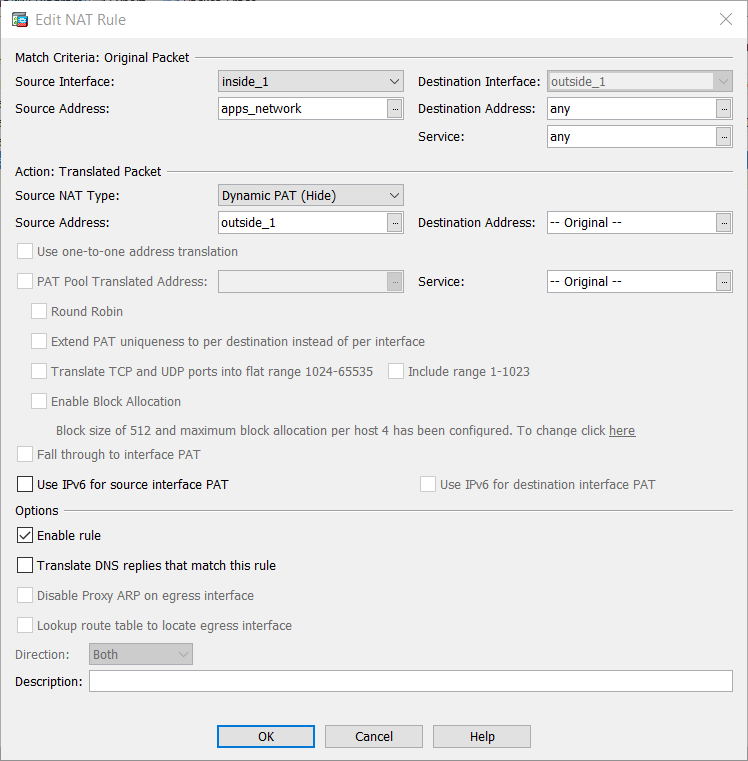
Outgoing NAT (Share Single IP)
inside hosts to share a single public address for translation
Use: Port Address Translation (PAT)
GUI
Equivalent CLI
wan:outside_1
lan:inside_1
i.e.
nat (inside_1,outside_1) source dynamic apps_network interface
и§ЈиӘӘ
# nat (real_ifc ,mapped_ifc ) source dynamic {real_obj | any }{mapped_obj [interface]} [description desc] [inactive]
real_ifc,mapped_ifc
Required for bridge group member interfaces.
interface
The interface keyword enables interface PAT fallback.
After the mapped IP addresses are used up,
then the IP address of the mapped interface is used.
you must configure a specific interface for the mapped_ifc
(You cannot specify interface when the mapped interface is a bridge group member)
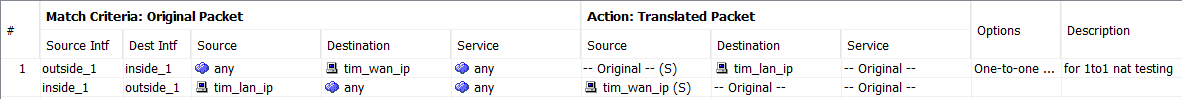
Static NAT
static NAT allows bidirectional connection initiation, both to and from the host (if an access rule exists that allows it)
wan --- 88.243(outside_1,inside_1) --- 3.178
i.e.
object network tim_lan_ip host 192.168.3.178 object network tim_wan_ip host 192.168.88.243 nat (outside_1,inside_1) source static any any destination static tim_wan_ip tim_lan_ip net-to-net description for 1to1 nat testing
- source static
- destination static
- net-to-net # For a one-to-one translation
GUI жңғжңүе…©жўқ Rule
access rule иҰҒз”Ё Lan IP
access-list outside_1_access_in_1 extended permit tcp any object tim_lan_ip eq www
Troubleshoot
- show conn addr IP
- syslog
- packet-tracer
- Capture Package
----------------
show conn
# connection in the firewall connection table (stateful firewall)
show conn address 198.168.3.178
TCP outside_1 192.168.88.177:64503 inside_1 192.168.3.178:80, idle 0:00:02, bytes 3021, flags UIOB TCP outside_1 192.168.88.177:64502 inside_1 192.168.3.178:80, idle 0:00:02, bytes 8220, flags UIOB TCP outside_1 192.168.88.177:64501 inside_1 192.168.3.178:80, idle 0:00:02, bytes 29084, flags UIOB TCP outside_1 192.168.88.177:64500 inside_1 192.168.3.178:80, idle 0:00:02, bytes 7645, flags UIOB TCP outside_1 192.168.88.177:64499 inside_1 192.168.3.178:80, idle 0:00:02, bytes 0, flags SaAB
# flag зҡ„ж„ҸжҖқ
show conn detail
# Inbound Connection
B - initial SYN from outside
...
# shows the state of all TCP connections through the ASA
show conn protocol tcp
Syslog
ASA(config)# show log | in 198.168.3.178
packet-tracer
# allows you to specify a simulated packet and see all of the various steps,
# checks, and functions that the firewall goes through when it processes traffic.
client(outside_1) ASA server(inside_1)
.88.177:1234 -> .88.234 -> 198.168.3.178
i.e. 1
packet-tracer input outside_1 tcp 192.168.88.177 1234 192.168.88.243 http
Result: input-interface: outside_1 input-status: up input-line-status: up output-interface: inside_1 output-status: up output-line-status: up Action: allow
i.e. 2
packet-tracer input outside_1 tcp 192.168.88.177 1234 192.168.88.243 https
Phase: 1 Type: UN-NAT Subtype: static Result: ALLOW Config: nat (outside_1,inside_1) source static any any destination static tim_wan_ip tim_lan_ip net-to-net description for 1to1 nat testing Additional Information: NAT divert to egress interface inside_1 Untranslate 192.168.88.243/443 to 192.168.3.178/443 Phase: 2 Type: ROUTE-LOOKUP Subtype: Resolve Egress Interface Result: ALLOW Config: Additional Information: found next-hop 192.168.88.177 using egress ifc outside_1 Phase: 3 Type: ACCESS-LIST Subtype: Result: DROP Config: Implicit Rule Additional Information: Result: input-interface: outside_1 input-status: up input-line-status: up output-interface: inside_1 output-status: up output-line-status: up Action: drop Drop-reason: (acl-drop) Flow is denied by configured rule
i.e. 3
packet-tracer input outside_1 tcp 192.168.88.177 1234 192.168.3.178 http
Phase: 7 Type: NAT Subtype: rpf-check Result: DROP Config: nat (outside_1,inside_1) source static any any destination static tim_wan_ip tim_lan_ip net-to-net description for 1to1 nat testing Additional Information: Result: input-interface: outside_1 input-status: up input-line-status: up output-interface: inside_1 output-status: up output-line-status: up Action: drop Drop-reason: (acl-drop) Flow is denied by configured rule
Capture Package
ASA# capture capin interface inside match tcp host 172.16.11.5 host 198.51.100.100
ASA# capture capout interface outside match tcp any host 198.51.100.100
ASA#show capture capin
ASA#show capture capout
![йҰ–й Ғ Logo ¶гБВ Keith і]ӯp !!](/themes/mytheme/logo.png)