жңҖеҫҢжӣҙж–°: 2015-11-15
зӣ®йҢ„
- д»Ӣзҙ№
- е®үиЈқ ASSP 2.2.X
- е®үиЈқеҲҘдәәжү“еҢ…еҘҪзҡ„ module - assp.mod.zip
- Perl cpan
- Install ASSP.pl
- еҹ·иЎҢ
- еҹәжң¬иЁӯе®ҡ(жңҖеҝ«дёҠйҰ¬зҡ„ж–№жі•)
- Panel
- Auto - Startup
- Troubeshoot
- ASSP иЁӯе®ҡ
- е»әз«Ӣ cron job
- Admin д»Ӣйқўзҡ„иЁӯе®ҡ
- starterdb
- Mail SSL/TLS
- Web SSL
- Greylist зҡ„жңүй—ңиЁӯе®ҡ
- URIBL
- Cache File
- Upgrade ASSP
- NoprocessingOK
- ClamAV
- Tips
д»Ӣзҙ№
ASSP is a proxy and not a store-and-forward smtp server.
Perl version >= v5.10.1 <-- ASSP 2.4.X
TCP Port: 55555 | 55553
зҸҫеңЁ ASSP жңү 3 еҖӢзүҲ(2015-09):
- ASSP 1.9.X (stopped at the end of 2014)
- ASSP 2.2.X
- ASSP 2.4.X
ASSP features
- Uses your existing message transport and existing SMTP server.
- Adds SSL/TLS support and Spam Analysis even for your non SSL aware MTA
- Automatically customizes to your site's unique email profile.
- Automatic whitelist -- noone you email will ever be blocked.
- Early Sender validation -- Kills most spam before it ever reaches the server.
- Advanced Virus Scanning with ClamAV and your File-System Virusscanner
- Senders receive immediate notification if mail is blocked but no erroneous bounces are ever generated.
- Redlist keeps an address off the whitelist.
- No-processing addresses pass through.
- Makes use of honeypot type spambucket addresses to automatically recognize spam and update your spam database.
- Bayesian filter intelligently classifies email into spam and non-spam.
- Community based grey IP list, Senderbase, SPF, DKIM support even if your MTA does not support it.
- Supports additional site-defined regular expressions to identify spam or non-spam email.
- Can optionally block all non-whitelisted email (for anti-spam zelots).
- Mime encoded and other camouflaged spam is also recognized.
- Automatically maintains the spam and non-spam databases.
- Accepts whitelist submissions and spam error reports by authorized email.
- Optionally rejects executable attachments from non-whitelisted (or all) addresses.
- Practically no maintenance required.
- Optionally blocks no mail but adds an email header and/or updates the message subject.
- Optionally uses community-based spam statistics to identify hosts that are likely to send spam or non-spam mail.
- Individual users can be configured to receive all mail.
- Shows detailed analysis of spam rating process for specific messages.
- Option to forward a copy of every rejected mail to an address or to resend blocked Mails.
- Can block spam-bombs (when spammers forge your domain in the from field) and fake Bounces
- Keeps spam statistics for your site.
е®үиЈқ ASSP 1.9.X
ASSP 1.9.X Download (2015-09)
http://sourceforge.net/projects/assp/files/ASSP%20Installation/
е®үиЈқ ASSP 2.2.X
Debian:
Install the necessary Perl modules.
aptitude install libcompress-zlib-perl libemail-valid-perl libfile-readbackwards-perl libmail-spf-perl libemail-mime-perl \
libemail-mime-modifier-perl libmail-srs-perl libnet-dns-perl libsys-syslog-perl libnet-ldap-perl unzip clamav \
clamav-daemon libemail-send-perl libio-socket-ssl-perl libio-socket-inet6-perl libnet-cidr-lite-perl \
libmail-spf-query-perl
Install the necessary CPAN
apt-get install build-essential
perl -MCPAN -e shell
еҫҲеҸҜжғңеңЁ Debian дёҠе®үиЈқ peal module еӨұж•—дәҶ -__-
cpan[1]> install File::Scan::ClamAV
ERROR: LOCAL: Socket file /root/.cpan/build/File-Scan-ClamAV-1.91-YSAWTK/clamsock could not be bound: Permission denied
е®үиЈқеҲҘдәәжү“еҢ…еҘҪзҡ„ module - assp.mod.zip
еңЁ sourceforge дёӢијүзҡ„ module йғҪ已經еҫҲиҲҠдәҶ ..
дёӢијү: assp.mod.zip <-- жңүжҲҗ 9M
# дёҖе®ҡиҰҒж”ҫе®ғеңЁ assp зҡ„ sub-folder дёӢ, д№ӢеҫҢеҹ·иЎҢ:
/usr/share/assp/assp.mod/install# perl mod_inst.pl
Perl cpan
еңЁ Centos6 дёҠе®үиЈқ assp 2.4 жүҖй Ҳзҡ„ Modules:
е®үиЈқеңЁ EPEL е…§зҡ„ package:
rpm -Uvh http://dl.fedoraproject.org/pub/epel/6/i386/epel-release-6-8.noarch.rpm
yum install perl-Compress-Zlib perl-Compress-Raw-Zlib perl-Compress-Raw-Bzip2 \ perl-Digest-SHA perl-Digest-SHA1 perl-Digest-MD5-File \ perl-Email-MIME perl-Email-MIME-Modifier perl-Email-Send \ perl-Email-Valid perl-Mail-SPF perl-File-ReadBackwards \ perl-IO-Socket-SSL perl-Net-CIDR-Lite perl-Net-DNS \ perl-Net-IP-Match-Regexp perl-Mail-DKIM perl-Text-Glob \ perl-Number-Compare perl-Convert-TNEF perl-File-ReadBackwards \ perl-MIME-Types perl-Net-SMTP-SSL perl-Tie-DBI \ perl-Time-HiRes perl-Schedule-Cron-Events perl-Sys-MemInfo \ perl-BerkeleyDB perl-Crypt-CBC perl-Crypt-OpenSSL-AES \ perl-Set-Scalar
е®үиЈқеңЁ Cpan е…§зҡ„ package
yum groupinstall "Development Tools"
yum install cpan perl-YAML
д№ӢеҫҢ
# еңЁйҖҷиЈЎдёҖеҖӢдёҖеҖӢиЎҢијғеҘҪ !
threads/1.74 <-- cpan -i threads
threads::shared/1.32 <-- cpan -i threads::shared
Thread::Queue/2.11 <-- cpan -i Thread::Queue
Thread::State/0.09 <-- cpan -i Thread::State
LWP::Simple <-- cpan -i LWP::Simple
Net::LDAP <-- cpan -i Net::LDAP
Net::SMTP <-- cpan -i Net::SMTP
Net::SenderBase <-- cpan -i Net::SenderBase
Net::Syslog <-- cpan -i Net::Syslog
Sys::Syslog <-- cpan -i Sys::Syslog
Mail::SRS <-- cpan -i Mail::SRS
Mail::SPF::Query <-- cpan -i Mail::SPF::Query
* дёҖж¬ЎйҒҺе®үиЈқ
cpan -i threads threads::shared Thread::Queue Thread::State \ LWP::Simple Net::LDAP Net::SMTP Net::SenderBase \ Net::Syslog Sys::Syslog Mail::SRS Mail::SPF::Query
# Centos 7
yum
yum install perl-threads perl-threads-shared perl-Thread-Queue \ perl-Sys-Syslog perl-Mail-SPF perl-Net-IP perl-Text-Unidecode perl-Authen-SASL
cpam
cpan -i Regexp::Optimizer cpan -i Sys::CpuAffinity cpan -i Net::LDAP cpan -i Unicode::GCString cpan -i Tie::RDBM cpan -i Thread::State cpan -i Schedule::Cron cpan -f Mail::SPF::Query cpan -i File::Scan::ClamAV cpan -i ASSP_WordStem cpan -i ASSP_FC
spf
make: *** [test_dynamic] Error 255 JMEHNLE/mail-spf-query/Mail-SPF-Query-1.999.1.tar.gz /usr/bin/make test -- NOT OK
cpan -f -i Mail::SPF::Query
clamav
ln -s /etc/clamd.d/scan.conf /etc/clamd.conf
export CLAMD_PATH=/usr/sbin/
Remark
perl assp.pl еҹ·иЎҢеҫҢ, е®ғжңғз”ҹжҲҗ moduleLoadErrors.txt
иЈЎйқўжңүйӮҒзі»зөұйҮҚе·®е’© package
firewall
firewall-cmd --permanent --zone=public \
--add-rich-rule='rule family="ipv4" source address="w.x.y.z" port protocol="tcp" port="55553" accept'
firewall-cmd --permanent --zone=public \
--add-rich-rule='rule family="ipv4" source address="w.x.y.z" port protocol="tcp" port="55553" accept'
firewall-cmd --reload
Version 2.5
service
cp /opt/assp/rc/assp /etc/init.d
chmod 755 /etc/init.d/assp
е°Ү
/usr/local/bin/perl assp.pl 2>&1 > /dev/null &
ж”№жҲҗ
/usr/bin/perl assp.pl 2>&1 > /dev/null &
/etc/init.d/assp start
watchdog
mkdir /root/scripts
cp assp_watchdog /root/scripts
chmod 755 /root/scripts/assp_watchdog
/root/scripts/assp_watchdog &
дҪҝз”Ё ClamAV
File::Scan::ClamAV <-- cpan -i File::Scan::ClamAV
Compile еүҚдёҖе®үиҰҒе®үиЈқ clamav clamd
yum install clamav clamd
еҗҰеүҮжңғиҰӢеҲ°
Cannot find clamd in /root/bin (or a number of other places) - are you sure clamav in installed?
assp.cfg
# е•ҹз”Ё
UseAvClamd:=1
# еӨ§еҖӢ 4 Mbytes зҡ„дҝЎдёҚ scan
ClamAVBytes:=4000000
# Virus detected Score
vdValencePB:=50
# ClamAV will timeout after this many seconds.
ClamAVtimeout:=20
# default value жҳҜйҢҜзҡ„
AvClamdPort:=/var/run/clamav/clamd.sockP.S.
еңЁжҹҗдәӣ list pass дәҶзҡ„жғ…жіҒдёӢжҳҜдёҚз”Ёиў« scan зҡ„
LOG: [WhitelistedOK] [NoprocessingOK]
жё¬и©Ұ:
1 з„ЎжҜ’
Apr-04-14 09:45:07 m-39657-00279 [VIRUS] 198.160.xx.xx <sender@domain> to: recipient@domain ClamAV: scanned 63304 bytes in message - OK ;
2 жңүжҜ’
Apr-04-14 03:36:57 m-39655-00189 [VIRUS] 114.25.xx.xx <sender@domain> to: recipient@domain ClamAV: scanned 13460 bytes in message - FOUND Heuristics.Phishing.Email.SpoofedDomain;
Service:
/etc/init.d/clamd start
chkconfig clamd on
Troubleshoot
Log:
Apr-03-14 12:48:55 File::Scan::ClamAV module version 1.91 installed but AvClamdPort not ready, error: Cannot connect to unix socket '/var/run/clamav/clamd.ct': connect: No such file or directory;
Setting:
Centos 6 зҡ„ clamd socket default жҳҜ /var/run/clamav/clamd.sock
Install ASSP.pl
yum install unzip
cd /usr/src
mkdir assp
cd assp
wget http://datahunter.org/files/story/481/assp_2.4.3_14258_install.zip
mv assp /usr/share
/usr/share
chmod 770 assp
# -r: Create a system account
useradd -r assp
chown root.assp assp
cd assp
chown -R assp. *
cp -a assp.cfg.defaults assp.cfg
cd /etc/init.d
wget http://datahunter.org/files/story/481/assp_centos.txt -O assp
chmod 700 assp
ln -s /usr/share/assp /usr/share/ASSP
/etc/sysconfig/iptables
................................................................ -A INPUT -m state --state NEW -m tcp -p tcp --dport 25 -j ACCEPT -A INPUT -s x.x.x.x -m state --state NEW -m tcp -p tcp --dport 55555 -j ACCEPT -A INPUT -s x.x.x.x -m state --state NEW -m tcp -p tcp --dport 55553 -j ACCEPT
еҹ·иЎҢ
第дёҖж¬Ўеҹ·иЎҢжңғиҰӢеҲ°д»ҘдёӢ info:
perl assp.pl
Dec-14-12 16:40:30 [Main_Thread] Saving config Dec-14-12 16:40:31 [Main_Thread] Info: saved config to /usr/share/assp/assp.cfg.tmp - which is now renamed to /usr/share/assp/assp.cfg Dec-14-12 16:40:31 [Main_Thread] Finished saving config
第дәҢж¬Ўеҹ·иЎҢжңғиҰӢеҲ°д»ҘдёӢ info:
# 2.2
loading modules.........U [failed] - errors are written to file /usr/share/assp/moduleLoadErrors.txt starting maintenance worker thread -> init all databases starting maintenance worker thread [OK] starting rebuild SpamDB worker thread [OK] starting 5 communication worker threads ..
# 2.4
Nov-05-14 16:56:14 [Main_Thread] MainThread started
loading modules жңү failed еӨҡж•ёе®үиЈқеӣһ missing package е°ұеҸҜ, жҜ”еҰӮжҲ‘зҡ„ Error:
module Mail::SPF::Query could not be loaded module Mail::DKIM::Verifier could not be loaded File::Scan::ClamAV could not be loaded
и§Јжұә:
perl -MCPAN -e shell
cpan[1]> install Mail::SPF::Query
cpan[1]> install Mail::DKIM::Verifier
cpan[1]> force install File::Scan::ClamAV
P.S.
жңүе’©дәӢиЁҳеҫ—зңӢ log file !!
еҹәжң¬иЁӯе®ҡ(жңҖеҝ«дёҠйҰ¬зҡ„ж–№жі•)
иЁӯе®ҡжӘ”:
assp.cfg
иЁӯе®ҡз”ЁжҲ¶:
# дёҚз”Ё root иЎҢзҡ„и©ұ, auto-restart жңғе”” work
# after startup runAsUser:=assp runAsGroup:=assp
Daemon:
# fork and exit AsADaemon:=1
# еҒңз”Ёе·ҰжүӢйӮҠ Menu дёҚз”Ё ajax
hideAlphaIndex:=1
иЁӯе®ҡиў«дҝқиӯ·зҡ„ Mail Server еңЁйӮЈиЈЎ:
1 е°Қ 1
<Network Setup Network Flow>
# your primary SMTP mail transfer agent (MTA)
SMTP Destination (smtpDestination)
йҖІйҡҺ:
localDomains:=file:files/localdomains.txt
domain1.com=>mx.domain.com:25 domain2.com=>mx.domain2.com:1025
Checking
[root@assp ASSP]# ps aux | grep -i assp
assp 4608 0.7 13.9 79028 71032 pts/2 S 10:33 0:11 perl assp.pl
Service:
/etc/init.d/clamd start
chkconfig assp on
chkconfig clamd on
Panel
Web Admin:
127.0.0.1:55555
жңүй—ңиЁӯе®ҡ:
webAdminPort:=55555 allowAdminConnectionsFrom:= 127.0.0.1 webAdminPassword:= <-- дёҚз”Ё pw
V2.2.x зҡ„ Default PW: root / nospam4me
е ұиЎЁ:
127.0.0.1:55553
жңүй—ңиЁӯе®ҡ:
webStatPort:=55553 allowStatConnectionsFrom:=127.0.0.1
Auto - Startup Script
е»әз«Ӣ /etc/init.d/assp
# Centos cp rc/assp /etc/init.d/
дҝ®ж”№иЁӯе®ҡ
asspbase=/usr/share/ASSP # /usr/local/bin/perl /usr/bin/perl
chmod 755 assp
/etc/init.d/assp start
# Auto Start
# Debian
update-rc.d assp defaults 50
# Centos
chkconfig assp on
Watchdog
дҝ®ж”№
#!/bin/bash # е°ҚжҮү assp е…§зҡ„ "$asspbase/pid" assppidfile=/usr/share/ASSP/pid logfile=/var/log/assp_watchdog.log
chmod 755 /usr/share/ASSP/rc/assp_watchdog
/etc/rc.local
/usr/share/ASSP/rc/assp_watchdog &
Troubeshoot
收еҲ°д»ҘдёӢзҡ„ Return Mail
Return1
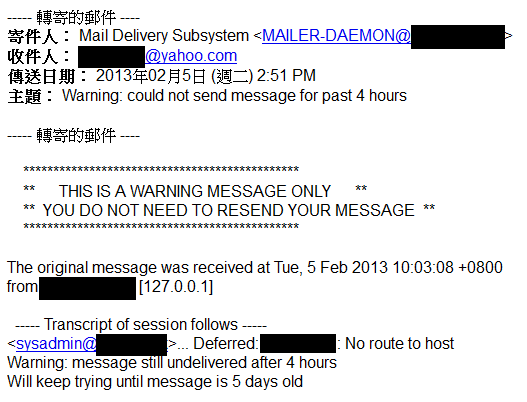
Return2
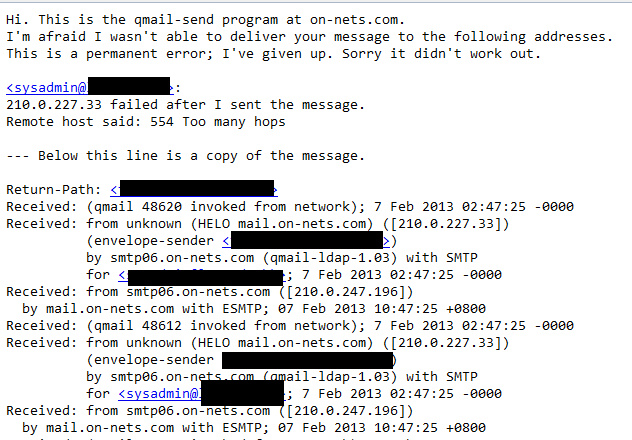
жғ…жіҒ:
[email protected] -- send --> B@mydomain [email protected] <-- return -- B@anotherdomain
жңүй—ңиЁӯе®ҡ:
2 dns server
assp configure
# SMTP error message to reject spam # The literal LOCALDOMAIN will be replaced by the recipient domain or defaultLocalHost. # SESSIONID will be replaced by the unique ASSP identifier. assp.cfg:defaultLocalHost:= # Copy Spam and Send to this Address (collection mode, eg. baysSpamLog) assp.cfg:sendAllSpam:=
ASSP иЁӯе®ҡ
# mx server жІ’жңү connection зҡ„йҷҗеҲ¶
noMaxSMTPSessions:=127.0.0.1 noGRIP:=127.0.0.1
# SMTP Session Limits:
maxSMTPSessions:=32 maxSMTPipSessions:5 maxSMTPipConnects:=5 maxSMTPipDuration:=90 smtpIdleTimeout:=300
# 當дёҖеҖӢ Domain з”ұеӨҡйҒҺ 10 еҖӢдёҚеҗҢ IP 收йҒҺдҝЎеҫҢ, йӮЈе®ғжңғиў« Ban 2 е°ҸжҷӮ
maxSMTPdomainIP:=10 maxSMTPdomainIPExpiration:=7200
#
localDomains:=file:files/localdomains.txt nolocalDomains:= # Enter any addresses that are your ISP or backup MX servers, separated by pipes (|). ispip:=127.0.0.1
# Validate Sender Domain MX/A
DoDomainCheck:=1
# Enable SPF Validation
ValidateSPF:=1
# RBL
RBLServiceProvider:=zen.spamhaus.org|bl.spamcop.net
# 210.0.255.250 жҳҜ DNS Server # 209.85.160.50 жҳҜ Sender зҡ„ IP Dec-23-13 18:29:29 Sending DNS-query to 210.0.255.250 on zen.spamhaus.org for RBL checks on 209.85.160.50 Dec-23-13 18:29:29 Sending DNS-query to 210.0.255.250 on psbl.surriel.com for RBL checks on 209.85.160.50 Dec-23-13 18:29:29 Sending DNS-query to 210.0.255.250 on ix.dnsbl.manitu.net for RBL checks on 209.85.160.50 Dec-23-13 18:29:29 Sending DNS-query to 210.0.255.250 on bl.spamcop.net for RBL checks on 209.85.160.50 Dec-23-13 18:29:29 Sending DNS-query to 210.0.255.250 on l2.apews.org for RBL checks on 209.85.160.50 Dec-23-13 18:29:29 Sending DNS-query to 210.0.255.250 on no-more-funn.moensted.dk for RBL checks on 209.85.160.50 Dec-23-13 18:29:29 Sending DNS-query to 210.0.255.250 on combined.njabl.org for RBL checks on 209.85.160.50 Dec-23-13 18:29:29 Sending DNS-query to 210.0.255.250 on safe.dnsbl.sorbs.net for RBL checks on 209.85.160.50
# иЁӯе®ҡз”Ёд»Җйәј DNS Server
DNSServers:=xxx|xxx
# е…¶д»– turning
enableINET6:=0
# reload дәәжүӢдҝ®ж”№йҒҺзҡ„ assp
kill -HUP <pid>
е»әз«Ӣ cron job
- stat.pl <-- To list statistics from your maillog.txt (daily)
- rebuildspamdb.pl <-- rebuild the bayes database (weekly)
Rebuild SpamDB - rebuildspamdb
rebuildspamdb.pl builds the statistical model that is used to test incoming mail.
Directories:
- spam
- notspam
- errors/spam
- errors/notspam
usage:
perl rebuildspamdb.pl path/to/assp-base-dir
ж–°зүҲжңғиҮӘеӢ• rebuildspam зҡ„
assp.cfg
# Download and Install (rebuildspamdb.pl) AutoUpdateREBUILD:=2 # run rebuildspamdb.pl at 3:00 06:00 .. 24:00 RebuildSchedule:=3|6|9|12|15|18|21|24 RebuildNotify:=admin@domain
mailreport.sh
#!/bin/sh _report=/tmp/daily_report.txt _recipient="[email protected]" echo "assp Daily Report" | mail -s "assp report" -a $_report $_recipient
stat.pl
list statistics from your maillog.txt file
/usr/share/ASSP/stat.pl /usr/share/ASSP/logs/maillog.txt As of Fri Jun 7 10:52:25 2013 the mail logfile shows: 3 proxy / smtp connections 0 were dropped for attempted relays (0.0% of total). 3 messages for 3.0 messages per day were spam (0.0%) or 0.0 spams per day 0 additions to / verifications of the whitelist (0.0 per day) 6 were judged spam by the bayesian filter (0.0% of spam) 0 were to spam addresses (0.0% of spam) 3 were nonspam (100.0%) or 3.0 nonspam per day 0 were sent from local clients (0.0% of nonspam) 3 were from whitelisted addresses (100.0% of nonspam) were from/to noprocessing addresses (0.0% of nonspam) 0 messages were passed to SPAMLOVERs 0 were ok after all checks (0.0% of nonspam) -1 addresses are on the whitelist
cron jobs
crontab -u assp -e
# assp 1 1 * * 1 /usr/share/assp/rebuildspamdb.pl /usr/share/assp > /dev/null 2>&1 # daily report 50 23 * * * /usr/share/assp/stat.pl /usr/share/assp/logs/maillog.txt > /tmp/daily_report.txt 10 0 * * * /home/assp/mailreport.sh
Admin д»Ӣйқўзҡ„иЁӯе®ҡ
# йҷҗеҲ¶йӮЈиЈЎзҡ„дәәеҸҜд»Ҙ connect дҫҶ
allowAdminConnectionsFrom allowStatConnectionsFrom
# е®үе…ЁеҸҠж•ҲиғҪ
enableWebAdminSSL:=1 EnableHTTPCompression:=1
# е·ҰжүӢйӮҠ Menu дёҚз”Ё ajax
hideAlphaIndex:=1
# дёҚ upload жқұиҘҝ
noGriplistUpload:=1 noGriplistDownload:=1 totalizeSpamStats:=0
# йҳІжҜ’иЁӯе®ҡ
# е°Қ whitelist зҡ„дәәз…§ scan virus
ScanWL:=0 FileScanWL:=0
For an UPDATE installation
# go to installation dir
cd /usr/share/ASSP
# backup
BAKDIR=backup-`date +%Y%m%d`
mkdir $BAKDIR
mv *.pl $BAKDIR
cp assp.cfg $BAKDIR
# upgrade
cp -a /usr/share/ASSP.new/*.pl ./
# testing
perl assp.pl
starterdb
Bayesian Starter Database
и§ЈеЈ“еҫҢж”ҫе…Ҙ assp/starterdb
Mail SSL/TLS
enableSSL:=1 SSLCertFile:=/usr/share/ASSP/certs/server-cert.pem SSLKeyFile:=/usr/share/ASSP/certs/server-key.pem SSLtimeout:=5 SSLCacheInterval:=0 SSLLog:=1 SSLRetryOnError:=1
Greylist зҡ„жңүй—ңиЁӯе®ҡ
assp.cfg
EnableDelaying:=1
# DelayWL: Whitelisted Greylisting - Enable Greylisting for whitelisted users.
DelayWL:=0
DelayNP:=0
DelaySL:=0
# 'Enter the number of minutes for which delivery, related with IP address of the sending host,
# is refused with a temporary failure.(Default: 5 minutes)
DelayEmbargoTime:=1
# 'Enable simple delaying for IP\'s in black penaltybox with totalscore above this value.'
DelayIP:=50
DelayIPTime:=1
# Add X-Assp-Delayed Header
DelayAddHeader:=1
# number of days for which whitelisted 'Tuplet' is considered valid.
DelayExpiryTime:=36
# /24 subnet rather than the specific IP, default: 1
DelayUseNetblocks:=1
# associated with spam, viri, failed rbl, spf etc, it is deleted from the safelist.
DelayExpireOnSpam:=1
# default: 1. adds some level of security to the delay database.
DelayMD5:=0
# noDelay:=file:files/nodelay.txt
noDelay: 145.145.145.145|145.146.
DelayShowDB:=file:files/delaydb
DelayShowDBwhite:=file:files/delaydb.white
DelayError:=451 4.7.1 Please try again later
# default: 10800
CleanDelayDBInterval:=120жӘ”жЎҲ delaydb еҸҠ delaydb.white еҸӘжңғеңЁ CleanDelayDBInterval з”ҹж•ҲеҫҢжүҚе»әз«Ӣ !
Dec-23-13 19:28:19 Cleaning up delaying databases ... Dec-23-13 19:28:19 Cleaning delaying database (triplets) finished; keys before=1, deleted=0 Dec-23-13 19:28:19 Cleaning delaying database (safelisted tuplets) finished; keys before=0, deleted=0
第дёҖж¬ЎжҺҘи§ё
Dec-23-13 18:32:41 94761-11364 202.181.xxx.xxx <[email protected]> adding new triplet: (202.181.xx.xx,[email protected],[email protected]) Dec-23-13 18:32:41 94761-11364 202.181.xxx.xxx <[email protected]> to: [email protected] recipient delaying queued: [email protected] Dec-23-13 18:32:41 94761-11364 202.181.xxx.xxx <[email protected]> to: [email protected] recipient delayed: [email protected]
第дәҢж¬ЎжҺҘи§ё
Dec-23-13 19:45:34 99134-10282 202.181.201.11 <[email protected]> accepting triplet: (202.181.201.0,tim@[email protected],[email protected]) waited: 1m 2s
д№ӢеҫҢзҡ„жҺҘи§ё
Dec-23-13 19:50:17 99417-04927 202.181.201.11 <[email protected]> renewing tuplet: (202.181.201.0,[email protected]) age: 0s
NoprocessingOK
иЁӯе®ҡ Over жҹҗ Size зҡ„дҝЎдёҚ Scan
иЁӯе®ҡ:
# 5 MB npSize:=5000000 npSizeOut:=5000000
Log i.e.
Apr-03-14 11:03:13 m-39649-00005 [NoprocessingOK] 202.181.201.11 <sender@domain> to: recipient@domain noprocessing - message size (8555350) is above 2000000 (npSize) - [test mail @ 1106] - attachment '6.1mb.7z'
URIBL
дҝЎд»¶е…§зҡ„жүҖжңү URL йғҪжңғеҺ» check uribl зҡ„.
assp.cfg
ValidateURIBL:=1 uriblTestMode:= uriblnValencePB:=20 uriblValencePB:=25 URIBLWL:=1 URIBLNP:=1 URIBLLocal:=1 URIBLISP:=1 URIBLServiceProvider:=multi.surbl.org|black.uribl.com URIBLCCTLDS:=file:files/URIBLCCTLDS.txt URIBLmaxuris:=0 URIBLmaxdomains:=0 URIBLNoObfuscated:=1 URIBLmaxreplies:=2 URIBLmaxhits:=1 URIBLmaxtime:=10 URIBLsocktime:=1 URIBLwhitelist:=doubleclick.net noURIBL:= AddURIBLHeader:=1 URIBLCacheExp:=24 URIBLError:=554 5.7.1 Blacklisted by URIBLNAME
ValidateURIBL
Enable URI Blocklist Validation about (Default: 1)
URIBLwhitelist (Whitelisted URIBL Domains)
This prevents specific domains from being checked by URIBL module. For example:files/uriblwhite.txt.
URIBLCacheInterval (URIBL Cache Refresh Interval for Hits)
Domains in cache will be removed after this interval in days. Empty or 0 will disable the cache.
URIBLCacheIntervalMiss (URIBL Cache Refresh Interval for Misses)
Domains in cache with status=2 (miss) will be removed after this interval in days. Empty or 0 will prevent caching of non-hits.
Cache File:
pb/pbdb.uribl.db
Cache File
еңЁ pb Folder е…§
global pbdb.mxa.db pbdb.rbl.db.bak pbdb.spf.db pbdb.white.db.bak
pbdb.back.db pbdb.mxa.db.bak pbdb.rwl.db pbdb.spf.db.bak
pbdb.back.db.bak pbdb.ptr.db pbdb.rwl.db.bak pbdb.uribl.db
pbdb.black.db pbdb.ptr.db.bak pbdb.sb.db pbdb.uribl.db.bak
pbdb.black.db.bak pbdb.rbl.db pbdb.sb.db.bak pbdb.white.db
Upgrade ASSP
copy the following files to your existing ASSP folder:
- assp.pl <-- еҝ…иҰҒзҡ„
- rebuildspamdb.pl
copy the following folders to your existing ASSP folder:
- images
- reports
- certs
- docs
- notes
copy from folder "files" into the folder "files" inside your old ASSP folder
(merge your modifications in the old files)
Tips
дҝқжҢҒжңҖж–°зүҲ:
# Download update еҲ° "/usr/share/ASSP/download (assp.pl)" AutoUpdateASSP:=1
дҝқжҢҒ ASSP жӯЈеёёиЎҢ:
# Exception жҷӮ restart AutoRestart:=1 # second MainloopTimeout:=600 # Mainloop Timeout AutoRestartAfterTimeOut:=1 # reload configuration data, combat potential memory leaks AutoRestartInterval:=12 # жүҖжңү restart йғҪжңғ call е®ғ AutoRestartCmd:=sleep 30;"/usr/bin/perl" "/usr/share/ASSP/assp.pl" "/usr/share/ASSP" & NoMultipleASSPs:=1
| йҷ„еҠ жӘ”жЎҲ | еӨ§е°Ҹ |
|---|---|
| assp.txt | 2.59 KB |
| assp_centos.txt | 1.08 KB |
| 55553.jpg | 223.07 KB |
| assp_2.4.3_14258_install.zip | 1.46 MB |
![йҰ–й Ғ Logo ¶гБВ Keith і]ӯp !!](/themes/mytheme/logo.png)