жңҖеҫҢжӣҙж–°: 2024-09-30
зӣ®йҢ„
- жҮүз”Ё: еңЁ Mutt дёӯдҪҝз”Ё GnuPG
- еңЁ Vim дёӯдҪҝз”Ё GnuPG
- gpg4win
- жҮүз”Ё: Verify Package
- жҮүз”Ё: Thunderbird - Enigmail
- жҮүз”Ё: зҚІеҫ— MariaDB зҡ„ Key
- й…ҚеҗҲ sha256sum дҪҝз”Ё
жҮүз”Ё: еңЁ Mutt дёӯдҪҝз”Ё GnuPG
еңЁ ~/.muttrc дёӯеҠ е…ҘдёӢеҲ—зҡ„е…§е®№
macro index S ":toggle pgp_verify_sig\n" set pgp_verify_sig=no
еүҮеҰӮжһңдҪ еңЁ index йҒёе–®дёӯијёе…Ҙ "S", е°ҮжңғиҮӘеӢ•е•ҹеӢ•дёҖеҖӢдҪҺйҖҹзҡ„ GnuPG
еңЁ Vim дёӯдҪҝз”Ё GnuPG
е°Ү examples subdirectory дёӯзҡ„ _vimrc ж–Ү件зҡ„е…§е®№еҠ еҲ° ~/.vimrc е°ұеҸҜд»ҘиҮӘ然зҡ„еҹ·иЎҢ GnuPG.
Gpg4Win
Window дёҠзҡ„ opengpg
Download: https://www.gpg4win.de/download.html
Package
- gpg4win-light-2.3.4.exe @20191008
- gpg4win-3.1.10.exe @20191008
Remark
Gpg4Win <= 2.1.0 passphrase does not work in a non-English "Language"
light & vanilla
gpg4win-vanilla and gpg4win-light have been left on the now outdated and not maintained 2.0 gpg branch.
These packages have not been updated for more than a year and are potentially putting users of these at risk.
Verify Package
FILENAME.asc file
-----BEGIN PGP SIGNATURE----- ... -----END PGP SIGNATURE-----
е®ғжңғз”Ёж–ј verify FILENAME
Verify Package by ".asc" file
gpg --verify sha256sums.asc
Notes: 當 FILENAME иҲҮ FILENAME.asc дёҚеңЁз”ЁдёҖзӣ®йҢ„жҷӮ
gpg --verify sha256sums.asc /path/to/sha256sums
жң¬ең°жңӘжңү Public Key жҷӮ
gpg --verify rsync-3.1.2.tar.gz.asc rsync-3.1.2.tar.gz
gpg: Signature made Tue 22 Dec 2015 04:25:56 AM HKT using DSA key ID 4B96A8C5
gpg: Can't check signature: No public keyGet Public Key & Verify
gpg --recv-keys 4B96A8C5
gpg: requesting key 4B96A8C5 from hkp server keys.gnupg.net gpg: /root/.gnupg/trustdb.gpg: trustdb created gpg: key 4B96A8C5: public key "Wayne Davison <[email protected]>" imported gpg: no ultimately trusted keys found gpg: Total number processed: 1 gpg: imported: 1
gpg --verify rsync-3.1.2.tar.gz.asc
gpg: Signature made Tue 22 Dec 2015 04:25:56 AM HKT using DSA key ID 4B96A8C5 gpg: Good signature from "Wayne Davison <[email protected]>" gpg: aka "Wayne Davison <[email protected]>" gpg: WARNING: This key is not certified with a trusted signature! gpg: There is no indication that the signature belongs to the owner. Primary key fingerprint: 0048 C8B0 26D4 C96F 0E58 9C2F 6C85 9FB1 4B96 A8C5
Warning
gpg: WARNING: This key is not certified with a trusted signature!the key in your keyring & the signatures are valid, but either you have not marked the keys as trusted
=> no proof it belongs to whom it pretends to
=> Compare the fingerprints with those shown on business cards / homepage
How to trust an imported key
Trust level (當 fingerprint е°Қе®Ң homeage жӯЈзўәжҷӮ)
Edit trust level of keys by running "gpg --edit-key", and then using the trust command.
i.e.
gpg --edit-key <fingerprint>
gpg> trust
... 1 = I don't know or won't say 2 = I do NOT trust 3 = I trust marginally 4 = I trust fully 5 = I trust ultimately m = back to the main menu
Your decision? 3
gpg> quit
Trust in a key's owner(1~5)
A key's trust level is something that you alone assign to the key,
and it is considered private information.
It is not packaged with the key when it is exported;
It is even stored separately from your keyrings in a separate database.
There are 4 trust levels:
unknown(1)
Nothing is known about the owner's judgement in key signing.
(Keys on your public keyring that you do not own initially have this trust level.)
none(2)
The owner is known to improperly sign other keys.
marginal(3)
The owner understands the implications of key signing and properly validates keys before signing them.
fully(4)
The owner has an excellent understanding of key signing,
and his signature on a key would be as good as your own.
Find out when it expires
# -k, --list-keys
gpg -k 4B96A8C5
pub 1024D/4B96A8C5 2003-12-19 uid Wayne Davison <[email protected]> uid Wayne Davison <[email protected]> sub 1024g/29C67D63 2003-12-19
Update Keys
gpg --refresh-keys
жҮүз”Ё: Thunderbird - Enigmail
http://www.enigmail.net/home/index.php
收件иЁӯе®ҡ: Decryt & Verify
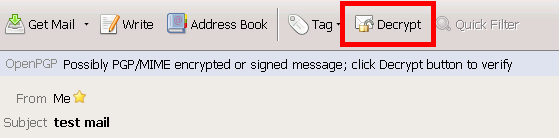
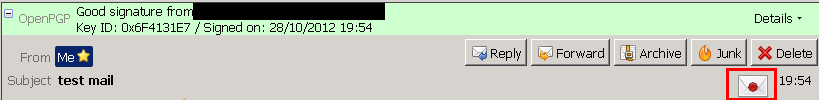
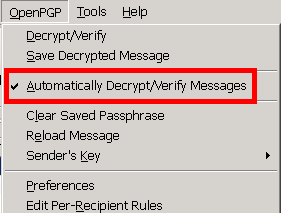
еҜ„件иЁӯе®ҡ:
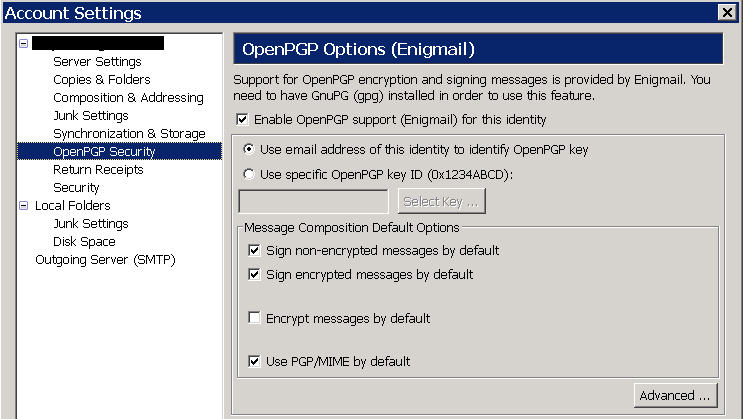
дҝЎд»»е°Қж–№зҡ„ Key:
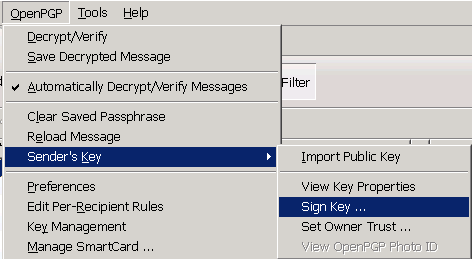
<MIME Header>
PGP/MIME is a standard defined in RFC 3156 (inline-PGP standard)
當еҲҘдәәзҡ„ E-Mail Client з„Ў GPG еҠҹиғҪжҷӮ, йӮЈ"з°ҪеҗҚ"е°ұжңғд»Ҙйҷ„件еҪўејҸеӯҳеңЁ: signature.asc
е…§е®№еүҮжҳҜ html еҪўејҸеӯҳеңЁ
е·ІзҹҘж”ҜжҸҙзҡ„ Client: 2014-02-20
(Apple Mail, Becky, Evolution, KMail, Mulberry, Sylpheed and The Bat!.)
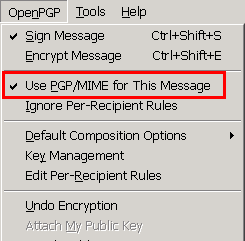
дёҚз”Ё MIME зҡ„ Mail:
з•¶ж јејҸжҳҜ HTML жҷӮ, е°ұжңғжңү Warning
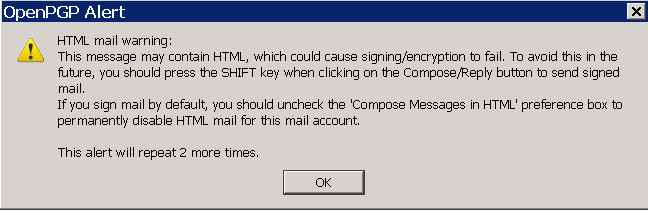
Mail зҡ„ Source е…§е®№:
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 test -----BEGIN PGP SIGNATURE----- Version: GnuPG v2.0.17 (MingW32) Comment: Using GnuPG with Mozilla - http://www.enigmail.net/ iQEcBAEBAgAGBQJQjSNoAAoJEMNEx0ZvQTHnoYcIAL82miLiUo2n/Yj+rflVtMLd ................................................................ -----END PGP SIGNATURE-----
з”Ё MIME зҡ„ Mail Source:
Content-Type: multipart/signed; micalg=pgp-sha1; protocol="application/pgp-signature"; boundary="------------enigC43BDF83D84A140632D2F633" This is an OpenPGP/MIME signed message (RFC 2440 and 3156) --------------enigC43BDF83D84A140632D2F633 Content-Type: text/plain; charset=ISO-8859-1 Content-Transfer-Encoding: quoted-printable testing --------------enigC43BDF83D84A140632D2F633 Content-Type: application/pgp-signature; name="signature.asc" Content-Description: OpenPGP digital signature Content-Disposition: attachment; filename="signature.asc" -----BEGIN PGP SIGNATURE----- Version: GnuPG v2.0.17 (MingW32) Comment: Using GnuPG with Mozilla - http://www.enigmail.net/ iQEcBAEBAgAGBQJQjRzyAAoJEMNEx0ZvQTHnRQIIAIMzAGC1+50h+mVdrdnWCrhB .............................................................. -----END PGP SIGNATURE----- --------------enigC43BDF83D84A140632D2F633--
жҢҮжҳҺиҮӘе·ұжҳҜз”ЁйӮЈеҖӢ keyserver
Advanced -> Send 'OpenPGP' Header -> Send URL for key retrieval
# OpenPGP: url=pool.sks-keyservers.net
жҮүз”Ё: зҚІеҫ— MariaDB зҡ„ Key
gpg --keyserver hkp://pgp.mit.edu --recv-keys 1BB943DB
gpg: key 84DF8D521BB943DB: public key "Totally Legit Signing Key <[email protected]>" imported gpg: key CBCB082A1BB943DB: public key "MariaDB Package Signing Key <[email protected]>" imported gpg: Total number processed: 2 gpg: imported: 2
# жңғ export дәҶ [email protected] зҡ„ pubkey !!
gpg --export --armour 1BB943DB > mariadb-signing-key.asc
# import дәҶе°ұеҮәдәӢ !!
rpm --import mariadb-signing-key.asc
Summary
е®ҳз¶ІдҫӢеҮә full key еҫҲйҮҚиҰҒ
1993 69E5 404B D5FC 7D2F E43B CBCB 082A 1BB9 43DB
е»әиӯ°
rpm --import https://supplychain.mariadb.com/MariaDB-Server-GPG-KEY
й…ҚеҗҲ sha256sum дҪҝз”Ё
https://openwrt.org/docs/guide-user/security/signatures
# key for unattended snapshot builds (v23@2024)
User ID: OpenWrt Build System [email protected] Fingerprint: 54CC 7430 7A2C 6DC9 CE61 8269 CD84 BCED 6264 71F1 Public Key: 0xCD84BCED626471F1
# key for 22.03 release builds
User ID: OpenWrt Build System [email protected] Fingerprint: BF85 6781 A012 93C8 409A BE72 CD54 E82D ADB3 684D Public Key: 0xCD54E82DADB3684D
# Usage verify v23.05
gpg --recv-keys 0xCD84BCED626471F1
gpg -k --fingerprint
gpg --verify sha256sums.asc sha256sums
![йҰ–й Ғ Logo ¶гБВ Keith і]ӯp !!](/themes/mytheme/logo.png)