жңҖеҫҢжӣҙж–°: 2019-12-27
зӣ®йҢ„
- д»Ӣзҙ№
- XML
- Fix (easy)
- aspnet_regiis
- crazy
- export / import (apppool)
- File
- URL Rewrite
- Error after sysprep
- иЁӯзҪ® log зҡ„ fields
- Application Pool
IIS 6.0 application pool identity
The application pool identity is the name of the account under which the worker process of the application pool runs.
Network Service
Local Service:
The Local Service user account also has low-level access rights
LocalSystem:
which has more user rights than the Network Service or Local Service user account.
IIS_WPG group
IIS_WPG user group is new in IIS 6.0.
It provides the minimum set of privileges and permissions required to start and run a worker process on a Web server.
the IIS_WPG group contains the Network Service, Local Service, LocalSystem, and IWAM_ComputerName accounts.
To designate a specific user account as a worker process identity for a Web site, make the user account a member of the IIS_WPG group. This is a convenient way to configure a custom identity for a worker process without manually assigning privileges and permissions.
Unable to generate a temporary class (result=1).
error CS2001: Source file 'C:\WINDOWS\TEMP\7x9jn1zn.0.cs' could not be found
error CS2008: No inputs specified
Resolution
List folder / read data
If the IIS group is not listed, Add the group. Once added, or if it was already listed, set the permissions to at least
List folder / read data
for This folder, subfolders and files
By default, the NETWORK SERVICE account is a member of Authenticated Users which is a member of Users which has write access to C:\Windows\Temp. If NETWORK SERVICE is not a member of Authenticated Users on the system and/or Authenticated Users is not a member of Users and/or Users does not have write permissions to C:\Windows\Temp, this error can occur.
w3wp.exe <-- new user
Worker processes in IIS 6.0 and in IIS 7 run as Network Service by default. Network Service is a built-in Windows identity. It doesn't require a password and has only user privileges; that is, it is relatively low-privileged. Running as a low-privileged account is a good security practice because then a software bug can't be used by a malicious user to take over the whole system.
However, a problem arose over time as more and more Windows system services started to run as Network Service. This is because services running as Network Service can tamper with other services that run under the same identity. Because IIS worker processes run third-party code by default (Classic ASP, ASP.NET, PHP code), it was time to isolate IIS worker processes from other Windows system services and run IIS worker processes under unique identities. The Windows operating system provides a feature called "virtual accounts" that allows IIS to create a unique identity for each of its application pools. Click here for more information about Virtual Accounts.
е•ҸйЎҢ:
failed to decrypt attribute 'password'
OR
Bad Data. (Exception from HRESULT: 0x80090005)
IIS is stored in flat files with encrypted sections.
i deleted username and password definitions for applications and it worked well.
XML:
XML location
%SystemDrive%\Windows\System32\inetsrv\config\
===================================================
<RSAKeyValue><Modulus>...</Modulus><Exponent></Exponent></RSAKeyValue>
===================================================
<easy>
Export keys from source server:
aspnet_regiis -px "iisConfigurationKey" "C:\IISKEY\iisConfigurationKey.xml" -pri
aspnet_regiis -px "iisWasKey" "C:\IISKEY\iisWasKey.xml" -pri
Import on your target/problem server:
aspnet_regiis -pi "iisConfigurationKey" "C:\IISKEY\iisConfigurationKey.xml"
aspnet_regiis -pi "iisWasKey" "C:\IISKEY\iisWasKey.xml"
After importing keys, source %windir%\system32\inetsrv\config\applicationHost.config needs to be transferred to destination too.
If you copy over the <configProtectedData> tag, you should be ok then without copying the applicationHost.config
Either manually delete default website, default pool pool, etc or run the following appcmd's ON THE NEWLY KICKED NODE WITH NO SITES ON IT. PLEASE BE CAREFUL
a. appcmd list apppools /xml | appcmd delete apppools /in
b. appcmd list sites /xml | appcmd delete sites /in
6.Import the app pools then sites on the new node
a. appcmd add apppool /in < c:\apppools.xml
b. appcmd add site /in < c:\sites.xml
aspnet_regiis
aspnet_regiis - Administration utility to install and uninstall ASP.NET on the local machine.
ж”ҫеңЁ C:\Windows\Microsoft.NET\Framework64\v4.0.30319
-px container file
Exports an RSA public/private key pair from the specified container to the specified XML file. This argument takes the following optional modifiers
-pi container file
Imports an RSA public/private key pair to the specified container from the specified XML file.
<insecure>
File: applicationHost.config
Open your applicationHost.config in %windir%\system32\inetsrv\config and search for "[enc:" and put the configurations that are encrypted in the file in clear text.
Example Before:
<processModel identityType="User" userName="domain\username" password="[enc:IISWASOnlyAesProvider:?????????=:enc]” />
Example After:
<processModel identityType="User" userName="domain\username" password="UserNamesPasswordInClearText" />
Modify your MahineGuid
Modify your MahineGuid to match your keys needed to decrypt.
C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys
<KEYGUID>_<MACHINEGUID>
MACHINEGUID= xxx_xxx_xxx_xxx_xxx
flip the MachineGuid in
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography
to match the suffix of the keys stored in
C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys
New Feature
Windows Process Activation Service
Windows Process Activation Service generalizes the Internet Information Services (IIS) process model,
removing the dependency on HTTP.
All the features of IIS that were previously available only to HTTP applications are now available to applications hosting Windows Communication Foundation (WCF) services,
by using non-HTTP protocols. IIS 7.0 also uses Windows Process Activation Service for message-based activation over HTTP.
Conditions for installing and running WAS
From a security standpoint, you should not run Windows Process Activation Service unless you are supporting a .NET Framework 3.5.1 application or IIS 7.0.
IIS and .NET Framework 3.5.1 automatically install Windows Process Activation Service as needed. You should not install Windows Process Activation Service by itself.
TCP Port Sharing
part of Windows Communication Foundation (WCF)
no need to make remote applications aware that Net.TCP Port Sharing is enabled.
the WCF TCP transport infrastructure does not directly open a TCP socket in the application process.
Instead, the transport infrastructure registers the service’s base address Uniform Resource Identifier (URI) with the Net.Tcp Port Sharing Service and waits for the port sharing service to listen for messages on its behalf. Messages that are addressed to the application service are dispatched by the port sharing service as they arrive.
Windows Process Activation Service (WAS)
WAS to accomplish message-based activation over HTTP.
export / import (apppool)
To Export the Application Pools on IIS 7 :
%windir%\system32\inetsrv\appcmd list apppool /config /xml > c:\apppools.xml
To import the Application Pools:
%windir%\system32\inetsrv\appcmd add apppool /in < c:\apppools.xml
To Export all your website:
%windir%\system32\inetsrv\appcmd list site /config /xml > c:\sites.xml
To Import the website:
%windir%\system32\inetsrv\appcmd add site /in < c:\sites.xml
appcmd list apppool
To export/import a single application pool:
%windir%\system32\inetsrv\appcmd list apppool "MyAppPool" /config /xml > c:\myapppool.xml
Import:
%windir%\system32\inetsrv\appcmd add apppool /in < c:\myapppool.xml
appcmd list site
To export/import a single website:
%windir%\system32\inetsrv\appcmd list site "MyWebsite" /config /xml > c:\mywebsite.xml
Import:
%windir%\system32\inetsrv\appcmd add site /in < c:\mywebsite.xml
Backup & Restore
appcmd list backup
appcmd restore backup <backup name>
File
ApplicationHost.config file:
The server-level configuration file that contains IIS settings.
Administration.config:
The server-level configuration file that contains IIS settings for IIS Manager.
ConfigEncKey.key file:
A password-protected file that contains the encryption keys in a custom format. After you use IIS Manager to configure your computer to use shared configuration and encryption keys, the computer imports the encryption keys and stores them locally.These keys are used to decrypt any encrypted information in the configuration files.
Basic authentication
* "Basic Authentication" shares the same accounts that you have on your local computer or network.
Basic Authentication: transmits unencrypted base64-encoded passwords across the network.
Install & Setup
1. Enable "Basic Authentication" in "Windows Features"
2. In Features View, double-click Authentication.
3. On the Authentication page, select Basic Authentication.
4. In the Actions pane, click Enable to use Basic authentication with the default settings.
Create a user account
If you leave the domain and realm empty, local accounts are what are actually being used.
Right click on Computer and choose "Manage" (or go to Control Panel > Administrative Tools > Computer Management)
under "Local Users and Groups" you can add a new user. Then, give that user permission to read the directory where the site is hosted.
Notes:
-
After creating the user, be sure to edit the user and remove all roles
(user дёҚз”Ё add еҲ° Folder зҡ„ Security)
SSL
"Require SSL" # IIS 8
Turn on "Require SSL" still responds without SSL (http) but it will fail immediately.
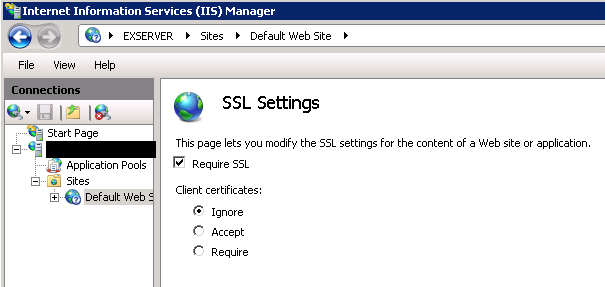
Toubleshoot
Apply Cert. Error
- Open IIS
- Right Click affected website and select “Edit Bindings”
- “Edit” binding for 443
- Change SSL Cert to IIS Dev Cert and Apply
- Re-Apply your cert and get the following:
Error
"A specified logon session does not exist. It may already have been terminated."
Cause
When importing a certificate file (.pfx) through IIS Manager, the option box to "Allow this certificate to be exported" is uncheck.
Re-import certificate (.pfx) file using "Mark this key as exportable."
UrlScan
е®үиЈқ UrlScan
IISз®ЎзҗҶ -> з¶Із«ҷпјҲеҸіж“Ҡеұ¬жҖ§пјү – ISAPIзҜ©йҒёеҷЁ –> й»һж“Ҡж·»еҠ –> ијёе…ҘзҜ©йҒёеҷЁеҗҚзЁұе’Ңж·»еҠ еҸҜеҹ·иЎҢж–Ү件dllпјҲй»ҳиӘҚе…ҒиЁұпјү –> й»һж“Ҡзўәе®ҡеҚіеҸҜ -> 然еҫҢйҮҚе•ҹIISеҚіеҸҜз”ҹж•ҲгҖӮ
On successful installation you should have a folder %windir%\system32\inetsrv\urlscan
(additionally under %windir%\syswow64\inetsrv as well for x64 installations)
Global Filter
The default installation of UrlScan v3.1 installs the filter as a global filter.
See the Site Filter section on how to setup your filter as a site filter
Disallowing Certain Types of Requests
The allow list is case sensitive and is evaluated before the deny list
(before the deny list to remain conservative in the evaluation of rules.)
# жӯӨйҒёй …иЁӯе®ҡзӮә 1
UseAllowVerbs=1
[AllowVerbs] GET HEAD POST
дҝқз•ҷжүҖжңүиў«зҰҒжӯўзҡ„и«ӢжұӮзҡ„е®Ңж•ҙж—ҘиӘҢ (жӯӨйҒёй …иЁӯе®ҡзӮә 1)
EnableLogging=1 PerDayLogging=1 PerProcessLogging=1
The default logging directory is the "logs" directory underneath the "UrlScan" directory where your global filter is installed.
RemoveServerHeader=1
AllowHighBitCharacters=1
Add Header
1. Double-click on the "HTTP Response Headers" icon
2. Click on "Add..." in the Actions section
3. Add Custom HTTP Response Header
i.e.
For Name: Strict-Transport-Security For Value: max-age=31536000
URL Rewrite
[1] Download and install the URL Rewrite module.
# Works With: IIS 7, IIS 7.5, IIS 8, IIS 8.5, IIS 10
https://www.iis.net/downloads/microsoft/url-rewrite
жҮүз”Ё 1: http to https
Double-click on the "URL Rewrite" icon.
Click 'Add Rule(s)'
Select 'Blank Rule' in the Inbound section, then press OK.
In the "Match URL" section:
- Select Matches the Pattern in the Requested URL drop-down menu
- Select Regular Expressions in the Using drop-down menu
- Enter the following pattern in the Match URL section: (.*)
- Check the Ignore case boxIn the "Conditions" section:
condition input: {HTTPS}
Check if inpurt_string: Matches the Pattern
Pattern: ^OFF$
Press OKIn the Action section
Action type: Redirect
Redirect URL: https://{HTTP_HOST}{REQUEST_URI}жҮүз”Ё 2: жүҖжңү code йғҪ under subfolder
(a) Apache
RewriteRule ^$ app/webroot/ [L]
Pattern: ^app/webroot/(.*)$
Action: None (Stop processing of subsequent rules)
(b) Apache
RewriteRule (.*) app/webroot/$1 [L]
Pattern: ^(.*)$
Action: Rewrite (app/webroot/{R:1})
The {R:1} is a back-reference to the matched pattern in the URL path.
Error after sysprep
Client IIS function icon Any (i.e. HTTP Response Headers)
failed to decrypt attribute 'password'
еҺҹеӣ
Sysprep is not compatible with IIS settings with encrypted passwords.
Fix
1. Copied applicationHost.config taken before Sysprep from Physical server to VM server
C:\Windows\System32\inetsrv\config\applicationHost.config
2. Exported encryption keys from Source using the following commands:
aspnet_regiis -px "iisConfigurationKey" "C:\temp\iisConfigurationKey.xml" -pri
aspnet_regiis -px "iisWasKey" "C:\temp\iisWasKey.xml" -pri
Remark
The aspnet_regiis.exe used below can be found in the .NET Framework folder
"c:\Windows\Microsoft.NET\Framework64\<version>"
3. Imported the encryption keys retrieved from step 2 to VM server using the following commands:
aspnet_regiis -pi "iisConfigurationKey" "C:\temp\iisConfigurationKey.xml"
aspnet_regiis -pi "iisWasKey" "C:\temp\iisWasKey.xml"
static or dynamic compression
Enable: In the server's Home pane, double-click "Compression".
(еҰӮжһңжІ’жңү Compression йҒёй …еүҮиҰҒе®үиЈқ, static еҸҠ dynamic дҝӮеҲҶй–Ӣе®үиЈқзҡ„)
Settings
MaxDiskSpaceUsage
Specifies the number of megabytes of disk space that compressed files can occupy in the compression directory.
When the space used by compressed files exceeds 90 percent of the value in this attribute, IIS deletes the least recently used files until a 90-percent usage level is reached.
staticCompressionIgnoreHitFrequency # The default value is False.
If True, disables the behavior that a static file is compressed only if it is hit a certain number of times within a time period.
If the behavior is not disabled, a hit rate of greater than or equal to two hits in 10 seconds will result in compression of the static content.
A lesser hit rate would result in the content not being compressed.
staticTypes
жұәе®ҡжңғеЈ“д»Җйәј file
%SystemDrive%\inetpub\temp\IIS Temporary Compressed Files
"x-content-encoding-over-network: gzip" header
當дҪҝз”Ё ESET жҷӮ, content-encoding: gzip жңғдёҚиҰӢдәҶ
Advanced -> Internet and email -> Web Access Protection - turn off.
Application Pool
maximum worker processes
If you set the MaxProcesses value to 0, IIS uses the following formula to calculate the maximum number of worker processes:
The formula is: MaxProcesses = (Number of CPUs * Number of Cores) + 1.
иЁӯзҪ® log зҡ„ fields
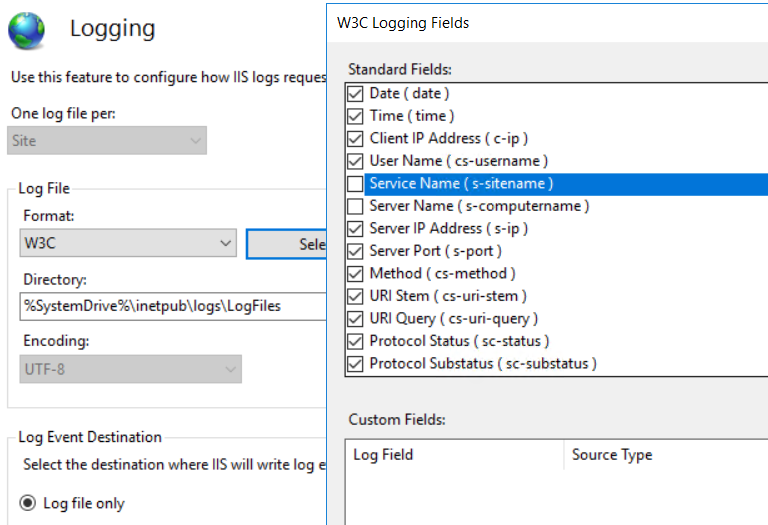
# log "HOST" field
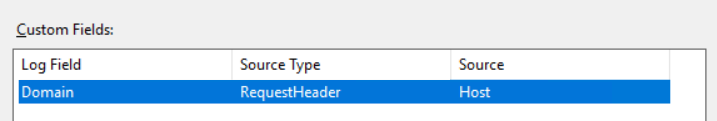
![йҰ–й Ғ Logo ¶гБВ Keith і]ӯp !!](/themes/mytheme/logo.png)