жңҖеҫҢжӣҙж–°: 2024-01-02
зӣ®йҢ„
- е®үиЈқ
- 第дёҖж¬Ўзҷ»е…Ҙ
- Debug with SyslogFacility
- е…¬з§ҒеҢҷиӘҚиӯү (authentication key)
- еҠ еј·е®үе…ЁжҖ§
- ssh login slow
- йҮҚж–°е»әз«Ӣ host key
- Alive
- sshd listen to multiple ports
- Environment Variable
- ForceCommand
- Login еҫҢ show зҡ„ message
- UsePAM
- Login еҫҢ show зҡ„ message(motd)
- Troubleshoot
е®үиЈқ
Openssh йҖҷе·Ҙе…·е…ұеҲҶзӮәе…©еҖӢеҢ…:
Server еҢ…: жҳҜжҢҮиЁӯе®ҡжӘ”еҸҠdaemon(sshd) жң¬иә«
Client еҢ…: дё»иҰҒдҝӮ ssh, scp
ServerеҢ…е®үиЈқ:
apt-get install openssh-server
дё»иҰҒзЁӢејҸ:
/usr/sbin/sshd # daemon жң¬иә«
иЁӯе®ҡжӘ”:
/etc/ssh/sshd_config
Server зҡ„е…¬з§ҒеҢҷ:
ssh_host_dsa_key.pub
ssh_host_dsa_key
ssh_host_rsa_key.pub <-- еӨҡж•ё
ssh_host_rsa_key
P.S.
當е®үиЈқ ServerеҢ…жҷӮ, е®ғеҖ‘жңғиҮӘеӢ•з”ҹжҲҗзҡ„ ~
Config Checking
/usr/sbin/sshd -t
-t Test mode. Only check the validity of the configuration file and sanity of the keys.
echo $?
0
ClientеҢ…
apt-get install openssh-client
иЁӯе®ҡжӘ”:
/etc/ssh/ssh_config
дё»иҰҒзЁӢејҸ:
/usr/bin/ssh
иј”еҠ©е·Ҙе…·:
/usr/bin/ssh-keygen
/usr/bin/scp
/usr/bin/ssh-add
/usr/bin/ssh-agent
/usr/bin/ssh-copy-id
/usr/bin/ssh-keyscan
/usr/bin/ssh-argv0
/usr/bin/sftp
/usr/bin/slogin
/usr/bin/ssh-vulnkey
第дёҖж¬Ўзҷ»е…Ҙ
еҰӮжһңдҝӮз”Ё Linux зҡ„жңӢеҸӢ, client е·Ҙе…·еҝ…然жҳҜ ssh дәҶ, дёҚз”ЁеӨҡиӘӘ
еңЁ Window дёҠ, ssh жңүеҫҲеӨҡ client дҫӣйҒёж“Ү
иҖҢжҲ‘жҳҜз”Ё pietty зҡ„
pietty е®ғжҳҜиҒһеҗҚдё–з•Ңзҡ„ putty дёӯж–ҮеҠ еј·зүҲдҫҶ,
еңЁдёӯж–Үж”ҜжҸҙж–№йқўе°Өе…¶еҮәиүІ.
當жҲ‘еҖ‘еңЁз¬¬дёҖж¬Ў login е…Ҙ ssh server жҷӮ, жҲ‘еҖ‘жңғиҰӢеҲ°
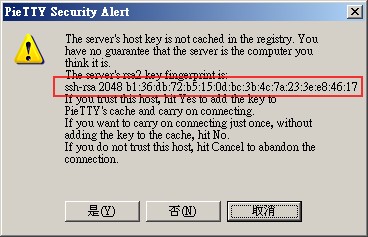
жіЁж„Ҹзҙ…еңҲйғЁд»Ҫ, еңЁдёҚеҗҢ Server, е°ұжңүдёҚз”Ёзҡ„ fingerprint.
е®ғжҳҜ ssh_host_rsa_key.pub е…¬еҢҷзҡ„жҢҮзҙӢдҫҶ,
зҗҶи«–дёҠе®ғжҳҜзҚЁдёҖз„ЎдәҢзҡ„.
жҲ‘еҖ‘жҳҜз”Ёе®ғдҫҶеҲҶиҫЁжҳҜеҗҰйҖЈдёҠзңҹжӯЈзҡ„ Server
еңЁз¬¬дәҢж¬ЎйҖЈдёҠз”ЁдёҖ Server жҷӮ, client е°ұдёҚжңғеҶҚе•Ҹ,
еӣ зӮә fingerprint 已經дҝқеӯҳеңЁ regetry иЈЎ
HKEY_CURRENT_USER\Software\SimonTatham\PuTTY\SshHostKeys
Debug with SyslogFacility
SyslogFacility AUTHPRIV LogLevel Debug
service sshd restart
е…¬з§ҒеҢҷиӘҚиӯү (authentication key)
дёҖиҲ¬жғ…жіҒдёӢ ssh жҳҜз”ЁеёіжҲ¶еҗҚеҸҠеҜҶзўјзҷ»е…Ҙзҡ„, иҖҢ authentication key жҳҜд»Ҙе…¬еҢҷеҸҠз§ҒеҢҷзҡ„еҪўејҸзҷ»е…Ҙ
еҘҪиҷ•жҳҜжҜ”ијғе®үе…Ё (е””жҖ•жҜ”дәәж’һеҜҶзўј)
дҪңжі•:
еңЁServer дёҠиЎҢ ssh-ssh-keygen е»әз«ӢеҜҶе…¬еҢҷеҸҠз§ҒеҢҷ
е®ғеҖ‘жҳҜе»әз«ӢеңЁ ./ssh зҡ„зӣ®йҢ„дёӢ, еҲҶеҲҘжҳҜ id_rsa еҸҠ id_rsa.pub
id_rsa жҳҜз§ҒеҢҷ ( иҰҒеҘҪеҘҪе°Ҹеҝғдҝқеӯҳ, дёҚз”Ёж”ҫеңЁ Server дёҠзҡ„ ),
id_rsa.pub жҳҜе…¬еҢҷ ( иҰҒж”ҫеңЁServerдёҠ )
д№ӢеҫҢжҠҠ id_rsa.pub ж”№еҗҚжҲҗ authorized_keys е°ұеҸҜд»Ҙз”Ёе®ғдҪңиӘҚиӯүд№Ӣз”Ё
( mv ~/.ssh/id_rsa.pub ~/.ssh/authorized_keys )
Server Setting
# зӣёз•¶ж–ј %h/.ssh/authorized_keys
AuthorizedKeysFile .ssh/authorized_keysVariable
- %u by the login name of the use
i.e.
AuthorizedKeysFile /etc/ssh/authorized_keys/%u
sshdзӮәдәҶе®үе…Ё, е°Қеұ¬дё»зҡ„зӣ®йҢ„е’Ңж–Ү件ж¬ҠйҷҗжңүжүҖиҰҒжұӮ.
Debug log
Authentication refused: bad ownership or modes for directory
Fix
chmod g-w /home/your_user chmod 700 .ssh chmod 600 .ssh/authorized_keys
OR
StrictModes off
authorized_keys format
# key-comment options keytype base64-encoded_key comment
options: optional. comma-separated option specifications
keytype: ssh-rsa, ssh-dss, ...
The options are supported in authorized_keys files
restrict
Enable all restrictions
i.e. disable port, agent and X11 forwarding, as well as disabling PTY allocation and execution of ~/.ssh/rc
command="cmd"
# Specifies that the command is executed whenever this key is used for authentication.
# The command supplied by the user (if any) is ignored.
# (useful to restrict certain public keys to perform just a specific operation)
# The command is run on a pty if the client requests a pty;
# otherwise it is run without a tty.
environment="NAME=value"
# The patterns may use "*" as wildcard
# CIDR address/masklen notation
# An exclamation mark ! can be used in front of a pattern to negate it.
# Support DNS Name
from="pattern-list"
i.e.
from="*.sales.example.net,!pc.sales.example.net"
no-pty
# Prevents allocation of a pseudo-tty
no-user-rc
# Disables execution of .ssh/rc when using the key.
forwarding
no-agent-forwarding
no-port-forwarding
no-x11-forwarding
permitopen="host:port" # -L option
permitlisten="[host:]port" # -R option
tunnel="n"
иӘҚиӯүж–№ејҸ
... sshd[27691]: debug1: KEX done [preauth] ... sshd[27691]: debug1: userauth-request for user MyUserName service ssh-connection method none [preauth] ... sshd[27691]: debug1: attempt 0 failures 0 [preauth] ... sshd[27691]: debug1: PAM: initializing for "MyUserName" ... sshd[27691]: debug1: PAM: setting PAM_RHOST to "IP.ctinets.com" ... sshd[27691]: debug1: PAM: setting PAM_TTY to "ssh" ... sshd[27691]: debug1: userauth_send_banner: sent [preauth] -------------------------------- ... sshd[27691]: debug1: userauth-request for user MyUserName service ssh-connection method publickey [preauth] ... sshd[27691]: debug1: attempt 1 failures 0 [preauth] ... sshd[27691]: debug1: userauth_pubkey: test whether pkalg/pkblob are acceptable for RSA SHA256:?/? [preauth] ... sshd[27691]: debug1: temporarily_use_uid: 1063/1063 (e=0/0) ... sshd[27691]: debug1: trying public key file /root/.ssh/authorized_keys ... sshd[27691]: debug1: Could not open authorized keys '/root/.ssh/authorized_keys': Permission denied ... sshd[27691]: debug1: restore_uid: 0/0 ... sshd[27691]: Failed publickey for MyUserName from R.R.R.R port 57044 ssh2: RSA SHA256:?/? -------------------------------- ... sshd[27691]: debug1: userauth-request for user MyUserName service ssh-connection method keyboard-interactive [preauth] ... sshd[27691]: debug1: attempt 2 failures 1 [preauth] ... sshd[27691]: debug1: keyboard-interactive devs [preauth] ... sshd[27691]: debug1: auth2_challenge: user=MyUserName devs= [preauth] ... sshd[27691]: debug1: kbdint_alloc: devices 'pam' [preauth]
еҠ еј·е®үе…ЁжҖ§
иЁӯе®ҡе®үе…Ё:
# root з”ЁжҲ¶дёҚеҸҜ經з”ұ ssh login
PermitRootLogin no
Opts:
- yes
- prohibit-password (default)
- without-password
- forced-commands-only (public key authentication + command)
- no
# дёҖе®ҡиҰҒз”Ёе…¬еҢҷеҸҠз§ҒеҢҷ login
PasswordAuthentication no
# еҸӘз”Ё Protocol 2
Protocol 2
# еҸӘеҸҜд»ҘзөҰеҗҢжҷӮеңЁ AllowUsers еҸҠ AllowGroups зҡ„еёіжҲ¶зҷ»е…Ҙ
# дәҰеҚіжҳҜиӘӘиҰҒеҗҢжҷӮж»ҝи¶ійҖҷе…©еҖӢжўқиҰҸеүҮ !!
# е°ұз®— PermitRootLogin yes жҷӮ, root йғҪдёҚиғҪ login
AllowUsers root sysadmin AllowGroups admin
з¶ІзөЎе®үе…Ё
йҮҚж–°е»әз«Ӣ host key
Error msg
Could not load host key: /etc/ssh/ssh_host_key
е»әз«Ӣ
ssh-keygen -A
ssh-keygen: generating new host keys: RSA1 ECDSA
* "host keys do not exist" жүҚжңғе»әз«Ӣж–°зҡ„ Key
OR
# ssh-keygen [-q] [-b bits] -t type [-N new_passphrase] [-C comment] [-f output_keyfile]
# -q Silence ssh-keygen
cd /etc/ssh
ssh-keygen -t dsa -f ssh_host_dsa_key
ssh-keygen -t rsa -f ssh_host_rsa_key
ssh-keygen -t ecdsa -f ssh_host_ecdsa_key
жҹҘзңӢ server зҡ„ fingerprint
ssh-keygen -l -f /etc/ssh/ssh_host_rsa_key.pub
Alive
make your OpenSSH server keep alive all connections with clients
# send a null packet to the other side every 30 seconds
# give up if it doesn’t receive any response after 2 tries
ClientAliveInterval 30 ClientAliveCountMax 2
sshd listen to multiple ports
Port 22 Port 2201
Performance
sshd_config
# disable dns lookup the remote host name
UseDNS no
Banner
Banner none | /path/to/file
...
VersionAddendum String....
additional text to append to the SSH protocol banner sent by the server upon connection.
telnet localhost 22
SSH-2.0-OpenSSH_7.4 Private SFTP
sshd per user configuration
e.g.
Match User USERNAME PasswordAuthentication no
дёҚжҳҜжүҖжңүзҡ„ Setting йғҪеҸҜд»Ҙ per user зҡ„, еҸӘжңүд»ҘдёӢ Setting йҒ©з”Ё
AllowAgentForwarding, AllowTcpForwarding,
AuthorizedKeysFile, AuthorizedPrincipalsFile, Banner, ChrootDirectory,
ForceCommand, GatewayPorts,
GSSAPIAuthentication,
HostbasedAuthentication, HostbasedUsesNameFromPacketOnly,
KbdInteractiveAuthentication, KerberosAuthentication,
MaxAuthTries, MaxSessions, PasswordAuthentication,
PermitEmptyPasswords, PermitOpen, PermitRootLogin, PermitTunnel,
PubkeyAuthentication,
RhostsRSAAuthentication, RSAAuthentication,
X11DisplayOffset, X11Forwarding and X11UseLocalHost.
Environment Variable
PermitUserEnvironment
# The default is no
Specifies whether "~/.ssh/environment" and "environment=" options in ~/.ssh/authorized_keys are processed by sshd
AcceptEnv
Specifies what environment variables sent by the client will be copied into the session's environ(7).
See SendEnv in ssh_config(5) for how to configure the client.
The TERM environment variable is always sent whenever the client requests a pseudo-terminal as it is required by the protocol.
Variables are specified by name, which may contain the wildcard characters ‘*’and ‘?’.
Multiple environment variables may be separated by whitespace or spread across multiple AcceptEnv directives.
Bewarned that some environment variables could be used to bypass restricted user environments.
For this reason, care should be taken in the use of this directive. The default is not to accept any environment variables.
ForceCommand
The command is invoked by using the user's login shell with the -c option.
This applies to shell, command, or subsystem execution.
Login еҫҢйЎҜзӨәзҡ„ message(motd)
/etc/motd
ж”ҜжҸҙдёӯж–Ү
"Last login" & Motd message
е®ғеҖ‘ default йғҪжҳҜ yes
/etc/ssh/sshd_config
PrintLastLog yes PrintMotd yes
~/.hushlogin
Suppress printing the "PrintLastLog" & "PrintMotd"
It does not suppress printing "Banner"
pam_motd
Example
Rocky 8 Login еҫҢжңғжңү:
Activate the web console with: systemctl enable --now cockpit.socket
# Stop е®ғ
rm -f /etc/issue.d/cockpit.issue /etc/motd.d/cockpit
UsePAM
UsePAM (Default: no)
yes: this will enable PAM authentication using ChallengeResponseAuthentication and PasswordAuthentication
in addition to PAM account and session module processing for all authentication types.
Because PAM challenge-response authentication usually serves an equivalent role to PasswordAuthentication,
You should disable either PasswordAuthentication or ChallengeResponseAuthentication.
е»әиӯ°
UsePAM yes PasswordAuthentication yes ChallengeResponseAuthentication no
* If UsePAM is enabled, you will not be able to run sshd as a non-root user.
---
ChallengeResponseAuthentication (Default: yes)
Specifies whether challenge-response authentication is allowed.
---
* PAM authentication via ChallengeResponseAuthentication may bypass the setting of
- PasswordAuthentication no
- PermitRootLogin without-password
---
WARNING: 'UsePAM no' is not supported in RHEL and may cause several problems.
History
UseLogin no # /usr/bin/login
UseLogin option is disabled by default in OpenSSH for many years
telnet е№ҙд»Јзҡ„дәӢ:
init start getty & telnetd getty opened a serial port -> login (prompt for the password) telnetd -> login (prompt for the password)
Troubleshoot
Debug ж–№ејҸ
sshd re-exec requires execution with an absolute path
зӣҙжҺҘеңЁ cli иЎҢ "sshd" дҝӮ start е””еҲ° sshd зҡ„
еҺҹеӣ :
For every new connection, sshd will re-execute itself,
to ensure that all execute-time randomisations are re-generated for each new connection.
In order for sshd to re-execute itself, it needs to know the full path to itself.
which sshd
/usr/sbin/sshd
sshd foreground debug on another port
# The server also will not fork and will only process one connection
# Multiple -d options increase the debugging level. (Maximum is 3)
/usr/sbin/sshd -d -p 9999
- -d Debug mode
- -p port 9999
[Issue] жҹҗ user login е””еҲ°
debug1: kbdint_alloc: devices 'pam' debug1: auth2_challenge_start: trying authentication method 'pam' Postponed keyboard-interactive for ???? from ::ffff:192.168.168.4 port 39132 ssh2 ... debug1: session_pty_req: session 0 alloc /dev/ttyp0 debug1: server_input_channel_req: channel 0 request shell reply 0 debug1: session_by_channel: session 0 channel 0 debug1: session_input_channel_req: session 0 req shell debug1: PAM: setting PAM_TTY to "/dev/ttyp0" debug1: Setting controlling tty using TIOCSCTTY. debug1: Received SIGCHLD. <-- е•ҸйЎҢдҫҶдәҶ debug1: session_by_pid: pid 4273 debug1: session_exit_message: session 0 channel 0 pid 4273 debug1: session_exit_message: release channel 0 debug1: session_close: session 0 pid 4273 debug1: session_by_tty: session 0 tty /dev/ttyp0 debug1: session_pty_cleanup: session 0 release /dev/ttyp0 debug1: channel 0: free: server-session, nchannels 1 Connection closed by ::ffff:192.168.168.4 debug1: do_cleanup debug1: PAM: cleanup Closing connection to ::ffff:192.168.168.4 debug1: PAM: cleanup
Fix
cat /etc/shells # жҹҘзңӢзі»зөұжңүд»Җйәј Shell
usermod -s /bin/bash USERNAME
[Issue] ssh login slow
log:
Jul 22 10:44:20 myserver sshd(pam_unix)[25925]: session opened for user root by (uid=0) Jul 22 10:44:20 myserver sshd[25927]: nss_ldap: reconnecting to LDAP server (sleeping 4 seconds)... Jul 22 10:44:20 myserver sshd[25927]: nss_ldap: reconnecting to LDAP server (sleeping 8 seconds)... ...................
[fix] Speed up SSH logon
GSSAPIAuthentication
GSSAPIAuthentication no
Generic Security Services API. In SSH's case its designed to talk to Kerberos.
GSSAPI is a IETF standard for doing strong encrypted authentication in network based applications.
OPENssh uses this API and the underlying kerberos 5 code to provide a alternative means of authentication other than ssh_keys.
# The "-v" maximum is 3
ssh -vvv
debug3: preferred gssapi-keyex,gssapi-with-mic,gssapi,publickey,keyboard-interactive,passwordnsswitch
еңЁ nsswitch.conf е…§еҒңз”Ё ldap
/etc/nsswitch.conf
passwd: files shadow: files group: files
[Issue]
sshd:Privilege separation user sshd does not exist
и§Јжұә
UsePrivilegeSeparation no
иӘӘжҳҺ
The default is ''yes''.
sshd separates privileges by creating an unprivileged child process to deal with incoming network traffic.
After successful authentication, another process will be created that has the privilege of the authenticated user.
The goal of privilege separation is to prevent privilege escalation by containing any corruption within the unprivileged processes.
[Issue]
OS: Centos 6
/var/log/secure
sshd[400]: fatal: daemon() failed: No such device
жІ’жңү /dev/null
[Issue]
OS: Centos 7
ssh жҷӮиҰӢеҲ°е®ғжҷӮиҰӢеҲ°
... Server refused to allocate pty
жҹҘзңӢ
ls -la /dev/pts/*
lsof /dev/pts/*
/var/log/secure
error openpty read-only file system
mount | grep devpts
mount -t devpts devpts /dev/pts
mount -t devpts -o remount,rw,nosuid,noexec,relatime,uid=0,gid=5,mode=620 devpts /dev/pts
![йҰ–й Ғ Logo ¶гБВ Keith і]ӯp !!](/themes/mytheme/logo.png)