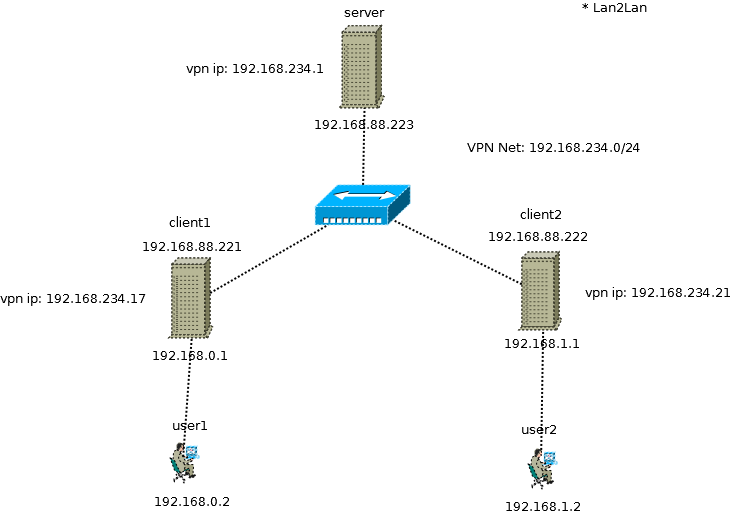
Diagram
server.conf
# By default clients will not see each other.
client to client # е»әз«Ӣ route еҺ»е…©еҖӢ client йӮЈиЈЎеҺ» # The server needs to route this IP range through the tunnel # --route network [netmask] [gateway] [metric] # Add route to routing table after connection is established. # Multiple routes can be specified. Routes will be automatically torn down in reverse order prior to TUN/TAP device close. route 192.168.0.0 255.255.255.0 route 192.168.1.0 255.255.255.0
per client configure зҡ„ iroute
Client1:
# иҮӘе·ұйӮЈйӮҠ IP iroute 192.168.0.0 255.255.255.0 # еҸҰдёҖйӮҠ IP route 192.168.1.0 255.255.255.0
iroute
-- iroute only works with tun-style tunnels
log
--iroute options rejected for tim/115.160.172.18:1194
--iroute essentially defines a subnet which is owned by a particular client
Iroute does not bypass or alter the kernel's routing table, it allows openvpn to know it should handle the routing when the kernel points to it but the network is not one that openvpn knows about. The iroute entry tells the openvpn server which client is responsible for the network. Without the iroute entry you will find the following in your logfiles:
MULTI: bad source address from client [IP ADDRESS], packet dropped
IP ADDRESS in that case would be the machine on client LAN which tried to talk through vpn, because openVPN has no clue what that address is. Once you give it the iroute statement, that changes. Iroute is a route internal to openVPN, and has nothing to do with the kernel's routing table. It tells the openvpn server which client owns which network. Note that even if you only have 1 lan behind 1 client, YOU STILL NEED IROUTE. You will need it any time a clients source IP address is different from the IP given to it by the vpn server.
--iroute directive also has an important interaction with --push "route ..."
In order for all clients to see A's subnet, OpenVPN must push route(--route) to all clients EXCEPT for A, since the subnet is already owned by A(--iroute).
"comp-lzo" зҡ„ per-user иЁӯе®ҡ
Server per client setting (--client-config-dir file)
comp-lzo yes push "comp-lzo yes"
client side configure file:
# еҚідҪҝжҳҜ "no" client дәҰиҰҒжңүйҖҷиЁӯе®ҡ comp-lzo no
iptables
iptables -I INPUT -i tun0 -j ACCEPT iptables -I OUTPUT -o tun0 -j ACCEPT iptables -I FORWARD -o tun0 -j ACCEPT iptables -I FORWARD -i tun0 -j ACCEPT
Addressing Basics for Server/Client
- subnet
- net30
- p2p
Static Address Assignment (ccd)
--ifconfig-push local remote-netmask [alias]
* Push virtual IP endpoints for client tunnel
* overriding the --ifconfig-pool dynamic allocation.
It is possible to have the server allocate a static IP to a client based on its commonName. This is done by way of an
Example:
# ccd-dir/client1
ifconfig-push 192.168.234.17 192.168.234.18
performance_test
![йҰ–й Ғ Logo ¶гБВ Keith і]ӯp !!](/themes/mytheme/logo.png)