жңҖеҫҢжӣҙж–°: 2018-05-04
зӣ®йҢ„
- postfix - TLS (Port 587)
- Disable SSL2, SSL3, TLS1.0, TLS1.1
- Secure SMTP (SSMTP) (Port 465)
- Outlook SSL иЁӯе®ҡ
- Check Postfix Support TLS
- smtpd (incoming)
- smtp (Outgoing)
- TLS Policy Table
- дҝқиӯ· TLS Connection
- Troubleshoot
- Doc
д»Ӣзҙ№
SMTP Port
- TLS (Port 587)
- Secure SMTP (SSMTP) - port 465
postfix - TLS (Port 587)
main.cf
# STARTTLS support to remote SMTP clients # By default, TLS is disabled in the Postfix SMTP server # Postfix >= 2.3 use smtpd_tls_security_level instead smtpd_use_tls = yes smtpd_tls_cert_file = /etc/postfix/ssl/server.cert smtpd_tls_key_file = /etc/postfix/ssl/server.key
Cert. file permission
-rw-r----- 1 root root 1675 Jun 21 16:46 server.key -rw-r--r-- 1 root root 1663 Jun 21 16:46 server.cert
# Postfix SMTP server announces STARTTLS support to remote SMTP clients. Not force to use
smtpd_tls_security_level = may
opts
- none # TLS will not be used
- may # announce STARTTLS support to remote SMTP clients (Opportunistic)
- encrypt # Mandatory TLS encryption
Checking & Log:
main.cf
smtpd_tls_loglevel = 1
log:
... setting up TLS connection from unknown[x.x.x.x]
... Anonymous TLS connection established from unknown[x.x.x.x]:
TLSv1 with cipher AES128-SHA (128/128 bits)
е»әз«Ӣ SSL/TLS зҡ„ Cert
mkdir /etc/postfix/ssl; cd /etc/postfix/ssl
openssl req -new -x509 -days 3650 -keyout server.x -out server.crt
touch server.key; chmod 600 server.key
openssl rsa -in server.x > server.key
rm server.x
Disable SSLv2, SSLv3
smtpd_tls_protocols = !SSLv2, !SSLv3, !TLSv1, !TLSv1.1 smtpd_tls_mandatory_protocols = !SSLv2, !SSLv3, !TLSv1, !TLSv1.1
еҲҶеҲҘ
smtpd_tls_mandatory_protocols = mandatory TLS encryption
Secure SMTP (SSMTP) (Port 465)
TLS is sometimes used in the non-standard "wrapper" mode where a server always uses TLS
дҝ®ж”№ /etc/postfix/master.conf
-o smtpd_tls_wrappermode=yes
... mail postfix/smtpd[30891]: connect from CLIENT_IP[CLIENT_IP]
... mail postfix/smtpd[30891]: setting up TLS connection from CLIENT_IP[CLIENT_IP]
... mail postfix/smtpd[30891]: Anonymous TLS connection established from CLIENT_IP[CLIENT_IP]:
TLSv1 with cipher RC4-MD5 (128/128 bits)Telnet дәӮжү“еӯ—:
... case2square postfix/smtpd[7370]: warning: TLS library problem:
7370:error:140760FC:SSL routines:SSL23_GET_CLIENT_HELLO:unnown protocol:s23_srvr.c:578:Login Fail:
warning: unknown[115.160.172.18]: SASL LOGIN authentication failed: UGFzc3dvcmQ6
Open relay жё¬и©Ұ:
... case2square postfix/smtpd[7520]: NOQUEUE: reject: RCPT from unknown[x.x.x.x]: 554 5.7.1 <to_mail>:
Relay access denied; from=<test_mail> to=<to_mail> proto=ESMTP helo=<lwyPC>
Outlook SSL иЁӯе®ҡ

ж¬Ўж¬ЎйғҪе•Ҹ
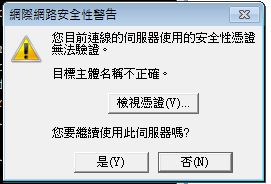
жңӘзӯ”жҳҜ/еҗҰжҷӮзҡ„ Server log
... SERVER dovecot: imap-login: Disconnected (no auth attempts): rip=R.R.R.R, lip=L.L.L.L,
TLS: SSL_read() syscall failed: Connection reset by peer
Check Postfix Support TLS
ldd /usr/libexec/postfix/smtp | grep libssl
libsasl2.so.2 => /usr/lib/libsasl2.so.2 (0x00322000)
libssl.so.10 => /usr/lib/libssl.so.10 (0x00cd0000)
libcrypto.so.10 => /usr/lib/libcrypto.so.10 (0x0033d000)
smtpd (incoming) TLS
/etc/postfix/main.cf
# must be in "PEM" format (RSA, DSA, ECDSA) # This file may also contain the Postfix SMTP server private RSA key. # intermediate CAs: cat server_cert.pem intermediate_CA.pem > server.pem smtpd_tls_cert_file = /etc/postfix/ssl/server.pem # chmod 440 server.key smtpd_tls_key_file = /etc/postfix/ssl/server.key # yes: announce STARTTLS support, but do not require. # Default: no # еңЁ postfix 2.3 еҫҢ, з”Ё smtpd_tls_security_level еҺ» control smtpd_use_tls = yes # Default: no # require that clients use TLS encryption (Mandatory TLS) # "smtpd_enforce_tls = yes" implies "smtpd_tls_auth_only = yes". smtpd_enforce_tls = no # default: empty # none: TLS will not be used. # may: Opportunistic TLS # encrypt => require that clients use TLS encryption (implies "smtpd_tls_auth_only = yes") # 當 "smtpd_tls_security_level=none" зі»зөұе°ұе””жңғ announce "STARTTLE" smtpd_tls_security_level = may # do not announce or accept SASL authentication over unencrypted connections. # plantext login "must issue a starttls command first" # default: no smtpd_tls_auth_only = no # Log # (default: 0) 0 = Log only a summary message on TLS handshake completion smtpd_tls_loglevel = 0
smtp (Outgoing) TLS
/etc/postfix/main.cf
# Mandatory TLS encryption setting smtp_tls_security_level = may
none - No TLS. TLS will not be used unless enabled for specific destinations via smtp_tls_policy_maps.
may - Opportunistic TLS. Use TLS if this is supported by the remote SMTP server, otherwise use plaintext.
TLS Policy Table
/etc/postfix/main.cf
# Default: NULL smtp_tls_policy_maps = hash:/etc/postfix/outgoing_tls_policy # 1 Log only a summary message on TLS handshake completion # 2 Also log levels during TLS negotiation. smtp_tls_loglevel = 0
TLS policy table
The TLS policy table is indexed by the full next-hop destination
* which is either the recipient domain, or the verbatim next-hop specified in the transport table
/etc/postfix/outgoing_tls_policy
example.edu none example.com verify example.gov encrypt
* parent domain starting with a leading "." is matched recursively (".example.com encrypt")
opts
none No TLS
may Opportunistic TLS
encrypt TLS encryption is always used, mail delivery continues even if the server certificate is untrusted
verify Mandatory server certificate verification
Mail is delivered only if the TLS handshake succeeds
(not expired or revoked, and signed by a trusted Certification Authority)
# жҢҮе®ҡз”Ёе…¶д»– Domain
.example.net secure match=.example.net:example.net
fingerprint
there are no trusted Certification Authorities.
[thumb.example.org] fingerprint
match=EC:3B:2D:B0:5B:B1:FB:6D:20:A3:9D:72:F6:8D:12:35
match=3D:95:34:51:24:66:33:B9:D2:40:99:C0:C1:17:0B:D1е»әз«Ӣ map
postmap hash:/etc/postfix/outgoing_tls_policy
log
... certificate verification failed for w.y.z[x.x.x.x]:25: untrusted issuer /C=SE/O=AddTrust AB/OU=AddTrust External TTP Network/CN=AddTrust External CA Root
дҝқиӯ· TLS Connection
# Fix 'The Logjam Attack'.
smtpd_tls_exclude_ciphers = aNULL, eNULL, EXPORT, DES, RC4, MD5, PSK, aECDH, EDH-DSS-DES-CBC3-SHA, EDH-RSA-DES-CDC3-SHA, KRB5-DE5, CBC3-SHA
dh жӘ” (forward secrecy)
# Postfix ≥ 2.2 support 1024-bit-prime EDH out of the box, with no additional configuration
smtpd_tls_X_param_file => To use a non-default prime (жӯӨиЁӯе®ҡдҝӮжңүй—ң EDH ж–№ејҸ)
( for improved security against pre-computation attacks )
е»әз«Ӣ dh жӘ”
# mkdir /etc/postfix/tls; cd /etc/postfix/tls
openssl dhparam -out dh512.pem 512
openssl dhparam -out dh2048.pem 2048
# smtpd_tls_dh1024_param_file еҸҜз”Ё 1024 bit / 2048 bit жӘ”(е»әиӯ°з”Ё 2048 bit зҡ„)
smtpd_tls_dh512_param_file = /etc/postfix/tls/dh512.pem smtpd_tls_dh1024_param_file = /etc/postfix/tls/dh2048.pem
Checking
smtp_tls_loglevel = 1 smtpd_tls_loglevel = 1
Or
smtpd_tls_received_header = yes
еҸғиҖғ
https://datahunter.org/dh
Troubleshoot
Error1:
TLS not available due to local problem
Solution1:
mkdir /etc/postfix/tls
cd /etc/postfix/tls
openssl req -new -x509 -nodes -out smtpd.crt -keyout smtpd.key -days 3650
openssl dhparam -out dh1024.pem 1024
chmod 440 smtpd.key dh1024.pem
smtpd_tls_dh1024_param_file = /etc/postfix/tls/dh1024.pem smtpd_tls_CAfile = /etc/postfix/tls/smtpd.crt smtpd_tls_cert_file = /etc/postfix/tls/smtpd.crt smtpd_tls_key_file = /etc/postfix/tls/smtpd.key
Doc
http://www.postfix.org/TLS_README.html
![йҰ–й Ғ Logo ¶гБВ Keith і]ӯp !!](/themes/mytheme/logo.png)