жңҖеҫҢжӣҙж–°: 2016-09-14
зӣ®йҢ„
- NAT Rule
- service-port(NAT helpers)
- PPTP with NAT
- NAT Action
- hairpin
NAT Rule
List nat rule
/ip firewall nat
/ip firewall nat print stats
Add Port forwarding By CLI
Public IP: 10.5.8.200
Local IP: 192.168.0.109
/ip firewall nat add chain=dstnat dst-port=1234 action=dst-nat protocol=tcp to-address=192.168.1.1 to-port=1234
Add Port forwarding By GUI
Tab1
Chian: dstnat
Protocol: tcp
dst-port=1234 => "еҝ…й ҲеЎ« !!!"
Tab4
Action: dst-nat
to-address => LAN_IP_ADDR
to-port => Server_Listen_Port
service-port(NAT helpers)
Hosts behind a NAT-enabled router do not have true end-to-end connectivity.
Therefore some Internet protocols might not work in scenarios with NAT.
To overcome these limitations RouterOS includes a number of NAT helpers,
that enable NAT traversal for various protocols.
Helper: ftp, pptp, sip ...
/ip firewall service-port enable pptp
PPTP with NAT
PPTP uses port 1723 as well as protocol 47. You need to allow this thru the forward chain.
Also, turn on the IP services (helper) for pptp - it will allow nat traversal of GRE(protocol 47).
Its the only way to have more than 1 PPTP behind a NAT.
NAT Action
dst-nat - replaces destination address and/or port of an IP packet to values specified by to-addresses and to-ports parameters
masquerade - replace source address of an IP packet to IP determined by routing facility.
src-nat - replaces source address of an IP packet to values specified by to-addresses and to-ports parameters
netmap - creates a static 1:1 mapping of one set of IP addresses to another one. Often used to distribute public IP addresses to hosts on private networks
redirect - replaces destination port of an IP packet to one specified by to-ports parameter and destination address to one of the router's local addresses
same - gives a particular client the same source/destination IP address from supplied range for each connection.
This is most frequently used for services that expect the same client address for multiple connections from the same client
Notes
еңЁ nat д№ӢеүҚжңү accept
accept - accept the packet. Packet is not passed to next NAT rule.
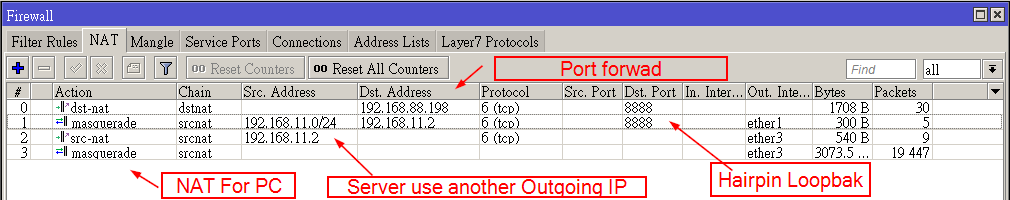
hairpin
еҒҮиЁӯжңү NAT
/ip firewall nat
add chain=dstnat dst-address=W.W.W.W protocol=tcp dst-port=80 \
action=dst-nat to-address=192.168.1.2
# дёҠз¶І
add chain=srcnat out-interface=WAN action=masquerade* W.W.W.W жҳҜ ether1 еҸЈзҡ„ Wan IP. еҰӮжһңжІ’жңүеӣәе®ҡ IP е°ұиҰҒз”Ё in-interface=ether1 еҸ–д»Ј
hairpin loopback
* еңЁ NAT д№ӢеҫҢеҠ
/ip firewall nat add chain=srcnat src-address=192.168.1.0/24 \ dst-address=192.168.1.2 protocol=tcp dst-port=80 \ out-interface=LAN action=masquerade
Notes
* еҰӮжһң dst-nat зҡ„ rule дҝӮз”Ё "in-interface=ether1" иҖҢдёҚжҳҜ "dst-address=W.W.W.W"
йӮЈиҰҒеҠ еӨҡжўқ rule зӣёеҗҢзҡ„ rule, еҸӘдёӯ in-interface ж”№жҲҗ bridge1
* з”ұж–јдҪҝз”Ё srcnat з”ЁдёҚдәҶ in-interface, жүҖд»ҘиҰҒйҷҗ src-address
* dst-address еҸҠ dst-port дҝӮ nat еҫҢзҡ„зөҗжһң
иЁӯе®ҡ Example
Doc
https://wiki.mikrotik.com/wiki/Manual:IP/Firewall/NAT
![йҰ–й Ғ Logo ¶гБВ Keith і]ӯp !!](/themes/mytheme/logo.png)