жңҖеҫҢжӣҙж–°: 2022-07-19
д»Ӣзҙ№
VPN Protocols Supported by SoftEther VPN Server
- SoftEther VPN Protocol (Ethernet over HTTPS)
- OpenVPN (L3-mode and L2-mode)
- L2TP/IPsec
- MS-SSTP (Microsoft Secure Socket Tunneling Protocol)
- L2TPv3/IPsec
- EtherIP/IPsec
Home Page: https://www.softether.org/
зӣ®йҢ„
- Install
- иЁӯе®ҡиӘһиЁҖ
- Start & Stop
- Config file & Admin ACL
- Command-Line Utility
- Changing the Manager Password
- Cipher Suite
- Logs
- Firewall Port
- Save all volatile data
- ...
- AccessList
- AccessList
- Route traffic to another side
- OpenVPN
- Reset Administrator Password
- Reset Statistics
- Access Server after VPN
- Upgrade
- Changelog
- Doc
Install
Download
https://www.softether.org/5-download
RTM Version
RTM stands for release to manufacturing
Compile
yum groupinstall "Development Tools" -y
cd /opt
tar -zxf softether-vpnserver-v4.20-9608-rtm-2016.04.17-linux-x64-64bit.tar.gz
cd /opt/vpnserver
make
Start & Stop
./vpnserver start
./vpnserver stop
Startup script
/etc/init.d/vpnserver
#!/bin/sh
# chkconfig: 2345 99 01
# description: SoftEther VPN Server
DAEMON=/opt/vpnserver/vpnserver
LOCK=/var/lock/subsys/vpnserver
test -x $DAEMON || exit 0
case "$1" in
start)
$DAEMON start
touch $LOCK
;;
stop)
$DAEMON stop
rm $LOCK
;;
restart)
$DAEMON stop
sleep 3
$DAEMON start
;;
*)
echo "Usage: $0 {start|stop|restart}"
exit 1
esac
exit 0Auto Start
chmod 755 /etc/init.d/vpnserver
chkconfig --add vpnserver # Centos
service vpnserver start # Centos
chkconfig vpnserver on
Checking
netstat -ntlp | grep 5555
ps aux | grep vpnserver
Ubuntu Version
/etc/init.d/vpnserver
### BEGIN INIT INFO # Provides: vpnserver # Required-Start: $network $local_fs # Required-Stop: $network $local_fs # Default-Start: 2 3 4 5 # Default-Stop: 0 1 6 # Short-Description: SoftEther VPN Server ### END INIT INFO ...
systemctl start vpnserver
systemctl enable vpnserver
иЁӯе®ҡиӘһиЁҖ
lang.config
# ja: Japanese (ж—Ҙжң¬иӘһ) # en: English (English) # cn: Simplified Chinese (з®ҖдҪ“дёӯж–Ү) en
Config file & Admin ACL
Administration Tools
* vpncmd.exe # CLI
* vpnsmgr.exe # GUI
Virtual Hubs
* Multiple Virtual Hubs can be created in the SoftEther VPN Server.
* Each Virtual Hub has an independent layer 2 segment and is incapable of communicating with the others.
е®ғеҖ‘жңүеҗ„иҮӘзҡ„ user authentication database and access list, SecureNAT settings and cascade connection settings
Admin Level:
- Administration Authority for the Entire SoftEther VPN Server
- Virtual Hub Administration Authority (enabling the delegation of authority )
Config File
vpn_server.config
* permission must 600
第дёҖж¬ЎиЎҢ vpnserver жүҚжңғе»әз«Ӣ
# The VPN Server service must be manually stopped in the following cases
* When manually editing or replacing the configuration file
* When updating the vpnserver program and other files after the release of a new version of VPN Server
(To replace the vpnserver, vpncmd and hamcore.se2 files, be sure to stop the service in advance.)
* When you want to restart the service due to erratic behavior of the operating VPN Server
Administration Connection Source IPs ACL
* е»әз«Ӣ adminip.txt дёҚз”Ё restart softehter е°ұз”ҹж•Ҳ
* з©әзҡ„ adminip.txt жңғд»ӨжүҖжңүдәәйғҪ admin е””еҲ°
echo 127.0.0.1 >> adminip.txt
adminip.txt
# localhost can access ALL Virtual Hubs
127.0.0.1
# Granting 2.11 access HUB1, 3.11 access HUB2
192.168.2.11 HUB1
192.168.3.11 HUB2
Command-Line Utility
./vpncmd [host:port] [OPTS] [/CMD commands...]
By using vpncmd program, the following can be achieved
1. Management of VPN Server or VPN Bridge
2. Management of VPN Client
3. Use of VPN Tools (certificate creation and Network Traffic Speed Test Tool)
# help
./vpncmd --help
VPN Server> BridgeCreate?
OPTS:
mode
- /CLIENT # This will connect to VPN Client to do management.
- /SERVER # This will connect to VPN Server or VPN Bridge
- /TOOLS
еҰӮжһңдёҚеЎ«, е°ұжңғе•Ҹ
By using vpncmd program, the following can be achieved. 1. Management of VPN Server or VPN Bridge 2. Management of VPN Client 3. Use of VPN Tools (certificate creation and Network Traffic Speed Test Tool)
/HUB:hub # When connecting to the VPN Server by "Virtual Hub Admin Mode", this specifies the Virtual Hub name 'hub'.
# not the /HUB parameter, connection will be by "Server Admin Mode".
/PASSWORD:password # If the administrator password is required when connecting
i.e.
# зӣҙйҖЈдёҚе•Ҹе•ҸйЎҢ
./vpncmd localhost /server
Get Vesion & Check Operations
Version
VPN Server>ServerInfoGet
... Version |Version 4.25 Build 9656 (English) ...
VPN Server>check
Checking 'Kernel System'...
Pass
Checking 'Memory Operation System'...
Pass
Checking 'ANSI / Unicode string processing system'...
Pass
Checking 'File system'...
Pass
Checking 'Thread processing system'...
Pass
Checking 'Network system'...
Pass
Changing the Manager Password
# At the time VPN Server is installed, the manager password for the entire VPN Server is not set
VPN Server>ServerPasswordSet
Cipher Suite
Get
ServerCipherGet
Encrypted Algorithm Currently Used by VPN Server:
RC4-MD5
List of Usable Encrypted Algorithm Names:
RC4-MD5 (weakest)[default]
RC4-SHA
...
DHE-RSA-AES128-SHA
DHE-RSA-AES256-SHA (strongest)Set
ServerCipherSet DHE-RSA-AES128-SHA
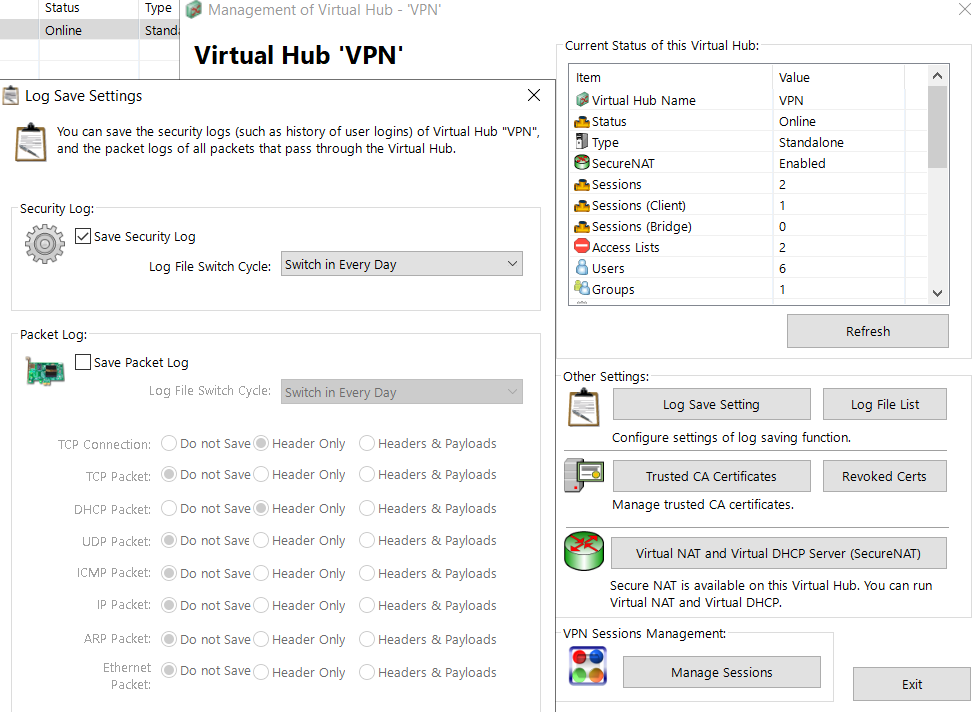
Logs
* All logs are set with a one day switch save cycle in default.
* еҸҜд»ҘеңЁ GUI download log file (Virtual Hub 'X' -> Log File List)
All log files create the three subdirectories
- packet_log
- server_log
- security_log
Server Log
Copies of each of the Virtual Hubs' security logs are saved together in the server log
so that even if a Virtual Hub Administrator sets the security log not to be saved,
it is always saved automatically in the server log
SecureNAT Log
The entire status of SecureNAT's Virtual NAT and Virtual DHCP Server functions are saved in the Virtual Hub's security log.
2019-08-14 18:01:57.487 SecureNAT: The TCP session 1814 has been created.
Connection source 192.168.30.10:31659,
Connection destination D.D.D.D:443...
2019-08-14 18:02:47.618 SecureNAT: The TCP session 1814 has been deleted.Setting
Firewall Port
# Panel (443)
firewall-cmd --add-port=443/tcp --permanent
# L2TP Firewall
UDP 500 and 4500
firewall-cmd --add-port=500/udp --permanent
firewall-cmd --add-port=4500/udp --permanent
Save all volatile data
Flush
Username to login
If the destination Virtual Hub Name in the login-attempting username is omitted,
=> then the "default Virtual Hub" is to be assumed to be designated by the user.
Login format
user@hub
cmd
UserCreate - Create User
UserDelete - Delete User
UserGet - Get User Information
UserList - Get List of Users
UserPasswordSet - Set Password Authentication for User
UserSet - Change User Information
i.e.
UserList
Item |Value ----------------+------------------------- User Name |datahunter Full Name | Group Name |- Description | Auth Method |Password Authentication Num Logins |3 Last Login |2016-12-02 (Fri) 10:36:40 Expiration Date |No Expiration Transfer Bytes |1,314,678 Transfer Packets|16,969
Group
VPN Server/DEFAULT>GroupList
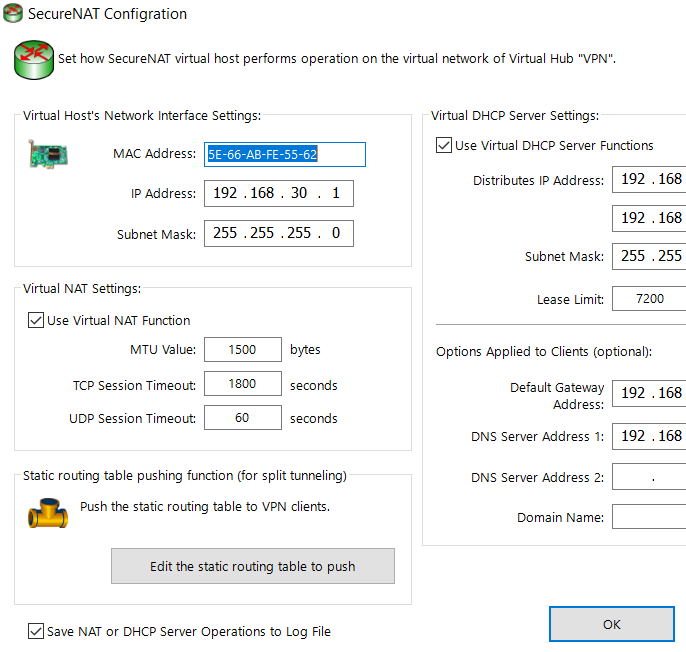
Virtual NAT Function
A Virtual Hub on SoftEther VPN Server / Bridge has "Virtual NAT Function" .
Virtual NAT Function can share a single IP address on the physical network by multiple private IP address of VPN Clients.
There are two operation mode of Virtual NAT: User-mode and Kernel-mode.
In the user-mode operation, Virtual NAT shares an IP address which is assigned on the host operating system.
Unlike user-mode, the kernel-mode operation attempts to find DHCP servers on the physical network.
If there are two or more physical networks, a DHCP server will be sought automatically for each segments serially.
If a DHCP server found, and an IP address is acquired, the IP address will be used by the Virtual NAT.
In this case, an IP entry as a DHCP client will be registered on the IP pool of the physical DHCP Server.
The physical default gateway and the DNS server will be used by the Virtual NAT in order to communicate with hosts in Internet.
In kernel-mode operation, a Virtual Hub has a virtual MAC address which is operating on the physical Ethernet segment.
In order to check the connectivity to Internet, SoftEther VPN periodically sends DNS query packet to resolve the IP address of host
"www.yahoo.com" or "www.baidu.com" , and attempts to connect to the TCP port 80 of such a resulted IP address for connectivity check.
Hub Config
# By default, only one Virtual Hub, named "DEFAULT", is registered to VPN Server.
Hub - Select Virtual Hub to Manage
HubCreate - Create New Virtual Hub
HubCreateDynamic - Create New Dynamic Virtual Hub (For Clustering)
HubCreateStatic - Create New Static Virtual Hub (For Clustering)
HubDelete - Delete Virtual Hub
HubList - Get List of Virtual Hubs
HubSetDynamic - Change Virtual Hub Type to Dynamic Virtual Hub
HubSetStatic - Change Virtual Hub Type to Static Virtual Hub
# Server Management Mode
VPN Server>
# жҹҘзңӢжңүд»Җйәј Hub
HubList
HubList command - Get List of Virtual Hubs Item |Value ------------------+------------------- Virtual Hub Name |VPN Status |Online Type |Standalone Users |6 Groups |1 Sessions |2 MAC Tables |2 IP Tables |4 Num Logins |21 Last Login |2019-08-14 17:00:25 Last Communication|2019-08-14 17:24:55 Transfer Bytes |4,850,222,176 Transfer Packets |12,134,775 The command completed successfully.
# Virtual Hub management mode (з®ЎзҗҶжҹҗ Hub)
VPN Server>Hub DEFAULT
Hub command - Select Virtual Hub to Manage The Virtual Hub "DEFAULT" has been selected. The command completed successfully.
VPN Server/DEFAULT>
# иҝ”еӣһ Server Management Mode
VPN Server/DEFAULT> Hub
# Online / Offline
VPN Server/DEFAULT> Online
VPN Server/DEFAULT> Offline
# Reboot
# All currently connected sessions and TCP connections will be disconnected
Reboot
# Status
# VPN Server/DEFAULT>StatusGet
Item |Value
-----------------------------+--------------------
Virtual Hub Name |DEFAULT
Status |Online
Type |Standalone
SecureNAT |Disabled
Sessions |2
Sessions (Client) |1
Sessions (Bridge) |0
Access Lists |0
Users |1
Groups |0
MAC Tables |43
IP Tables |62
Num Logins |14
Last Login |2016-12-14 15:55:03
Last Communication |2016-12-14 16:18:20
Created at |2016-12-01 17:14:35
Outgoing Unicast Packets |9,425,809 packets
Outgoing Unicast Total Size |624,561,195 bytes
Outgoing Broadcast Packets |105,306 packets
Outgoing Broadcast Total Size|12,880,646 bytes
Incoming Unicast Packets |495,020,812 packets
Incoming Unicast Total Size |63,519,669,474 bytes
Incoming Broadcast Packets |7,013,868 packets
Incoming Broadcast Total Size|829,330,357 bytesPolicy
VPN Server/DEFAULT>PolicyList
Access
# The access list is a set of packet file rules that are applied to packets that flow through the Virtual Hub.
VPN Server/DEFAULT>AccessList
AcL
VPN Server/DEFAULT>AcList
to allow or deny connection from a VPN Client when this client attempts connection to the Virtual Hub
Mac & Ip
# built by the Virtual Hub automatically analyzing the contents of the communication throughput.
VPN Server/DEFAULT>MacTable
Item |Value ------------+--------------------- ID |406811166 Session Name|SID-LOCALBRIDGE-2 VLAN ID |- MAC Address |34-12-98-71-62-4F Created at |2016-12-14 16:01:27 Updated at |2016-12-14 16:01:39 Location |On 'softether.local'
# automatically generated by analyzing the contents of communication
VPN Server/DEFAULT>IpTable
ID |896073399 Session Name|SID-LOCALBRIDGE-2 IP Address |192.168.88.236 Created at |2016-12-05 16:20:53 Updated at |2016-12-14 16:27:17 Location |On 'softether.local'
SecureNat
VPN Server/DEFAULT>SecureNatStatusGet
Item |Value -------------------------+--------- Virtual Hub Name |DEFAULT NAT TCP/IP Sessions |0 Session NAT UDP/IP Sessions |0 Session NAT ICMP Sessions |0 Session NAT DNS Sessions |0 Session Allocated DHCP Clients |0 Client Kernel-mode NAT is Active|No Raw IP mode NAT is Active|No The command completed successfully.
VPN Server/DEFAULT>DhcpGet
Item |Value -------------------------------+-------------- Use Virtual DHCP Function |Yes Start Distribution Address Band|192.168.30.10 End Distribution Address Band |192.168.30.200 Subnet Mask |255.255.255.0 Lease Limit (Seconds) |7200 Default Gateway Address |192.168.30.1 DNS Server Address 1 |192.168.30.1 DNS Server Address 2 |None Domain Name | Save NAT and DHCP Operation Log|Yes Static Routing Table to Push |
* иҰҒ Enable SecureNAT Function жүҚжңү DHCP function
Hub Preformance turning
VPN Server/DEFAULT>SetMaxSession 64
Local Bridging
Local Bridging
-------------------
| [vhub] --- NIC |
-------------------
Local bridging is used to connect a virtual network and a physical network on the Ethernet level(layer 2).
Multiple local bridges can be created, although it is not possible to register the same Virtual Hub/ physical network adapter
# NIC Requirements
Operate in promiscuous mode
If the Promiscuous Mode (MAC Address Spoofing) is administratively disabled,
the Local Bridge function between a Virtual Hub on the VPN Server and a physical network adapter on the physical computer does not work well.
You should allow the Promiscuous Mode (MAC Address Spoofing) by using the configuration tool of the VM.
# NIC Setting (Disable Protocol Stack)
Where there is a network adapter prepared on the computer for use exclusively in local bridging,
it is recommended that the TCP/IP protocol and other protocol stacks be disabled on that network adapter to enhance performance.
( both the frame buffer copied )
No Protocol Stack is Used for the Local Bridge Network Adapter
Where there is a network adapter prepared on the computer for use exclusively in local bridging,
it is recommended that the TCP/IP protocol and other protocol stacks be disabled on that network adapter to enhance performance.
The role of the local bridge network adapter is to release Ethernet frames between the Virtual Hub and the physical LAN,
entirely without the need for intervention from the protocol stack of the OS running the Virtual Hub.
Linux:
assigning an IP address of 0.0.0.0 to the local bridge network adapter.
# Local Bridge Sessions
Local bridge sessions are virtual sessions created automatically
for the Virtual Hub by the VPN Server in order to connect the Virtual Hub and physical network adapter.
# VPN Bridge does not have the following functions of VPN Server
Function for receiving a VPN connection (as a VPN server) and associated functions
Function for creating several Virtual Hubs
Virtual Layer 3 switching function
Packet filtering function using the access list
# Get List of Network Adapters Usable as Local Bridge
BridgeDeviceList
ens192
# List Hub
HubList
Item |Value ------------------+------------------- Virtual Hub Name |DEFAULT Status |Online ...........
# Create Local Bridge Connection
Permission: entire VPN Server Administrator
BridgeCreate
Virtual Hub Name to Create Bridge: DEFAULT
Bridge Destination Device Name: lan
# Get List of Local Bridge Connection
BridgeList
Number|Virtual Hub Name|Network Adapter or Tap Device Name|Status ------+----------------+----------------------------------+--------- 1 |DEFAULT |ens192 |Operating
Local Bridge Status
State:
Operating: functioning normally
Error: "device does not exist" error
Offline: does not exist or is offline
# Delete Local Bridge Connection
иҰҒжұӮ Permission: entire VPN Server Administrator
BridgeDelete
зӯ”е•ҸйЎҢ:
Virtual Hub Name to Delete Bridge: DEFAULT Bridge Device Name to Delete: ens192
# Using Tap Devices
The Linux version VPN Server / VPN Bridge allow the creation of a new tap device and bridging to that device.
* 當 Bridge иҰҒж”№ interface жҷӮ, йӮЈиҰҒеҲӘйҷӨеҺҹжң¬зҡ„ Bridge еҶҚе»әз«ӢйҒҺ
System Info
ServerInfoGet
Item |Value --------------------------------+-------------------------------------------- Product Name |SoftEther VPN Server (64 bit) Version |Version 4.20 Build 9608 (English) Build |Compiled 2016/04/17 21:59:35 by yagi at pc30 Host Name |softether.local Server Type |Standalone Server Type of Operating System |Linux Product Name of Operating System|Linux Operating System Vendor |Red Hat, Inc. Operating System Version |CentOS Linux release 7.0.1406 (Core) Type of OS Kernel |Linux Kernel Version of OS Kernel |Linux Kernel
ServerStatusGet
Item |Value ----------------------------------------------+------------------------- Server Type |Standalone Server Number of Active Sockets |46 Number of Virtual Hubs |1 Number of Sessions |0 Number of MAC Address Tables |37 Number of IP Address Tables |43 Number of Users |1 Number of Groups |0 Using Client Connection Licenses (This Server)|0 Using Bridge Connection Licenses (This Server)|0 Outgoing Unicast Packets |9,329 packets Outgoing Unicast Total Size |1,106,867 bytes Outgoing Broadcast Packets |4,982 packets Outgoing Broadcast Total Size |625,451 bytes Incoming Unicast Packets |614,891 packets Incoming Unicast Total Size |106,346,431 bytes Incoming Broadcast Packets |8,155 packets Incoming Broadcast Total Size |1,039,035 bytes Server Started at |2016-12-02 (Fri) 12:18:03 Current Time |2016-12-02 12:24:36.048 64 bit High-Precision Logical System Clock |392987
Caps - Get List of Server Functions/Capability
Item |Value ---------------------------------------------------------------+---------- Beta Version (Pre-release build) |No Works as VPN Bridge Software |No Cluster Controller Mode |No The Virtual Hub Types in a Cluster are Fixed |Yes Cluster Member Mode |No Running on VM (Virtual Machine) |Yes Either Free or Open-Source Version of SoftEther VPN |Yes Local Bridge is Supported |Yes Packet Capture Driver is Not Installed |No Standalone Mode |Yes Virtual Hub-Specific Source IP Address Limit Lists is Supported|Yes Conditioning by Group name is Supported in Access List |Yes Automatic Deletion of Log Files is Supported |Yes VPN Azure is Supported |Yes Cascade Connection is Supported |Yes Server Authentication for Cascade Connection is Supported |Yes Client Certificates for Cascade Connection is Supported |Yes Specifing MAC Address in Access Lists is Supported |Yes Checking TCP Connection State Filtering is Supported |Yes Operation as Part of a Cluster is Supported |Yes Integrated Administration for All Cluster Nodes is Supported |Yes Operating as a Cluster Controller |No Changing Virtual Hub Settings is Supported |Yes Changing Settings for Saving Log is Supported |Yes Remote Reading and Writing of Config File is Supported |Yes Virtual Hub-Specific Certificate Revocation Lists is Supported |Yes Dynamic DNS Client Function is Supported |Yes DDNS via Proxy Server is Supported |Yes Tagged VLAN Packet Transparency Support tool is Supported |No Delay, Jitter and Packet Loss is Supported in Access List |Yes Virtual Hub Enumeration Setting is Supported |Yes Virtual Hub Administration Options is Supported |Yes Virtual Hub Extended Option is Supported |Yes Intel CPU AES Acceleration (AES-NI) is Active |Yes IPsec / L2TP / EtherIP / L2TPv3 Server Functions are Supported |Yes IPv6 IP Access Control Lists is Supported |Yes IPv6 Access List is Supported |Yes The Virtual Layer 3 Switch is Supported |Yes Management of Licenses is Supported |No Limits for Multiple Login by Same User is Supported |Yes Message of Today function is Supported |Yes Getting Network Friendly Name is Supported |No OpenVPN Server Function is Supported |Yes Security Policy version 3 is Supported |Yes VoIP / QoS Functions is Supported |Yes External Authentication Server is Supported |Yes Retry Interval and Multi server is Supported in RADIUS Auth |Yes Downloading of Log Files is Supported |Yes HTTP URL Redirection in Access List is Supported |Yes Renaming of Cascade Connection is Supported |Yes SecureNAT is Supported |Yes VPN over ICMP and VPN over DNS is Supported |Yes MS-SSTP VPN Server Function is Supported |Yes Syslog Sending Functions is Supported |Yes UDP Acceleration Function is Supported |Yes VPN Gate Service Server Functions are Supported |No VPN Gate Service Server Functions (VPN Client integrated) |No Tagged VLAN ID is Supported in MAC Address Table |Yes Static Routing Table Pushing Function |Yes Static Routing Table Pushing Function (Configurable) |Yes Tun/Tap Device is Supported (only in Linux) |Yes SoftEther Lightweight Kernel-mode Ethernet Driver is Active |No Virtual NAT is Disabled (only DHCP Enabled) |No Accepting Connection from VPN Client / Bridge |Yes ...........................
ListenerList
multiple TCP/IP ports to be set on standby and VPN client computers can then establish a VPN connection
* Stopping or removing all of the available listener ports makes it impossible to connect to that VPN Server again
Port Number|Status -----------+--------- TCP 443 |Listening TCP 992 |Listening TCP 1194 |Listening TCP 5555 |Listening
# It does not display the TCP connections that have been established as VPN sessions.
ConnectionList
Connection Name|Connection Source|Connection Start |Type ---------------+-----------------+-------------------------+-------------- CID-3 |localhost: 41229 |2016-12-02 (Fri) 18:26:34|Management RPC CID-8 |localhost: 41655 |2016-12-05 (Mon) 16:21:25|Management RPC
# Get Information of TCP Connections Connecting to the VPN Server
ConnectionGet CID-8
Item |Value ------------------------+------------------------------------- Connection Name |CID-8 Connection Type |Management RPC Source Host Name |localhost Client Port Number (TCP)|41655 Connection Start |2016-12-05 (Mon) 16:21:25 Server Product Name |SoftEther VPN Server (64 bit) Sever Version |4.20 Server Build Number |9608 Client Product Name |SoftEther VPN Command-Line Admin Tool Client Version |4.20 Client Build |9608
# Disconnect TCP Connections Connecting to the VPN Server
ConnectionDisconnect CID-3
L2TP Setting
# Raw L2TP with No Encryption
only just a L2TP protocol without IPsec encryption.
To support such a strange device, you have to enable it.
# EtherIP / L2TPv3
EtherIP and L2TPv3 is for accepting VPN routers to build site-to-site VPNs.
# DHCP
So if no DHCP server, no login successes.
# L2TP Firewall
UDP 500 and 4500
firewall-cmd --add-port=500/udp --permanent
firewall-cmd --add-port=4500/udp --permanent
firewall-cmd --reload
жҲҗеҠҹ connection зҡ„ log
2016-12-02 10:33:58.730 L2TP PPP Session [192.168.88.132:1701]: An IP address is assigned. IP Address of Client: 192.168.88.220, Subnet Mask: 255.255.255.0, Default Gateway: 192.168.88.1, Domain Name: "", DNS Server 1: 192.168.88.1, DNS Server 2: 0.0.0.0, WINS Server 1: 0.0.0.0, WINS Server 2: 0.0.0.0, IP Address of DHCP Server: 192.168.88.1, Lease Lifetime: 86400 seconds
VPN Connection Checking (Session)
VPN Server/DEFAULT>SessionList
Item |Value ----------------+--------------------- # жӯӨ Section дҝӮе’ӘйғҪжңү Session Name |SID-LOCALBRIDGE-2 VLAN ID |- Location |Local Session User Name |Local Bridge Source Host Name|Ethernet Bridge TCP Connections |None Transfer Bytes |48,680,716,293 Transfer Packets|380,593,301 ----------------+--------------------- Session Name |SID-"Pre-Shared Key"-[L2TP]-8 VLAN ID |- Location |Local Session User Name |Login-Username Source Host Name|n.n.n.n TCP Connections |1 / 1 Transfer Bytes |36,072 Transfer Packets|270
VPN Server/DEFAULT>VPN Server/DEFAULT>SessionGet SID-"Pre-Shared Key"-[L2TP]-8
Item |Value ------------------------------------------+----------------------------------------------- Client IP Address |n.n.n.n ........ User Name (Database) |XXXXXXXX ........ Encryption |Enabled (Algorithm: IPsec - AES-CBC (256 bits)) ........ Connection Started at |2016-12-14 (Wed) 15:55:03 ........ Connection Name |CID-15
Final turning
Config File: vpn_server.config
To disable the Dynamic DNS Function
/etc/init.d/vpnserver stop # зӣҙжҺҘдҝ®ж”№ config file еҝ…й Ҳ stop service
Modify config
declare DDnsClient
{
bool Disabled true
byte Key ...
string LocalHostname softether
string ProxyHostName $
uint ProxyPort 0
uint ProxyType 0
string ProxyUsername $
}Checking
VPN Server>DynamicDnsGetStatus
# Disable жғ…жіҒ
DynamicDnsGetStatus command - Show the Current Status of Dynamic DNS Function Error occurred. (Error code: 33) Unsupported.
# Enable жғ…жіҒ
Item |Value ----------------------------------------+-------------------------------- Assigned Dynamic DNS Hostname (Full) |vpnNNNNNNNNN.softether.net Assigned Dynamic DNS Hostname (Hostname)|vpnNNNNNNNNN DNS Suffix |.softether.net Global IPv4 Address |n.n.n.n Global IPv6 Address |Connection to the server failed.
Disable ping a host
# UDP (1) / TCP (0)
Modify Config File
declare ServerConfiguration
{
bool UseKeepConnect true
string KeepConnectHost keepalive.softether.org
uint KeepConnectInterval 50
uint KeepConnectPort 80
uint KeepConnectProtocol 1
}Modify By CLI:
VPN Server> KeepGet
Item |Value --------------------------+----------------------- Host Name |keepalive.softether.org Port Number |80 Packet Send Interval (Sec)|50 Protocol |UDP/IP Current Status |Disable
VPN Server> KeepDisable
Nat Traversal
NAT Traversal is enabled by default.
A SoftEther VPN Server running on the computer behind NAT or firewall can accept VPN connections from the Internet,
without any special configurations on firewalls or NATs.
declare ServerConfiguration
{
bool DisableNatTraversal true
}
NAT Traversal
The built-in NAT Traversal Function opens a "Punched Hole" on the NAT or firewall.
When the VPN Client or VPN Bridge attempts to connect to your VPN Server behind the NAT,
the connection packets will be lead through the hole.
The hole is created by the SoftEther VPN Server automatically, so you need nothing special on the NAT.
Virtual Layer 3 Switches
# Get List of Virtual Layer 3 Switches
RouterList
Check VPN Support
OVPN
VPN Server>OpenVpnGet
Item |Value ----------------------------+----- OpenVPN Clone Server Enabled|No UDP Port List |1194
IPsec
VPN Server>IPsecGet
Item |Value ---------------------------------------------------+-------- L2TP over IPsec Server Function Enabled |Yes Raw L2TP Server Function Enabled |No EtherIP / L2TPv3 over IPsec Server Function Enabled|No IPsec Pre-Shared Key String |???????? Name of Default Virtual Hub |DEFAULT
Sstp
VPN Server>SstpGet
Item |Value -----------------------------+----- SSTP VPN Clone Server Enabled|No
Vpn Over Icmp/Dns
VPN Server>VpnOverIcmpDnsGet
Item |Value ----------------------------+----- VPN over ICMP Server Enabled|No VPN over DNS Server Enabled |No The command completed successfully.
Azure
VPN Server>VpnAzureGetStatus
Item |Value -----------------------------+----- VPN Azure Function is Enabled|No
VPN Over DNS / ICMP
Payload:
DNS # 53/UDP
Ping # ICMP
Enable VPN over X
GUI:
"Encryption and Network" -> "VPN over ICMP / DNS Settings"
Config File:
declare ServerConfiguration
{
bool EnableVpnOverDns true
bool EnableVpnOverIcmp false
...
}Client side disable VPN over X functions
appending "/tcp" suffix after the destination hostname.
Remark
It might causes memory-overflow or something problems on the "buggy routers" on the network.
Some routers might reboot because of these problems.
Speed test
Speed test з”ұ vpncmd иІ иІ¬
Tools Mode
# speed еҠҹиғҪжҳҜеңЁ tools mode зҡ„
/opt/vpnserver/vpncmd /TOOLS
TrafficServer
TrafficServer [port]
Default: 9821
i.e.
/opt/vpnserver/vpncmd /TOOLS /CMD TrafficServer
The Network Traffic Speed Test Tool in Server Mode started. Press the Enter key to stop the server program.
FW Port
firewall-cmd --add-port=9821/tcp --permanent
Or
firewall-cmd --add-rich-rule='rule family="ipv4" source address="192.168.88.0/24" port protocol="tcp" port="9821" accept' --permanent
TrafficClient
Unit: bitps
TrafficClient [host:port] [/NUMTCP:numtcp] [/TYPE:download|upload|full] [/SPAN:span]
/NUMTCP
Specify the number of TCP connections to be concurrently established between the client and
the server for data transfer. If omitted, 32 will be used.
/TYPE
"download", "upload" or "full"(Default)
By specifying "download" the data will be transmitted from the server side to the client side.
/SPAN
Specify, using seconds, the time span to conduct data transfer for the measurement of throughput. Default: "15"
Multiple physical tcp connection aggregation
* иҰҒ Direct TCP/IP Connection жүҚжңғжңү multiple physical tcp connection aggregation
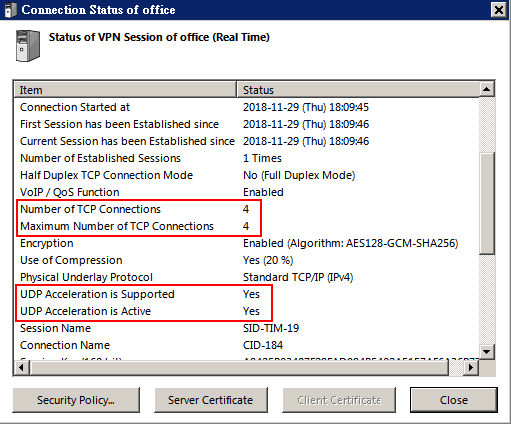
Parallel Transmission Mechanism of Multiple Tunnels
When this function is enabled, the logical VPN Session will consist of several TCP (HTTPS) connections.
All packets will be added to one of the appropriate TCP connections with calculations of optimizing modules.
If some packet losses have been detected on a TCP connection of the logical VPN Session,
then the new packet will use another health VPN connection.
UDP Acceleration Function
If a VPN consists of two sites detects that UDP channel can be established, UDP will be automatically used.
Direct UDP channel
If direct UDP channel can be established, direct UDP packets will be used.
UDP Hole Punching
if there is something obstacles such as firewalls or NATs, the "UDP Hole Punching" technology will be used, instead.
The "UDP Hole Punching" uses the cloud servers which SoftEther Corporation operates on Internet.
Disable UDP Acceleration
UDP Acceleration can be disabled anytime by setting up so on the VPN-client side.
Port
A pair of SoftEther VPN Client and SoftEther VPN Server will try to make a fast UDP-based VPN link between them,
even if both or any parties are behind the NAT or firewall.
In order to make a fast UDP-based VPN link, SoftEther VPN exploits the UDP Hole Punching (NAT-Traversal) technique.
Source Code
// Range of port numbers #define UDP_SERVER_PORT_LOWER 40000 // Minimum port #define UDP_SERVER_PORT_HIGHER 44999 // Maximum port
firewalld
firewall-cmd --add-port=40000-44999/udp --permanent
firewall-cmd --add-port=40000-44999/udp
User/Group Security Policies
The Virtual Hub interprets the header information of all virtual Ethernet frames flowing over it internally to a high layer
(automatic recognition of ARP / IP / TCP / UDP / ICMP / DHCP etc) and
determines whether their communication content conforms to a security policy based on the results of that interpretation.
Default
[Allow access] is enabled
permission to make VPN connection to VPN Server
[Maximum Number of TCP connections] is 32
maximum number of physical TCP connections consists in a physical VPN session
[Time-out Period] is 20 seconds
period to wait before disconnecting a session when communication trouble occurs between the VPN Client / VPN Server
Useful Policy
Filter All Non-IP Packets
Any tagged-VLAN packets via the Virtual Hub will be regarded as non-IP packets.
Filter All IPv6 Packets
Disallow DHCP Server Operation
not be allowed to become a DHCP server
Enforce DHCP Allocated IP Addresses (IPv4)
only be able to use IPv4 addresses allocated by a DHCP server on the virtual network side.
йҳІдәәеҒҮеҶ’
Deny MAC Addresses Duplication
Deny IP Address Duplication (IPv4)
a risk of security because incorrect user can have an IP address
and also can send an IP address imposing the correct one.
This security policy can do it, not only for IP addresses, but also MAC addresses.
Privacy Filter Mode
A user which is set by this policy cannot communicate any other user who is set by this policy too.
This policy is convenient the situation that the administrator allows users to access to only the central servers,
but disallow to users to communicate each other, for security reason.
Deny Changing Password
Deny Non-ARP / Non-DHCP /Non-ICMPv6 broadcast
Deny Operation as TCP/IP server policy
session is unable to respond to a SYN packet in TCP from a separate session.
# cascade connection
Deny Bridge Operation policy # cannot connect to the virtual hub as a [Router/ Bridge Mode] session.
Deny Routing Operation policy
Privacy Filter Mode policy # Filters all direct intersession communication in sessions
Access list / IP access control list
the "access list" controls IP packets flowing in a Virtual Hub using their IP addresses, protocol port numbers and so on,
the "IP access control list" is used to refine the physical IP addresses of connection sources which can make a VPN connection to the Virtual Hub.
No Enumerate To Anonymous Users
Entering the host name and port number of the destination VPN Server in the Windows version SoftEther VPN Client Manager or
VPN Server Manager automatically acquires a list of the Virtual Hubs registered on that VPN Server and displays them in a drop-down list box.
This is known as "Virtual Hub anonymous enumeration"
SecureNAT
Alternative to Promiscuous Mode
VMs prohibit the "Promiscuous Mode" (MAC Address Spoofing) on the network adapters by default.
* All traffic that passes through SecureNAT is accurately logged in the security log file
NAT Mode Spec
- User-mode NAT
- Kernel-mode NAT
- Virtual NAT Function: Maximum 4096 Dynamic Mapping
- Virtual DHCP Function
The SecureNAT еңЁ user mode жҸҗдҫӣ NAT еҸҠ DHCP server functions
Unlike the local bridge function, all settings of the SecureNAT function can be set by the Virtual Hub Administrators.
Enabling the SecureNAT function creates a virtual VPN session called a SecureNAT session within the Virtual Hub and
creates a virtual network interface (VNI) as if there were a single network adapter within that VPN session.
This is called a virtual host network interface.
A virtual host network interface is layer 2 direct connected to the Virtual Hub.
SecureNAT Speed: 100mb~200mb
NAT
Default Setting
Virtual NAT and Virtual DHCP Server > SecureNAT Configuration
- TCP Session Timeout: 1800s
- UDP Session Timeout: 60s
Virtual DHCP Server еҠҹиғҪ
* Allocating IP Addresses only without Allocating Default Gateway & DNS Server Addresses
* The LAN connected to the computer actually running the Virtual Hub is not affected
(This does not apply in the case of local bridging)
* ж”ҜжҸҙ push route еҲ° client (RFC 3442 - Classless Static Route Option for DHCP)
(SoftEther & OVPN Client Support, L2TP/SSTP иҰҒзңӢ OS)
# Format: IP/Subnet/Gateway 192.168.123.0/255.255.255.0/192.168.30.1
Notes
Client connected to SoftEther can't ping server itself (Server: linux)
* Limitations within the Linux or UNIX operating system
(restriction lies with OS's internal kernel codes)
Please use localbridge to TAP device ("double-bridge" setup)
Tap device is created by the softether vpn server automatically when you add it, with name as "tap_" as the prefix in ifconfig.
Bridge it to your original LAN adapter using a linux bridge. Do not add tap1 with your own linux command.
Performance Setting
Virtual Hub Extended Options
GUI: Virtual Hub Name -> Properties -> Edit Virtual Hub Extended Options List
ManageOnlyPrivateIP
The IPv4 address table of the Virtual Hub will contain only private IPv4 addresses.
FilterIPv6
The Virtual Hub discards all IPv6 packets.
Filter All Non-IP Packet
All non-IP packets in sessions defined this policy will be filtered.
"Non-IP packet" mean a packet which is not IPv4, ARP nor IPv6.
Any tagged-VLAN packets via the Virtual Hub will be regarded as non-IP packets.
Troubleshoot
[1] softether high cpu usage
Do you use LocalBridge and SecureNAT? If so, packet is loop.
Changing the local bridge settings, in creating a tap device instead of a bridge device.
[2] Duplicate Packets on Softether Server
Destination host and SecureNAT virtual host send ping reply when SecureNAT operating mode is raw IP mode.
SecureNAT is automatically answering ping requests on its own regardless of OS configuration.
(version 4.29 build 9680)
# еңЁ Server(s.s.s.s) дёҠиЎҢ
tcpdump -n -v -i ens192 icmp dst c.c.c.c
# жңү 3 зө„еӣһжҮү # 第 1 10:54:58.744751 IP (tos 0x0, ttl 64, id 24573, offset 0, flags [none], proto ICMP (1), length 84) s.s.s.s > c.c.c.c: ICMP echo reply, id 45, seq 1, length 64 10:54:58.745281 IP (tos 0x0, ttl 128, id 4439, offset 0, flags [none], proto ICMP (1), length 84) s.s.s.s > c.c.c.c: ICMP echo reply, id 45, seq 1, length 64 # 第 2 10:54:59.742756 IP (tos 0x0, ttl 64, id 24968, offset 0, flags [none], proto ICMP (1), length 84) s.s.s.s > c.c.c.c: ICMP echo reply, id 45, seq 2, length 64 10:54:59.743149 IP (tos 0x0, ttl 128, id 4440, offset 0, flags [none], proto ICMP (1), length 84) s.s.s.s > c.c.c.c: ICMP echo reply, id 45, seq 2, length 64 # 第 3 10:55:00.742808 IP (tos 0x0, ttl 64, id 25312, offset 0, flags [none], proto ICMP (1), length 84) s.s.s.s > c.c.c.c: ICMP echo reply, id 45, seq 3, length 64 10:55:00.743384 IP (tos 0x0, ttl 128, id 4441, offset 0, flags [none], proto ICMP (1), length 84) s.s.s.s > c.c.c.c: ICMP echo reply, id 45, seq 3, length 64
# еңЁ Client(c.c.c.c) дёҠиЎҢ
ping -c 3 s.s.s.s
64 bytes from s.s.s.s (s.s.s.s): icmp_seq=1 ttl=54 time=6.74 ms 64 bytes from s.s.s.s (s.s.s.s): icmp_seq=1 ttl=118 time=7.03 ms (DUP!) 64 bytes from s.s.s.s (s.s.s.s): icmp_seq=2 ttl=54 time=6.99 ms 64 bytes from s.s.s.s (s.s.s.s): icmp_seq=2 ttl=118 time=6.99 ms (DUP!) 64 bytes from s.s.s.s (s.s.s.s): icmp_seq=3 ttl=54 time=7.01 ms
[Fix]
[1]
bool DisableIpRawModeSecureNAT true
[2]
iptables -A OUTPUT -p icmp -m ttl --ttl-gt 100 -j DROP
OR
firewall-cmd --permanent --direct --add-rule ipv4 filter OUTPUT_direct 1 -o ens192 -p icmp -m ttl --ttl-gt 100 -j DROP
AccessList
# Get Access List Rule List
Item |Value ---------+------------------------------------------------ ID |1 Action |Pass Status |Enable Priority |1001 Unique ID|2742539467 Contents |(ipv4) DstIPv4=192.168.10.222/32, SrcUser=shawnn Memo |access_file_server ---------+------------------------------------------------ ID |2 Action |Discard Status |Enable Priority |1002 Unique ID|3895156983 Contents |(ipv4) DstIPv4=192.168.10.0/24, SrcUser=shawnn Memo |deny_access_other_server_in_office_lan
* Allow VPN Client дёҠз¶ІдёҚз”ЁеҠ Gateway IP & VPN Server IP
Diagram
|=====SecureNAT======| [Client](192.168.30.X)---[Office LAN](192.168.10.X)---[Internet]
GW: 192.168.30.1 / 192.168.10.1
Traffic ACL on the Virtual Hub
GUI: Manage Virtual Hub -> Manage Access Lists
* This kind of rule does not restrict connections to the virtual hub.
* The default rule permits access
If you want to restrict connections to the virtual hub from a particular subnet,
then you need to set a rule at:
Manage Virtual Hub -> Virtual Hub Properties -> IP Address Control List
OpenVPN
L3-mode => "VPN Client" session
The IP, GW, DNS address will be assigned on the virtual network adapter of OpenVPN automatically
L2-mode => "VPN Bridge" session
No IP-specific treatment will be done.
All Ethernet packets (MAC frames) will exchanged transparently between two or more sites.
Troubleshoot
еңЁ Server дёҠиҰӢеҲ° Client дёҖйҖЈе°ұж–·з·ҡ:
2020-08-19 13:44:26.422 On the TCP Listener (Port 5555), a Client (IP address C.C.C.C, Host name "C-C-C-C.static.pccw-hkt.com", Port number 25182) has connected. 2020-08-19 13:44:26.422 For the client (IP address: C.C.C.C, host name: "14-0-165-030.static.pccw-hkt.com", port number: 25182), connection "CID-73" has been created. 2020-08-19 13:44:27.438 OpenVPN Module: The OpenVPN Server Module is starting. 2020-08-19 13:44:27.438 OpenVPN Session 1 (C.C.C.C:25182 -> 192.168.1.201:5555): A new session is created. Protocol: TCP 2020-08-19 13:44:27.438 OpenVPN Session 1 (C.C.C.C:25182 -> 192.168.1.201:5555) Channel 0: A new channel is created. 2020-08-19 13:44:27.589 OpenVPN Module: The OpenVPN Server Module is stopped. 2020-08-19 13:44:27.589 Connection "CID-73" has been terminated. 2020-08-19 13:44:27.589 The connection with the client (IP address C.C.C.C, Port number 25182) has been disconnected.
еҺҹеӣ
Server CA / Cert йҒҺдәҶжңҹ !!
Route traffic to another side
SSL VPN еүҚ
з¶Іи·Ҝзӣ®зҡ„ең° з¶Іи·ҜйҒ®зҪ© й–ҳйҒ“ д»Ӣйқў иЁҲйҮҸ
0.0.0.0 0.0.0.0 192.168.123.1 192.168.123.31 261SSL VPN еҫҢ
# R.R.R.R дҝӮ remote зҡ„ WAN IP
з¶Іи·Ҝзӣ®зҡ„ең° з¶Іи·ҜйҒ®зҪ© й–ҳйҒ“ д»Ӣйқў иЁҲйҮҸ
0.0.0.0 0.0.0.0 192.168.88.1 192.168.88.74 2
R.R.R.R 255.255.255.255 192.168.123.1 192.168.123.31 261дёҚ Route Traffic еҲ°еҸҰдёҖйӮҠ
[ж–№жі• 0]
when using the virtual DHCP you are able to clear the Gateway field thus not giving the client a default gateway and
this results in not giving the client a default route.
[ж–№жі• 1]
No Adjustments of Routing Table # е”” work =.=?
[ж–№жі• 2]
You can just increase metric on vpn client adapter gateway (in Windows).
VPN client adapter -> properties -> tcp/ip -> advanced -> interface metric: 9999
route print
Active Routes:
Network Destination Netmask Gateway Interface Metric
0.0.0.0 0.0.0.0 192.168.130.254 192.168.130.30 10000 # 當иЁӯе®ҡжҲҗ 9999 жҷӮе®ғжңғи®Ҡ 10000
0.0.0.0 0.0.0.0 192.168.88.1 192.168.88.177 291
...[ж–№жі• 3]
remove the route manually
Reset Administrator Password
1 shutdown the vpnserver manually
2. edit the server configuration
3. delete the admin hash
declare ServerConfiguration
{
...
byte HashedPassword ******* (hashed password data)3. Next time you start and try to login without password
Embedded web server and JSON-RPC server
JSON-RPC API
API Suite allows:
creating users, adding Virtual Hubs, disconnecting a specified VPN sessions
https://<vpn_server_hostname>:<port>/api/
Embedded web server
https://<server IP address>/admin/
Disable
/etc/init.d/vpnserver stop
vim vpn_server.config
"bool DisableJsonRpcWebApi" from "false" to "true"
/etc/init.d/vpnserver start
Reset Statistics
Delete that user and then create it back
дҝ®ж”№ vpn_server.config, жё…дәҶи—ҚиүІйғЁд»Ҫ
declare UserList
{
declare YOUR-USERNAME
{
declare Traffic
{
...
declare RecvTraffic
{
...
}
declare SendTraffic
{
...
}
{
}
}
Access Server after VPN
Lan(123.0/24) - (123.251)Server(30.251) - VPN(192.168.30.1/24)1. е»әз«Ӣж–° NIC (tap_vpn) дёҰ set жҲҗ vpn subnet ip (30.251)
/sbin/ifconfig tap_vpn 192.168.30.251 netmask 255.255.255.0 &> /dev/null
2. push route to client
# Checking on client
route print | findstr 123.0
# 30.11 дҝӮ client йҖЈдёҠ VPN еҫҢзҚІеҫ—зҡ„ IP
192.168.123.0 255.255.255.0 192.168.30.251 192.168.30.11 2ping 192.168.123.251
Upgrade
Steps:
- cd /opt
- ./vpnserver/vpnserver stop
- mv vpnserver vpnserver.bak
- tar -zxf softether-vpnserver-v4.42-9798-rtm-2023.06.30-linux-x64-64bit.tar.gz
- cp -a vpnserver.bak/adminip.txt vpnserver/
- cp -a vpnserver.bak/vpn_server.config vpnserver/
- cp -a vpnserver.bak/lang.config vpnserver/
- cd vpnserver
- make
- ./vpnserver start
Changelog
SoftEther VPN 4.34 Build 9745 RTM
* еҠ е…ҘдәҶ Embedded web server еҸҠ JSON-RPC server
Doc
![йҰ–й Ғ Logo ¶гБВ Keith і]ӯp !!](/themes/mytheme/logo.png)