жңҖеҫҢжӣҙж–°: 2019-10-04
д»Ӣзҙ№
зӣ®йҢ„
- SSH VPN CMD
- Create Tunnel (tunX) by CMD
- иЁӯе®ҡ tunX IP
- NAT
- Route
SSH VPN CMD
-w local_tun[:remote_tun]
Requests tunnel device forwarding with the specified tun devices
between the client (local_tun) and the server (remote_tun).
The devices may be specified by
- numerical ID
- keyword“any”, which uses the next available tunnel device
- remote_tun is not specified, it defaults to “any”
i.e.
- -w any
- -w 0
- -w 0:0
ssh_config
If the Tunnel directive is unset, it is set to the default tunnel mode, which is "point-to-point"
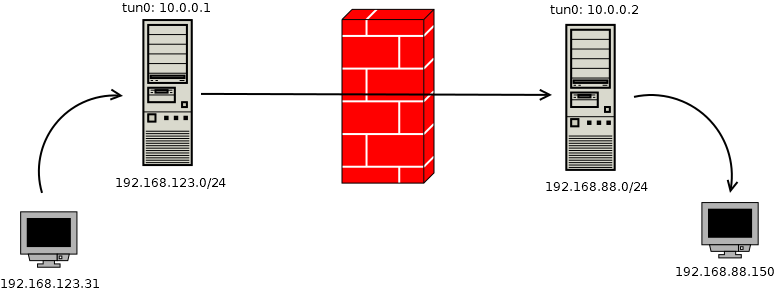
Create Tunnel (tunX)
# -f Requests ssh to go to background just before command execution.
ssh -f -w 0:0 root@sshtunnel true
* иҰҒжңү root ж¬ҠйҷҗеҸҠServer Side жңү 'PermitTunnel point-to-point' иЁӯе®ҡ, еҗҰеүҮжңғжңү Error
channel 0: open failed: administratively prohibited: open failed
# Checking
ip addr show tun0
11: tun0: <POINTOPOINT,MULTICAST,NOARP> mtu 1500 qdisc noop state DOWN qlen 500
link/[65534]
иЁӯе®ҡ tunX IP
# On Client Side (з”Ё iproute2 дҫӢеӯҗ)
[1]
ip link set dev tun0 up
[2]
ip addr add 10.1.1.1 peer 10.1.1.2 dev tun0
[3]
ip route add 192.168.88.0/24 via 10.1.1.2
# Checking
ip addr show tun0; ip route list 192.168.88.0/24
# On Server Side (ifconfig еҸҠ route)
[1]
ifconfig tun0 up
[2]
ifconfig tun0 10.1.1.2 pointopoint 10.1.1.1
[3]
route add -net 192.168.123.0/24 gw 10.1.1.2 dev tun0
# Checking
ifconfig tun0; route | grep 192.168.123.0
# Cleanup
ip addr flush tun0
NAT
# иЁӯе®ҡ
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables -I FORWARD -i tun0 -j ACCEPT
iptables -t nat -I POSTROUTING -s 10.1.1.1 -o ens4 -j MASQUERADE
# Checking
iptables -nvL FORWARD | grep tun0
# Cleanup
iptables -D FORWARD -i tun0 -j ACCEPT
iptables -t nat -D POSTROUTING -s 10.1.1.1 -o ens4 -j MASQUERADE
echo 0 > /proc/sys/net/ipv4/ip_forward
Route
Server
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables -I FORWARD -i tun0 -j ACCEPT # Client to Any
iptables -I FORWARD -s 192.168.88.150 -j ACCEPT # Tester to Client
# Check
iptables -vnL FORWARD
Tester (Server Side 's PC)
ip route add 192.168.123.0/24 via 192.168.88.184
![йҰ–й Ғ Logo ¶гБВ Keith і]ӯp !!](/themes/mytheme/logo.png)