жңҖеҫҢжӣҙж–°: 2019-10-02
зӣ®йҢ„
- Local Port Forward (-L)
- Reverse ssh tunnel (-R)
- Remote forward(-R) with 0.0.0.0
- Local forward(-L) with 0.0.0.0
- Dynamic Proxy
- ssh жҷӮиҮӘеӢ•е»әз«Ӣ tunnel
-
putty ssh tunnel
Socks5 Proxy - putty SOCKS v5
- autossh
- sidedoor
- ~/.ssh/config
- sshd йҷҗеҲ¶еҸӘеҸҜд»Ҙ tunnel еҺ»жҹҗ IP:Port
Local Port Forward (-L)
Diagram
# зӣёз•¶ж–ј Local зҡ„ 8888 map жҲҗ WWW зҡ„ 80
Client ------------------> Host -------------------> WWW-Server
tunnel unencrypted
port 8888 22 80
ssh_clinet ssh_server www
Usage
ssh -N -f [username@my_ssh_server] -L [lport]:[remote_host]:[rport]
Example
ssh -NT -f user@host -L 8888:WWW-Server:80
-
-N Do not execute a remote command.
е®ғжұәе®ҡеңЁ server дёҠз”Ё "none" йҖҷеҖӢ subsystem
"default" дҝӮ shell дҫҶ - -T Disable pseudo-tty allocation
- -f "йҖЈз·ҡеҫҢж–јиғҢжҷҜеҹ·иЎҢ"
Reverse ssh tunnel (-R)
дёҖиҲ¬дҫҶиӘӘ, йҖҷеҠҹиғҪжҳҜз”ЁеңЁ "жңүеҮәз„Ўе…Ҙ" зҡ„ең°ж–№, жҜ”еҰӮ Source жҳҜеңЁ Firewall еҫҢ, иҖҢдҪ еҸҲжғіеҫһеӨ–йқўйҖЈе…ҘеҺ»
Diagram
[SSH_Client] --ssh--[firewall]--ssh--> [SSH_Server(Port:22)]
[SSH_Client] -------[firewall]-------- SSH_Server
|
|
127.0.0.1:22 <---by_pass_fw--- 127.0.0.1:2222
Usage
# remote_port:localhost:local_port
ssh -R 2222:localhost:22 user@source
Example:
Step_1: еңЁ firewall еҫҢзҡ„ client ssh еҮәеҺ»
Step_2: жҲҗеҠҹеҫҢ, Firewall еӨ–зҡ„ Server зҡ„ Port 2222 зӣёз•¶еҚЎ Firewall еҫҢ Server зҡ„ Port 22
* port жңҖеҘҪз”Ё > 1024, еӣ зӮәдҪҺ port еҸӘжңү root жүҚз”ЁеҲ°
Remote forward(-R) with 0.0.0.0
GatewayPorts
Enabling it will instruct sshd to allow remote port forwardings to bind to a non-loopback address.
(by default it is disabled)
/etc/ssh/sshd_config
Match User root GatewayPorts yes
client cmd
-R 8080:127.0.0.1:8080 # е®ғжҳҜжҢҮ 127.0.0.1:8080
-R :8080:127.0.0.1:8080 # е®ғжҳҜжҢҮ 0.0.0.0:8080 !!
openwrt зҡ„ sshd (dropbear)
/etc/config/dropbear
config dropbear
option PasswordAuth 'on'
option RootPasswordAuth 'on'
option GatewayPorts 'on'
option Port '22'
Local forward(-L) with 0.0.0.0
# -g Allows remote hosts to connect to local forwarded ports.
ssh -g -L 8001:localhost:8000 root@remote-machine
жІ’жңүеҠ "-g" жҷӮ
netstat -nlt | grep 8080
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN
еҠ дәҶ "-g"
netstat -nlt | grep 8080
tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN
Dynamic Proxy
-D [bind_address:]port
ssh -D 10080 -fN user@jumphost
# wget, curl, yum йғҪжңғз”ЁжӯӨ Environment Variable
export http_proxy=http://SERVER:PORT/
e.g.
# еҲ©з”Ё ssh tunnel еҒҡ proxy
export http_proxy=http://localhost:10080/
yum settings
/etc/yum.conf
proxy=socks5://localhost:10080
ssh жҷӮиҮӘеӢ•е»әз«Ӣ tunnel
дҝ®ж”№ ~/.ssh/config
еҠ дёӢ
# дёҖиЎҢдёҖеҖӢ forward LocalForward [bind_address:]Lport Rhost:Rport
ж•Ҳжһңзӣёз•¶ж–ј
ssh -f -N Lport:Rhost:Rport
putty ssh tunnel
ssh дәҰеҸҜд»ҘдҪң vpn д№Ӣз”Ё, зңҹжҳҜдёҚи¬ӣдёҚзҹҘ !!!
е·Ҙе…· pietty:
еңЁ Source port еЎ« 8080
Destination еЎ« 192.168.1.1:80
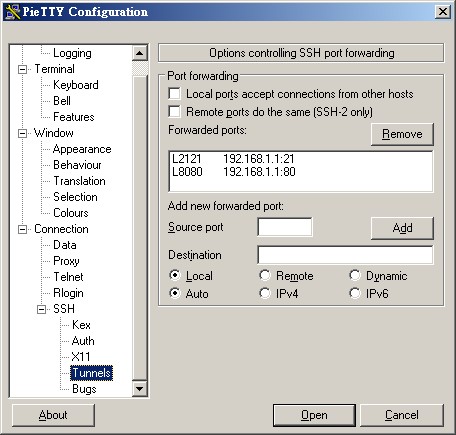
з¶Ій Ғ:
йӮЈеңЁ IE з¶ІеқҖеЎ« http://127.0.0.1:8080 ,
е°ұеҸҜйҖЈдёҠз¶ҒеңЁ loopback interface зҡ„ Web Server
ftp:
еҰӮжһңдҝӮдҪң ftp зҡ„ 21 еҠ иңңзҡ„и©ұ, иЁҳеҫ—иҰҒд»Ҙ passive mode зҷ»е…Ҙ,
иҖҢ server йӮЈиЈЎиҰҒжңү "pasv_promiscuous=YES" зҡ„иЁӯе®ҡ (д»ҘдёҠжҳҜ ftp зҡ„иЁӯе®ҡ)
е°ҚжҜ” Linux дёҠзҡ„жҮүз”Ё
ssh -f -N -L 2121:192.168.1.1:21 [email protected]
-N дёҚе»әз«Ӣshell
-f йҖЈз·ҡеҫҢеҹ·иЎҢж–јиғҢжҷҜ
д»ҘдёҠе…©еҸғж•ёзјәдёҖдёҚеҸҜ !!
Putty Setting:
Path: Settings -> Connection -> SSH _Tunnels
Source Port: 1080 Destination: BLANK Type: Dynamic
Checking:
netstat -an | find "10080"
TCP 127.0.0.1:1080 0.0.0.0:0 LISTENING
Firefox Setting:
https://datahunter.org/firefox#proxy_setting
Reverse Tunnel Setting
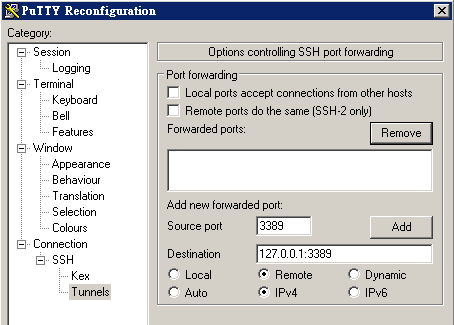
Disable interactive shell access while tunneling
[ж–№жі•1]
For any tunnelling-only user, change their login shell to /sbin/nologin
[ж–№жі•2]
authorized_keys
command="/sbin/nologin",no-pty ssh-rsa ...[ж–№жі•3]
Match group proxy-only
ForceCommand /sbin/nologin
PermitTTY no
...Checking
# Test by ssh
ssh sshtunnel
--
PermitTTY no
PTY allocation request failed on channel 0
--
ForceCommand /sbin/nologin
This account is currently not available. Connection to SERVER closed.
--
ChrootDirectory %h
Write failed: Broken pipe
Chroot Tunnel Environment
Proxy Only
AllowTcpForwarding
Specifies whether TCP forwarding is permitted.
- 'yes' (the default) or 'all' to allow TCP forwarding,
- 'no' to prevent all TCP forwarding,
- 'local' to allow local forwarding only or
- 'remote' to allow remote forwarding only.
PermitTunnel
Specifies whether tun(4) device forwarding is allowed
- yes(permits both point-to-point and ethernet)
- point-to-point (layer 3)
- ethernet (layer 2)
- no (default)
AllowStreamLocalForwarding
Specifies whether StreamLocal (Unix-domain socket) forwarding is permitted.
- yes (the default) or all to allow StreamLocal forwarding,
- no to prevent all StreamLocal forwarding,
- local to allow local (from the perspective of ssh(1)) forwarding only or
- remote to allow remote forwarding only.
AllowTcpForwarding remote
AllowStreamLocalForwarding no
GatewayPorts yes
Example: proxy-only
"proxy-only" Group
Match group proxy-only
X11Forwarding no
PermitTunnel no
GatewayPorts yes
AllowTcpForwarding remote
ForceCommand /sbin/nologin
PermitTTY no
PermitRootLogin no
KbdInteractiveAuthentication no
PasswordAuthentication no
PubkeyAuthentication yes
autossh
еҠҹиғҪ:
monitor and restart ssh sessions
The original idea and the mechanism were from rstunnel (Reliable SSH Tunnel).
е®үиЈқ:
# Centos 7
yum install autossh
# Check Version
autossh -V
autossh 1.4e
еҺҹзҗҶ:
autossh -M 0 -L 5000:localhost:3306 [email protected]
зӣёз•¶ж–ј
ssh -L 5000:localhost:3306 [email protected]
Usage
autossh [-V] [-M monitor_port[:echo_port]] [-f] [SSH_OPTIONS]
-f # causes autossh to drop to the background before running ssh.
# The -f flag is stripped from arguments passed to ssh.
# When -f is used, the "starting gate" time is set to 0.
# з”Ё -f еҝ…й Ҳ public/private key authentification
AUTOSSH_GATETIME
Specifies how long ssh must be up before we consider it a successful connection. Default: 30 sec
-M port[:echo_port]
-M N
Specifies the base monitoring port to use.
Without the echo port, this port and the port immediately above it ( port + 1) should be something nothing else is using.
autossh will send test data on the base monitoring port, and receive it back on the port above. For example,
if you specify "-M 20000", autossh will set up forwards so that it can send data on port 20000 and receive it back on 20001.
-M 0
Setting the monitor port to 0 turns the monitoring function off, and autossh will only restart ssh upon ssh's exit.
For example, if you are using a recent version of OpenSSH,
you may wish to explore using the ServerAliveInterval and ServerAliveCountMax options
to have the SSH client exit if it finds itself no longer connected to the server.
In many ways this may be a better solution than the monitoring port.
ServerAliveInterval (Default: 0)
Sets a timeout interval in seconds after which if no data has been received from the server,
ssh will send a message through the encrypted channel to request a response from the server.
ServerAliveCountMax (Default: 3)
If this threshold is reached while server alive messages are being sent,
ssh will disconnect from the server, terminating the session.
# Default Values:
autossh -o "ServerAliveInterval 30" -o "ServerAliveCountMax 3"
Server Side:
е»әз«Ӣ user
useradd -m -s /bin/false autossh
е»әз«Ӣ key
su -s /bin/bash autossh
ssh-keygen
mv ~/.ssh/id_rsa.pub ~/.ssh/authorized_keys
cat ~/.ssh/id_rsa
Client Side:
# Basic
autossh -M 0 -R 2222:localhost:22 autossh@remotemachine
* жңҖе°ҸеҲҮйңҖиҰҒеҠ "-M 0"
# жё¬и©Ұ
mkdir ~/ssh-key
chmod 700 ~/ssh-key
# дҝқеӯҳдёҠеҖӢ step cat еҮәдҫҶзҡ„ key
vim ~/ssh-key/sshgw.key
chmod 400 /root/ssh-key/sshgw.key
autossh -N -M 0-R 2222:localhost:22 autossh@remotemachine -i /root/ssh-key/sshgw.key
-N Do not execute a remote command. жІ’жңү -N жҷӮ, йӮЈжңғзҚІеҫ—дёҖеҖӢ shell
# жҲҗеҠҹеҫ—еңЁ server side жңғиҰӢеҲ°
netstat -ntlp | grep ssh
tcp 0 0 127.0.0.1:2222 0.0.0.0:* LISTEN 3092/sshd
# ж–·з·ҡжё¬и©Ұ
killall -u autossh
log (/var/log/messages)
Jul 21 16:30:24 centos7 autossh[13647]: ssh exited with error status 255; restarting ssh Jul 21 16:30:24 centos7 autossh[13647]: starting ssh (count 3) Jul 21 16:30:24 centos7 autossh[13647]: ssh child pid is 13657
systemd:
/etc/systemd/system/autossh-mysql-tunnel.service
[Unit] Description=AutoSSH tunnel service everythingcli MySQL on local port 5000 After=network.target [Service] Environment="AUTOSSH_GATETIME=0" ExecStart=/usr/bin/autossh -M 0 -NL 5000:localhost:3306 autossh@myserver -p 1022 [Install] WantedBy=multi-user.target
systemctl daemon-reload
systemctl start autossh-mysql-tunnel.service
systemctl enable autossh-mysql-tunnel.service
sidedoor
SSH connection daemon
https://github.com/daradib/sidedoor
sidedoor maintains an SSH connection or tunnel with a shell script daemon.
- /bin/sh
- while true; do
иҲҮ autossh жҜ”ијғ
sidedoor is a minimalistic shell script daemon.
autossh is a more extensive and configurable C program.
~/.ssh/config
~/.ssh/config
Host remotemachine HostName 192.168.88.116 User autossh Port 22 IdentityFile ~/ssh-key/sshgw.key ServerAliveInterval 10 ServerAliveCountMax 3 # local зҡ„ 13306 зӣёз•¶ж–ј remote зҡ„ 3306 #LocalForward 13306 localhost:3306 # remote зҡ„ 2222 зӣёз•¶ж–ј local зҡ„ 22 RemoteForward 2222 localhost:22
sshd йҷҗеҲ¶еҸӘеҸҜд»Ҙ tunnel еҺ»жҹҗ IP:Port
/etc/ssh/sshd_config
Match User some-user #AllowTcpForwarding yes #PermitTunnel no #GatewayPorts no X11Forwarding no AllowAgentForwarding no PermitOpen localhost:3306 ForceCommand echo 'This account can only be used for mysql tunnel'
PermitOpen
Limit local 'ssh -L' port forwarding (limit connect to the specified host and port)
Multiple forwards may be specified by separating them with whitespace PermitOpen *:* # Default PermitOpen host:port PermitOpen none
* еҰӮжһң User жңүеҫ— shell access, йӮЈ PermitOpen йҷҗеҲ¶еҪўеҗҢиҷӣиЁӯ, еӣ зӮә User еҸҜд»Ҙз”Ё rinetd
P.S.
AllowTcpForwarding yes(Default) | no | local | remote |
local: to allow local
remote: to allow remote forwarding only
![йҰ–й Ғ Logo ¶гБВ Keith і]ӯp !!](/themes/mytheme/logo.png)