жңҖеҫҢжӣҙж–°: 2019-08-10
зӣ®йҢ„
- mstsc.exe full path
- Check RDP Usage
- Sent "Ctrl + Alt + Del"
- reboot & shutdown
- Other Hotkey
- иЁӯе®ҡ idle жҷӮзҡ„ timeout
- Change the TCP Port
- Account Policies Policy
- RD - Disable Administrator Login
- Security Log in Event Viewer does not store IPs
- з¶Іи·ҜеұӨзҙҡй©—иӯү
- Console Session
- Restart RDP without rebooting windows
- RDP Version
- SecurityLayer Setting
- Win 7 & S08r2 иҪү DPI (Windows6.1-KB2726399-v3-x64.msu)
- RD еӨҡй–Ӣ - rdpwrap
RD Client(mstsc.exe) full path
%WINDIR%\system32\mstsc.exe
Check RDP Usage
qwinsta
SESSIONNAME USERNAME ID STATE TYPE DEVICE services 0 Disc >console tim 10 Active rdp-tcp 65536 Listen
Sent "Ctrl + Alt + Del"
CRTL+ALT+END
To use the Ctrl-Alt-Insert combo in Microsoft RDP
perform the following configuration:
1. Open the Remote Desktop Connection utility.
2. Click Options.
3. Open the Local Resources tab.
4. Change the value for Apply Windows key combinations option under Keyboard to On the remote computer.
All key combinations are sent to the remote desktop connection.
reboot & shutdown
[ж–№жі•1] hotkey
Alt + F4
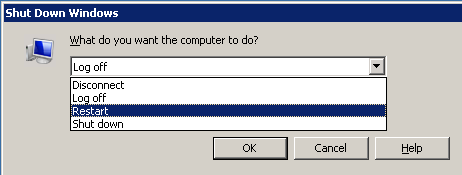
[ж–№жі•2] CMD
# е»әз«Ӣ shortcut
%WINDIR%\System32\shutdown.exe /t 10 /r /f /c "reboot by shortcut"
Other Hotkey
CTRL+ALT+BREAK е…Ёиһўе№•жЁЎејҸд№Ӣй–“еҲҮжҸӣ
иЁӯе®ҡ idle жҷӮзҡ„ timeout
Terminal Server:
Connection Object:
tscc.msc -> right-click RDP-Tcp -> Properties -> Sessions tab
gpedit.msc
Local Computer Policy\Computer Configuration\Administrative Templates\Windows Components\Terminal Services\Sessions
XP:
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows NT\terminal services\MaxIdleTime
Server08 R2
Administrative Tools -> Terminal Services -> "Remote Desktop Session Host Configuration"
* Timeout and reconnection settings configured by using "Remote Desktop Session Host Configuration"
it will take precedence over timeout and reconnection settings that have been configured for a specific user account.
Win7:
Computer Configuration -> Administrative Templates -> Windows Components -> Remote Desktop Services ->
Remote Desktop Session Host -> Session Time Limits
зӮәдҪҝз”ЁдёӯдҪҶй–’зҪ®зҡ„йҒ з«ҜжЎҢйқўжңҚеӢҷе·ҘдҪңйҡҺж®өиЁӯе®ҡжҷӮй–“йҷҗеҲ¶
- дҪҝз”ЁиҖ…жңғеңЁе·ҘдҪңйҡҺж®өдёӯж–·йҖЈз·ҡеүҚе…©еҲҶйҗҳ收еҲ°иӯҰе‘ҠиЁҠжҒҜ
- еҒңз”Ё => з„ЎйҷҗжңҹдҝқжҢҒдҪҝз”ЁдёӯдҪҶй–’зҪ®зӢҖж…Ӣ
When session limit is reached or connection is broken:
- Disconnect - To disconnect the user from the session, allowing the session to be reconnected
- End session - Any running applications are forced to shut down, which can result in loss of data at the client
Session timeout for a domain user account
[1] For a domain user account
"Active Directory Users and Computers" -> double-click USERNAME -> Sessions tab
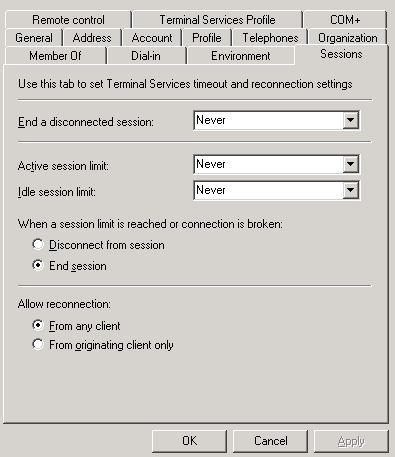
End a disconnected session
Amount of time that a disconnected user session is kept active on the RD Session Host server.
When a session is in a disconnected state, running programs are kept active.
Idle session limit
amount of time that an active Remote Desktop Services session can be idle (without user input)
before the session is automatically disconnected or ended.
When a session limit is reached or connection is broken
Specify whether to disconnect or end the user's Remote Desktop Services session
when an active session limit or an idle session limit is reached.
[2] Group Policies
gpedit.msc
Computer Configuration, Administrative Templates, Windows Components, Terminal Services, Sessions
[3] Terminal Services Configuration
Connections -> Properties
Change the TCP Port
HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp\PortNumber
Listen еӨҡеҖӢ Port
OS Window 7
1. Export the following key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Contro l\Terminal Server\WinStations\RDP-Tcp
2. Edit the REG file
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Contro l\Terminal Server\WinStations\RDP-Tcp\ "PortNumber"=dword:0000d3d
TO
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Contro l\Terminal Server\WinStations\RDP-Tcp-33389
"PortNumber"=dword:000826D# 33389 = 000826D
3. Double click REG file to import
* дёҚз”Ё reboot !!
Testing
netstat -n -l -p tcp
Remark
еңЁ S2008 зҡ„ TS дёҠжҷӮ, иҰҒдәәжүӢ Stop / Start "RDP-Tcp-33389" Service дёҖж¬Ў
Account Policies Policy
Account Policies -> Account Lockout Policy
Account lockout threshhold - 0 = administrator explicitly unlocks it
Reset account lockout counter after - minutes that must elapse after a failed logon
Account lockout duration
A successful authentication resets the failed attempts counter
HKLM\SYSTEM\CurrentControlSet\Services\RemoteAccess\Parameters\AccountLockout
MaxDenials
The maximum number of failed attempts before the account is locked out.
ResetTime (mins)
Manually resetting an account that is locked out
registry subkey for the user account is deleted.
RD - Disable Administrator Login
Workgroup Solution:
- Right-click on Computer and select Properties
- Advanced System Properties
- Adds the user to the Remote Desktop Users group
AD:
Administrative Tools -> Local Security Policy -> Local Policies -> User Rights Assignment
"Allow log on through Remote Desktop Services"
Open the Allow log on through Remote Desktop Services policy and remove the Administrators item.
Security Log in Event Viewer does not store IPs
Introducing TLS/SSL as Remote Desktop authentification, Windows does not log the source IP address of the failed login anymore. Within the event log you will just find the audit failure 4625 with NULL SID and no IP address.
Configure the Terminal Services
"Terminal Services Configuration Tools"
Connections -> RDP-Tcp -> Properties
General tab -> Security Layer
Available security layers
SSL (TLS 1.0) SSL (TLS 1.0)
will be used for server authentication and for encrypting all data transferred between the server and the client.
Negotiate
The most secure layer that is supported by the client will be used. If supported, SSL (TLS 1.0) will be used. If the client does not support SSL (TLS 1.0), the RDP Security Layer will be used. This is the default setting.
RDP Security Layer
Communication between the server and the client will use native RDP encryption. If you select RDP Security Layer, you cannot use Network Level Authentication.
By default, RD Session Host sessions use native RDP encryption. However, RDP does not provide authentication to verify the identity of an RD Session Host server. You can enhance the security of RD Session Host sessions by using Secure Sockets Layer (SSL) Transport Layer Security (TLS 1.0) for server authentication and to encrypt RD Session Host communications.
-----
How to identify the attacker and to protect your system even when the Windows event 4625 does not show an IP address
Install Cyberarms Intrusion Detection (IDDS), enable the TLS/SSL security agent, and you'll be fine. IDDS monitors network connections and locks out attackers before they are able to break in.
-----
This is a feature of TLS/SSL encryption of remote desktop. Using the RDP encryption instead (original protocol encryption) you will see all of the IP addresses in 4625 audit messages.
-----
Computer Configuration\Windows Settings\Security Settings\Security Options
Network security: LAN Manager authentication level -- Send NTLMv2 response only. Refuse LM & NTLM
Network security: Restrict NTLM: Audit Incoming NTLM Traffic -- Enable auditing for all accounts
Network security: Restrict NTLM: Incoming NTLM traffic -- Deny all accounts
Recommended
Do not allow for passwords to be saved -- Enabled
Prompt for credentials on the client computer -- Enabled
Event Log
еёёиҰӢ:
21: е·ҘдҪңйҡҺж®өзҷ»е…ҘжҲҗеҠҹ
23: е·ҘдҪңйҡҺж®өзҷ»еҮәжҲҗеҠҹ
24: е·ҘдҪңйҡҺж®өе·Ідёӯж–·йҖЈз·ҡ
25: е·ҘдҪңйҡҺж®өйҮҚж–°йҖЈз·ҡжҲҗеҠҹ
з¶Іи·ҜеұӨзҙҡй©—иӯү
Server 2012 R2 Default жңүз¶Іи·ҜеұӨзҙҡй©—иӯү
жүҖд»Ҙ XP дёҚиғҪйҖЈе®ғ, еҰӮжһңжғійҖЈ, йӮЈе°ұиҰҒй—ңй–ү"з¶Іи·ҜеұӨзҙҡй©—иӯү"
Steps
1. gpedit.msc
2. йӣ»и…ҰиЁӯе®ҡпјҸзі»зөұз®ЎзҗҶзҜ„жң¬пјҸWindows е…ғ件пјҸйҒ з«ҜжЎҢйқўжңҚеӢҷпјҸйҒ з«ҜжЎҢйқўе·ҘдҪңйҡҺж®өдё»ж©ҹпјҸе®үе…ЁжҖ§
йҖҸйҒҺдҪҝз”Ёз¶Іи·ҜеұӨзҙҡй©—иӯүд»ҘиҰҒжұӮе°ҚйҒ з«ҜйҖЈз·ҡйҖІиЎҢдҪҝз”ЁиҖ…й©—иӯү <- иЁӯжҲҗ(е·ІеҒңз”Ё)
SecurityLayer Setting
HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp\
SecurityLayer(DWORD)
0 RDP
1 Negotiate
2 SSL
RDP:
еңЁ Window з•«йқў Login
The RDP method uses native RDP encryption to secure communications between the client and RD Session Host server.
If you select this setting, the RD Session Host server is not authenticated.
Native RDP encryption (as opposed to SSL encryption) is not recommended.
Negotiate:
If TLS is not supported, native Remote Desktop Protocol (RDP) encryption is used to secure communications,
but the RD Session Host server is not authenticated.
SSL:
The SSL method requires the use of TLS to authenticate the RD Session Host server.
Encryption level(DWORD)
MinEncryptionLevel
1: low security level
2: encrypted at the maximum key strength supported by the client.
3: high security level
4: maximum security
Restart RDP without rebooting windows
[ж–№жі•1]
tasklist /svc | findstr TermService
svchost.exe 1064 TermService
# иў« kill еҫҢе®ғжңғиҮӘеӢ• restart зҡ„
taskkill /F /PID 1064
svchost.exe 7568 TermService
еҰӮжһңжІ’жңү start, йӮЈе°ұдәәжүӢ start е®ғ
sc \\127.0.0.1 start TermService
[ж–№жі•2]
net stop TermService
net start TermService
Console Session
mstsc -console IP
RDP Version
Windows XP SP3 + KB969084 (
RDP verion жңғеҚҮзҙҡеҲ° 7.0, дҪҶдёҚж”ҜжҸҙ"з¶Іи·ҜеұӨзҙҡй©—иӯү"
RemoteFX
еңЁ VM е…§з”ЁеҲ° Graphic еҚЎиіҮжәҗ
- VM Guest: еҠ HW: RemoteFX 3D иҰ–иЁҠеҚЎ (dxdiag ( жңғиҰӢеҲ°жүҖжңүеҠ йҖҹйғҪе•ҹз”ЁдәҶ))
- VM Host: Hyper-V (йҒ з«ҜжЎҢйқўиҷӣ擬主ж©ҹ)
Windows virtual desktops
Remote Desktop Virtualization Host is new to R2 and installs on the Hyper-V box,
monitoring and preparing VMs as directed by the RD Connection Broker.
When you install Remote Desktop Virtualization Host on a server,
Hyper-V will be installed if not already present.
Delivered as part of S2008 R2 SP1
It allows the end user to work remotely
- Windows Aero desktop environment,
- watch videos (RemoteFX Calista Codec)
- run 3D applications (provides VMs with access to the physical GPU)
- redirecting USB devices into Windows 7 VMs
Client computers
RDP >= 8.0
l3codeca.acm error
Win7 event log 6281
Code Integrity determined that the page hashes of an image file are not valid.
The file could be improperly signed without page hashes or corrupt due to unauthorized modification.
The invalid hashes could indicate a potential disk device error.
File Name: \Device\HarddiskVolume2\Windows\System32\l3codeca.acm
l3codeca.acm ?
l3codeca.acm, l3codecp.acm= MPEG Layer-3 Audio Codec for MSACM
An acm codec is a kind of program that works almost like a DLL.
l3codeca.acm # advanced version (free, but low bitrates)
l3codecp.acm # professional version
иӘӘжҳҺ
when audio is redirected to the client and we load audiodg.exe,
it enumerates the codecs to get information from them.
Not all codecs are signed to load in a protected process and
if they are not this error is generated.
audiodg.exe (Win 7)
е®ғжҳҜ Windows йҹій »иЁӯеӮҷең–еҪўйҡ”йӣўйҖІзЁӢ
Win 7 & S08r2 иҪү DPI (Windows6.1-KB2726399-v3-x64.msu)
# Windows 7 or Server 2008 R2
"еҸі click > display" settings can't be changed DPI from a RDP session
е®үиЈқ Windows6.1-KB2726399-v3-x64.msu patch еҫҢе°ұеҸҜд»Ҙи®ҠжӣҙдәҶ.
![йҰ–й Ғ Logo ¶гБВ Keith і]ӯp !!](/themes/mytheme/logo.png)